Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CyberOps Professional 350-201 Questions and answers with ExamsMirror
Exam 350-201 Premium Access
View all detail and faqs for the 350-201 exam
669 Students Passed
96% Average Score
97% Same Questions
Refer to the exhibit.
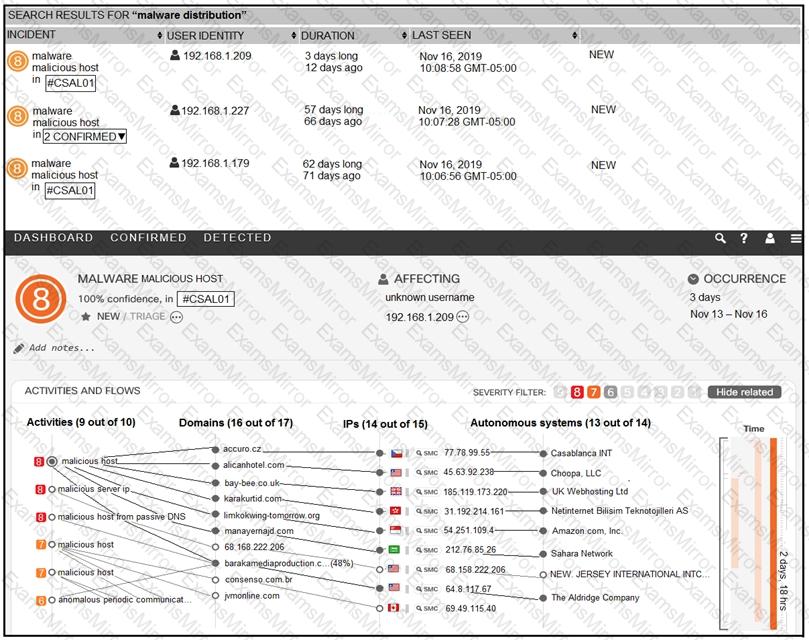
For IP 192.168.1.209, what are the risk level, activity, and next step?
What do 2xx HTTP response codes indicate for REST APIs?
An employee who often travels abroad logs in from a first-seen country during non-working hours. The SIEM tool generates an alert that the user is forwarding an increased amount of emails to an external mail domain and then logs out. The investigation concludes that the external domain belongs to a competitor. Which two behaviors triggered UEBA? (Choose two.)
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server. Which security solution is needed at this stage to mitigate the attack?
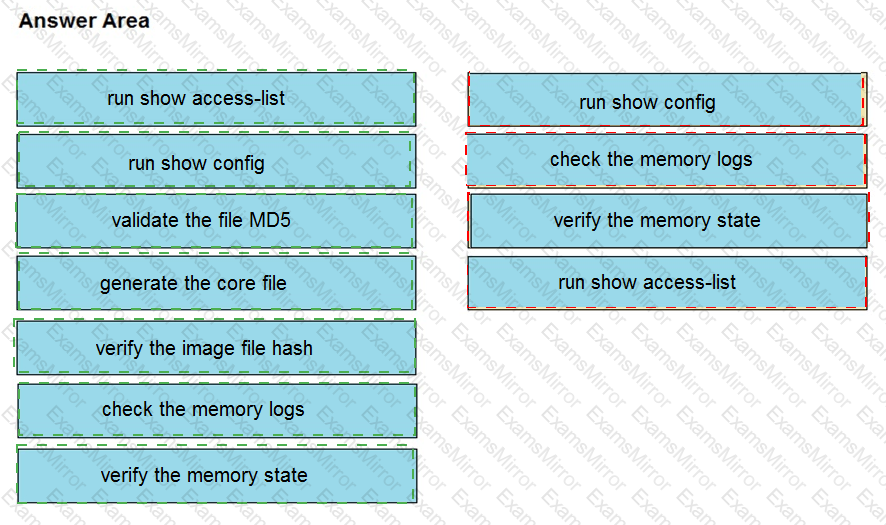
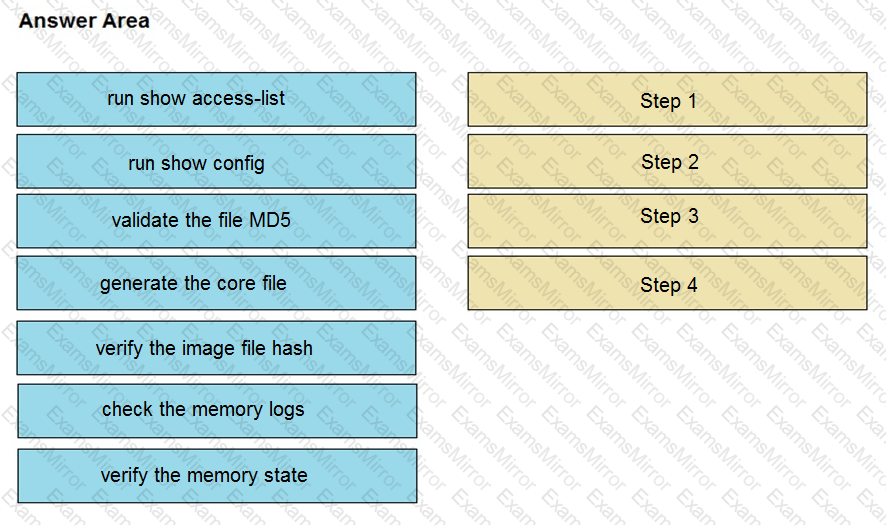
An organization lost connectivity to critical servers, and users cannot access business applications and internal websites. An engineer checks the network devices to investigate the outage and determines that all devices are functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not all options are used.
Refer to the exhibit.
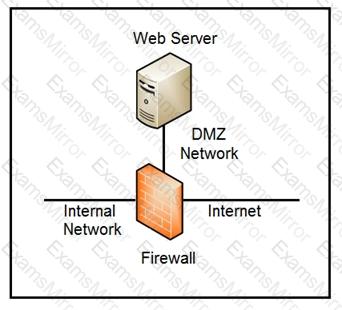
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company’s confidential document management folder using a company- owned asset al039-ice-4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected is from different departments. What are the actions a security manager should take?
Where do threat intelligence tools search for data to identify potential malicious IP addresses, domain names, and URLs?
Refer to the exhibit.
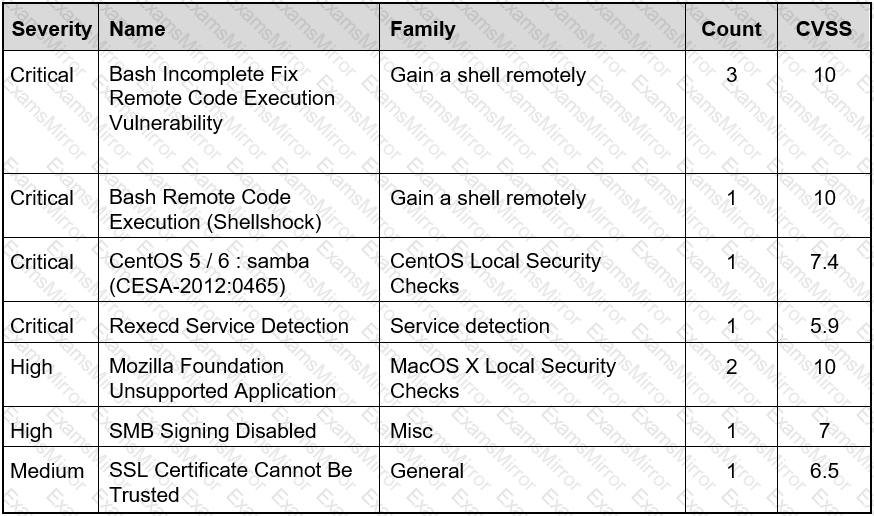
Based on the detected vulnerabilities, what is the next recommended mitigation step?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.