Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the CIW Web Security Associate 1D0-571 Questions and answers with ExamsMirror
Exam 1D0-571 Premium Access
View all detail and faqs for the 1D0-571 exam
745 Students Passed
85% Average Score
96% Same Questions
What is the primary use of hash (one-way) encryption in networking?
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
Which of the following is the most likely first step to enable a server to recover from a denial-of-service attack in which all hard disk data is lost?
You are using a PKI solution that is based on Secure Sockets Layer (SSL). Which of the following describes the function of the asymmetric-key-encryption algorithm used?
Which of the following applications can help determine whether a denial-of-service attack is occurring against a network host?
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
You have determined that an attack is currently underway on your database server. An attacker is currently logged in, modifying data. You want to preserve logs, caching and other data on this affected server. Which of the following actions will best allow you to stop the attack and still preserve data?
At the beginning of an IPsec session, which activity occurs during the Internet Key Exchange (IKE)?
Consider the following image:
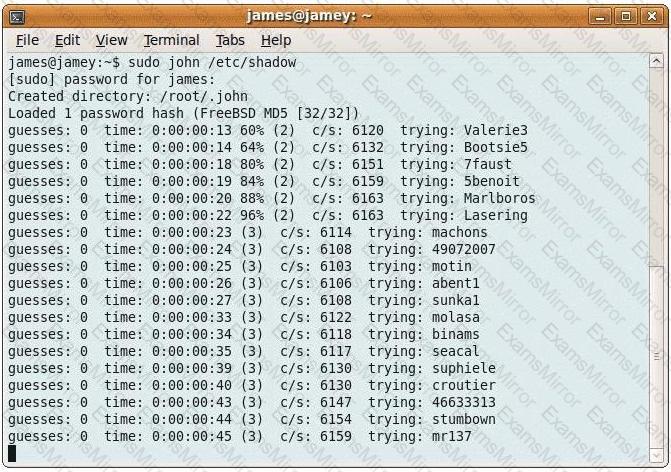
From the information in this image, what type of attack is occurring?
What is the first tool needed to create a secure networking environment?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
