Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CyberOps Associate 200-201 Questions and answers with ExamsMirror
Exam 200-201 Premium Access
View all detail and faqs for the 200-201 exam
750 Students Passed
93% Average Score
98% Same Questions
Refer to the exhibit.
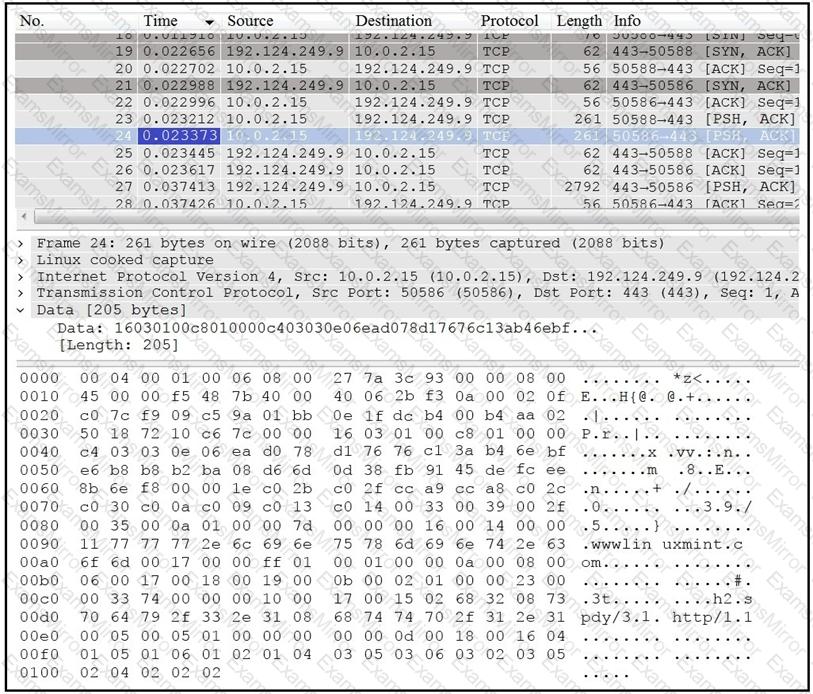
Which application protocol is in this PCAP file?
Refer to the exhibit.
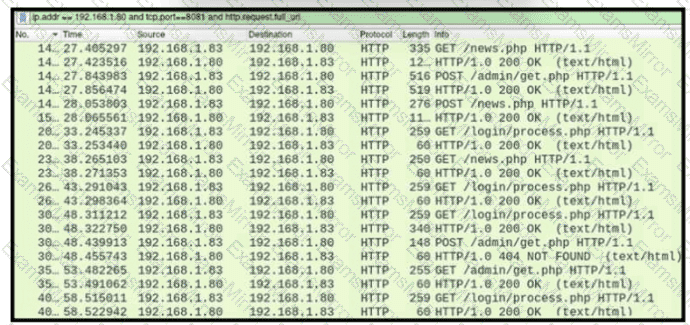
A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?
Which action matches the weaponization step of the Cyber Kill Chain model?

Refer to the exhibit. The figure shows an X 509 certificate. Which field represents the digital cryptographic algorithm used by the issuer to sign the certificate?
An engineer is working on the implementation of digital certificates for new cntical web applications One of the requirements is that the https connection must be validated and protected against malicious network impersonators The server will be exposed externally from the DMZ network Which certificate must be used?
Which type of evasion technique is accomplished by separating the traffic into smaller segments before transmitting across the network?
What is the difference between statistical detection and rule-based detection models?
How can TOR impact data visibility inside an organization?
Why is encryption challenging to security monitoring?
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
