Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the CyberArk Defender EPM-DEF Questions and answers with ExamsMirror
Exam EPM-DEF Premium Access
View all detail and faqs for the EPM-DEF exam
733 Students Passed
97% Average Score
93% Same Questions
What is required to configure SAML authentication on EPM?
An EPM Administrator needs to create a policy to allow the MacOS developers elevation to an application. What type of policy should be used?
If you want to diagnose agent EPM agent connectivity issues, what is the agent executable that can be used from the command line?
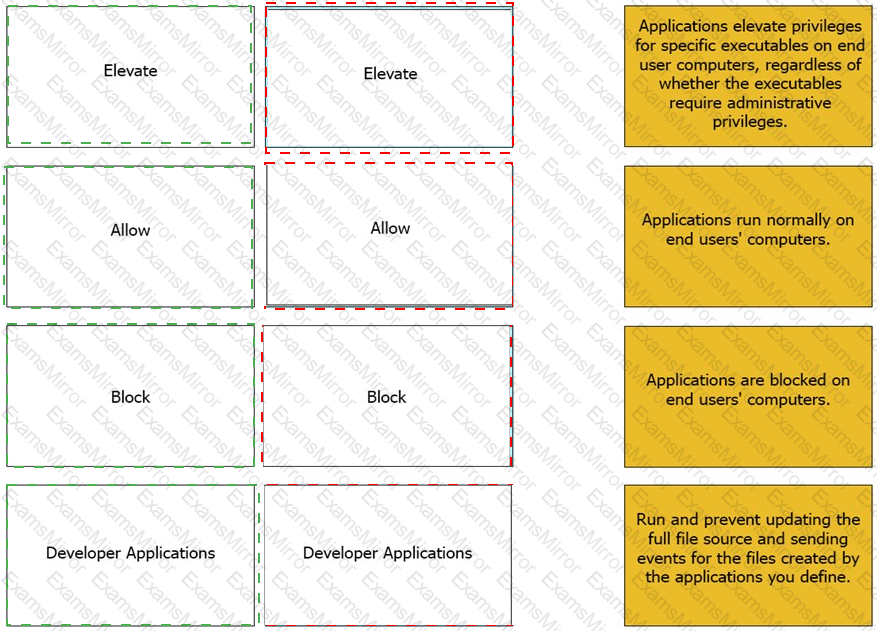
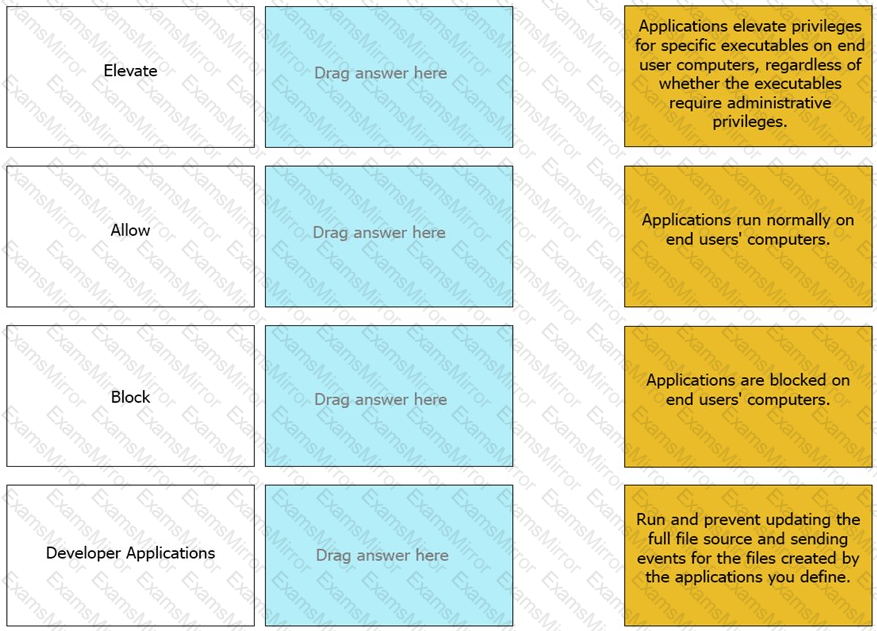
Match the Application Groups policy to their correct description.
An end user is experiencing performance issues on their device after the EPM Agent had been installed on their machine. What should the EPM Administrator do first to help resolve the issue?
CyberArk's Privilege Threat Protection policies are available for which Operating Systems? (Choose two.)
How does EPM help streamline security compliance and reporting?
Where can you view CyberArk EPM Credential Lures events?
A Helpdesk technician needs to provide remote assistance to a user whose laptop cannot connect to the Internet to pull EPM policies. What CyberArk EPM feature should the Helpdesk technician use to allow the user elevation capabilities?
When deploying Ransomware Protection, what tasks should be considered before enabling this functionality? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.