Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the CyberArk Secrets Manager SECRET-SEN Questions and answers with ExamsMirror
Exam SECRET-SEN Premium Access
View all detail and faqs for the SECRET-SEN exam
624 Students Passed
96% Average Score
95% Same Questions
Which statement is correct about this message?
Message: “[number-of-deleted-rows] rows has successfully deleted “CEADBR009D Finished vacuum”?
You are deploying Kubernetes resources/objects as Conjur identities.
In addition to Namespace and Deployment, from which options can you choose? (Choose two.)
What does “Line of business (LOB)” represent?
When attempting to configure a Follower, you receive the error:
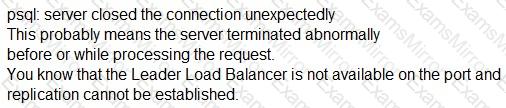
Which port is the problem?
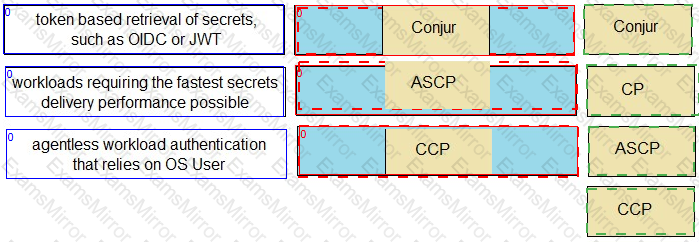
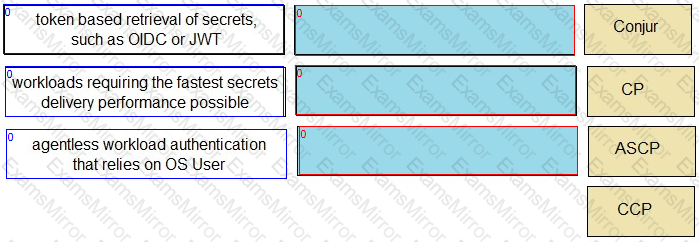
Match each scenario to the appropriate Secrets Manager solution.
Refer to the exhibit.
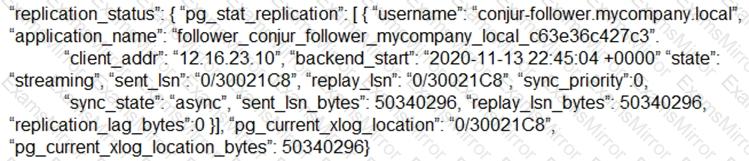
How can you confirm that the Follower has a current copy of the database?
How many Windows and Linux servers are required for a minimal Conjur deployment that integrates with an existing CyberArk PAM Vault environment, supports high availability, and is redundant across two geographically disparate regions?
A customer wants to ensure applications can retrieve secrets from Conjur in three different data centers if the Conjur Leader becomes unavailable. Conjur Followers are already deployed in each of these data centers.
How should you architect the solution to support this requirement?
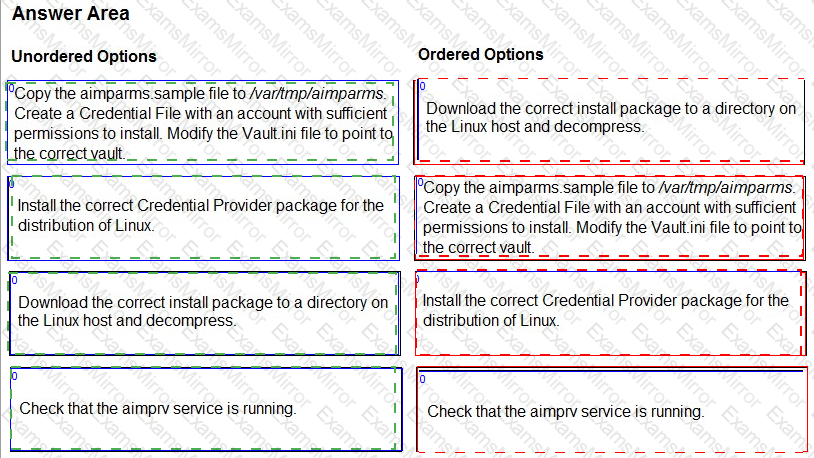
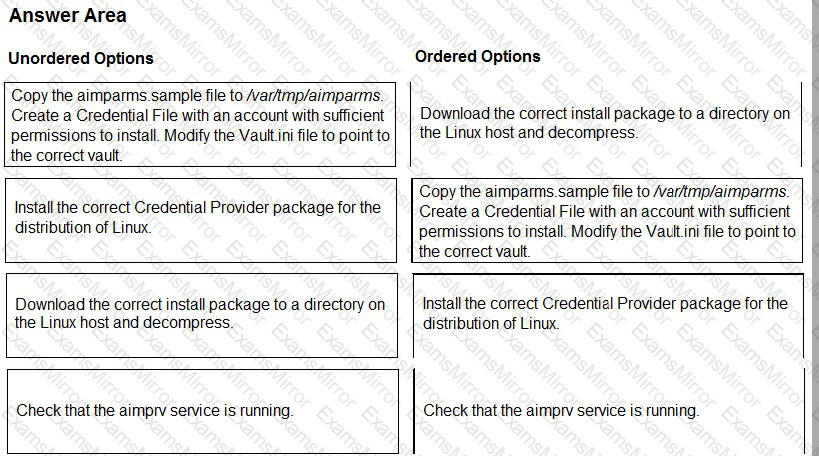
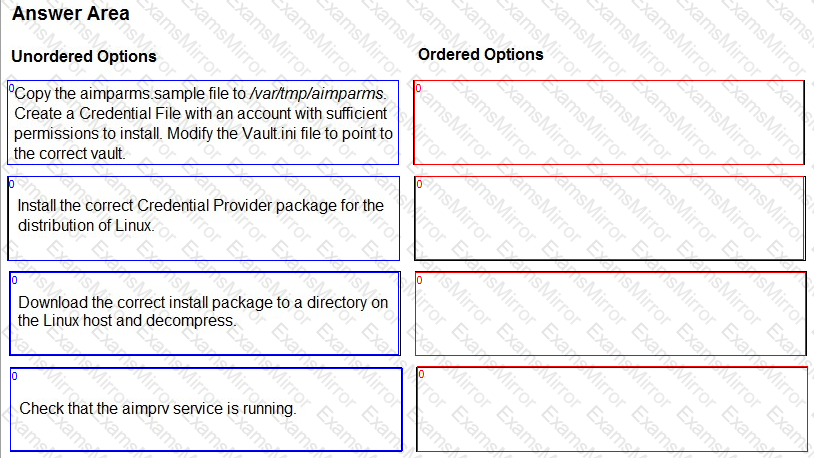
You are installing a Credential Provider on a Linux host. Arrange the installation steps in the correct sequence.
When using the Seed Fetcher to deploy Kubernetes Followers, an error occurs in the Seed Fetcher container. You check the logs and discover that although the Seed Fetcher was able to authenticate, it shows a 500 error in the log and does not successfully retrieve a seed file. What is the cause?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.