Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the EMC DECS DES-9131 Questions and answers with ExamsMirror
Exam DES-9131 Premium Access
View all detail and faqs for the DES-9131 exam
770 Students Passed
91% Average Score
90% Same Questions
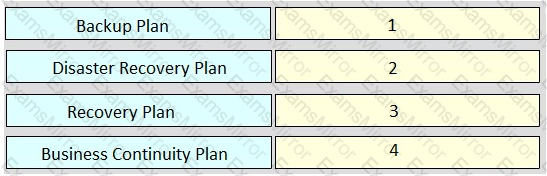
Rank order the relative severity of impact to an organization of each plan, where “1” signifies the most impact and “4” signifies the least impact.
Assume that a DDoS attack has been occurring for 72 minutes. What determines who talks to external
stakeholders?
What does a security benchmark help define?
Which NIST Cybersecurity Framework function should be executed before any others?
When should event analysis be performed?
A security engineer is responsible for monitoring company software, firmware, system OS, and applications for known vulnerabilities. How should they stay current on exploits and information security?
What is part of the Pre-Recovery phase?
What is the main goal of a gap analysis in the Identify function?
What should an organization use to effectively mitigate against password sharing to prevent unauthorized
access to systems?
You have been tasked with documenting mission critical procedures of an organization that need to be
sustained through a significant disruption.
What document would you develop?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.