Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the ECCouncil ECSA 412-79v10 Questions and answers with ExamsMirror
Exam 412-79v10 Premium Access
View all detail and faqs for the 412-79v10 exam
663 Students Passed
96% Average Score
97% Same Questions
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum.
Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.

Which of the following ICMP messages will be generated if the destination port is not reachable?
From where can clues about the underlying application environment can be collected?
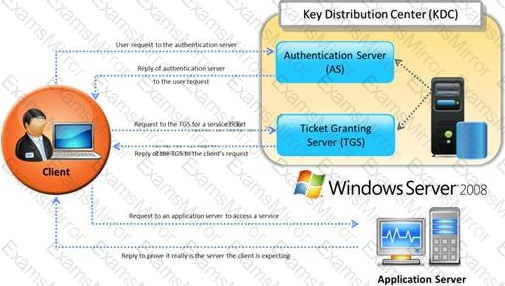
Identify the type of authentication mechanism represented below:
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
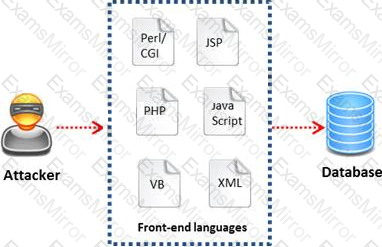
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.
In the example of a /etc/shadow file below, what does the bold letter string indicate?
Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
