Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the ECCouncil CHFI v10 312-49v10 Questions and answers with ExamsMirror
Exam 312-49v10 Premium Access
View all detail and faqs for the 312-49v10 exam
758 Students Passed
87% Average Score
94% Same Questions
When is it appropriate to use computer forensics?
Which of the following files gives information about the client sync sessions in Google Drive on Windows?
Heather, a computer forensics investigator, is assisting a group of investigators working on a large computer fraud case involving over 20 people. These 20 people, working in different offices, allegedly siphoned off money from many different client accounts. Heather responsibility is to find out how the accused people communicated between each other. She has searched their email and their computers and has not found any useful evidence. Heather then finds some possibly useful evidence under the desk of one of the accused.
In an envelope she finds a piece of plastic with numerous holes cut out of it. Heather then finds the same exact piece of plastic with holes at many of the other accused peoples desks. Heather believes that the 20 people involved in the case were using a cipher to send secret messages in between each other. What type of cipher was used by the accused in this case?
Why should you never power on a computer that you need to acquire digital evidence from?
Paul is a computer forensics investigator working for Tyler & Company Consultants. Paul has been called upon to help investigate a computer hacking ring broken up by the local police. Paul begins to inventory the PCs found in the hackers hideout. Paul then comes across a PDA left by them that is attached to a number of different peripheral devices. What is the first step that Paul must take with the PDA to ensure the integrity of the investigation?
During an investigation, an employee was found to have deleted harassing emails that were sent to someone else. The company was using Microsoft Exchange and had message tracking enabled. Where could the investigator search to find the message tracking log file on the Exchange server?
When a user deletes a file or folder, the system stores complete path including the original filename is a special hidden file called “INFO2” in the Recycled folder. If the INFO2 file is deleted, it is recovered when you ______________________.
Which of the following standard represents a legal precedent sent in 1993 by the Supreme Court of the United States regarding the admissibility of expert witnesses’ testimony during federal legal proceedings?
Which of the following tool can the investigator use to analyze the network to detect Trojan activities?
Which of the following commands shows you all of the network services running on Windows-based servers?
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive?
22,164 cylinders/disk
80 heads/cylinder
63 sectors/track
In the following directory listing,
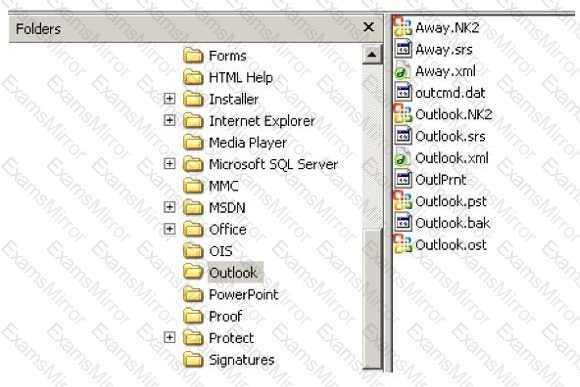
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
Which code does the FAT file system use to mark the file as deleted?
What stage of the incident handling process involves reporting events?
What will the following command accomplish?
dd if=/dev/xxx of=mbr.backup bs=512 count=1
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
