Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the ECCouncil Certification 312-49 Questions and answers with ExamsMirror
Exam 312-49 Premium Access
View all detail and faqs for the 312-49 exam
616 Students Passed
94% Average Score
92% Same Questions
Which part of Metasploit framework helps users to hide the data related to a previously deleted file or currently unused by the allocated file.
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
Which of the following acts as a network intrusion detection system as well as network intrusion prevention system?
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years.
You navigate to archive. org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code. While searching through the code, you come across something abnormal: What have you found?
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company PBX system be called?
Which of the following tool enables data acquisition and duplication?
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
James is testing the ability of his routers to withstand DoS attacks. James sends ICMP ECHO requests to the broadcast address of his network. What type of DoS attack is James testing against his network?
Pagefile.sys is a virtual memory file used to expand the physical memory of a computer. Select the registry path for the page file:
Shane has started the static analysis of a malware and is using the tool ResourcesExtract to find more details of the malicious program. What part of the analysis is he performing?
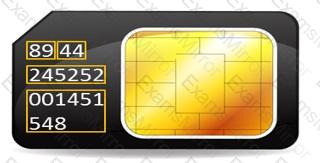
During an investigation, Noel found the following SIM card from the suspect's mobile. What does the code 89 44 represent?
Depending upon the jurisdictional areas, different laws apply to different incidents. Which of the following law is related to fraud and related activity in connection with computers?
Which of the following Windows-based tool displays who is logged onto a computer, either locally or remotely?
Which of the following options will help users to enable or disable the last access time on a system running Windows 10 OS?
A picture file is recovered from a computer under investigation. During the investigation process, the file is enlarged 500% to get a better view of its contents. The picture quality is not degraded at all from this process. What kind of picture is this file. What kind of picture is this file?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
