Weekend Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the CrowdStrike Falcon Certification Program CCFH-202 Questions and answers with ExamsMirror
Exam CCFH-202 Premium Access
View all detail and faqs for the CCFH-202 exam
409 Students Passed
94% Average Score
97% Same Questions
What do you click to jump to a Process Timeline from many pages in Falcon, such as a Hash Search?
Which field in a DNS Request event points to the responsible process?
How do you rename fields while using transforming commands such as table, chart, and stats?
The help desk is reporting an increase in calls related to user accounts being locked out over the last few days. You suspect that this could be an attack by an adversary against your organization. Select the best hunting hypothesis from the following:
Which of the following is an example of actor actions during the RECONNAISSANCE phase of the Cyber Kill Chain?
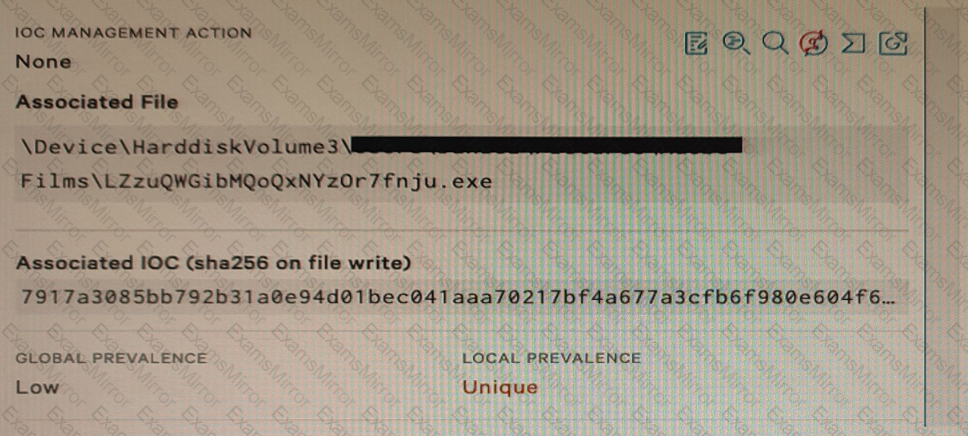
Falcon detected the above file attempting to execute. At initial glance; what indicators can we use to provide an initial analysis of the file?
You are reviewing a list of domains recently banned by your organization's acceptable use policy. In particular, you are looking for the number of hosts that have visited each domain. Which tool should you use in Falcon?
An analyst has sorted all recent detections in the Falcon platform to identify the oldest in an effort to determine the possible first victim host What is this type of analysis called?
Which of the following queries will return the parent processes responsible for launching badprogram exe?
To find events that are outliers inside a network,___________is the best hunting method to use.
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
