Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Public Cloud Security FCP_FML_AD-7.4 Questions and answers with ExamsMirror
Exam FCP_FML_AD-7.4 Premium Access
View all detail and faqs for the FCP_FML_AD-7.4 exam
584 Students Passed
91% Average Score
98% Same Questions
Refer to the exhibit, which shows a topology diagram of two MTAs.
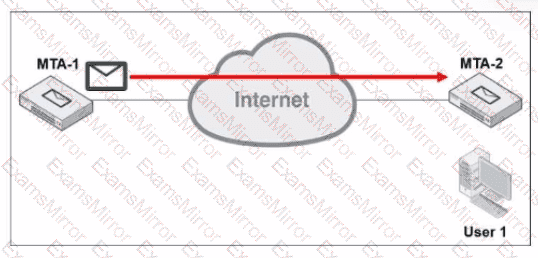
MTA-1 is delivering an email intended for User 1 to MTA-2. User 1 uses Outlook as an email client. Which two statements about protocol usage between these devices are correct? (Choose two.)
Refer to the exhibit, which shows a partial antispam profile configuration.
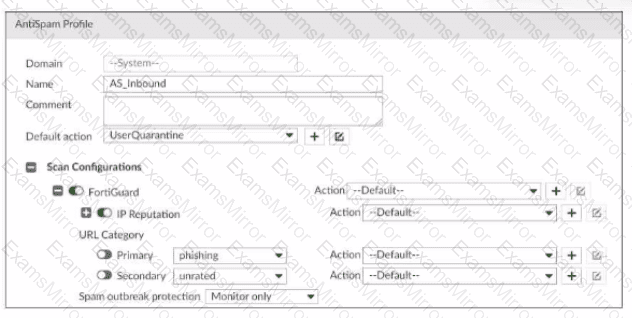
What will happen to an email that triggers Spam outbreak protection?
Refer to the exhibit, which displays the domain configuration of a FortiMail device running in transparent mode.
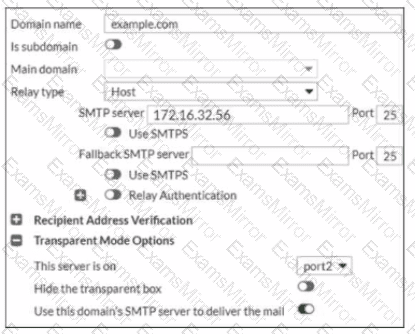
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
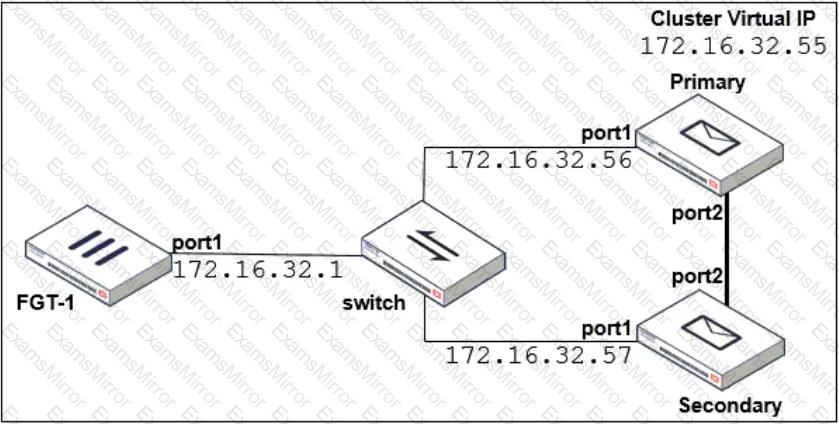
Which IP address must the DNS MX record for this organization resolve to?
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
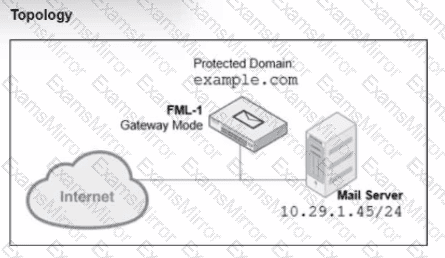

Refer to the exhibits, which show a topology diagram (Topology) and a configuration element (IP Policy).
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the mail server starts filling up with undeliverable email.
Which two changes must theadministrator make to fix this issue? (Choose two.)
Which three configuration steps must you set to enable DKIM signing for outbound messages on FortiMail? (Choose three.}
Exhibit.
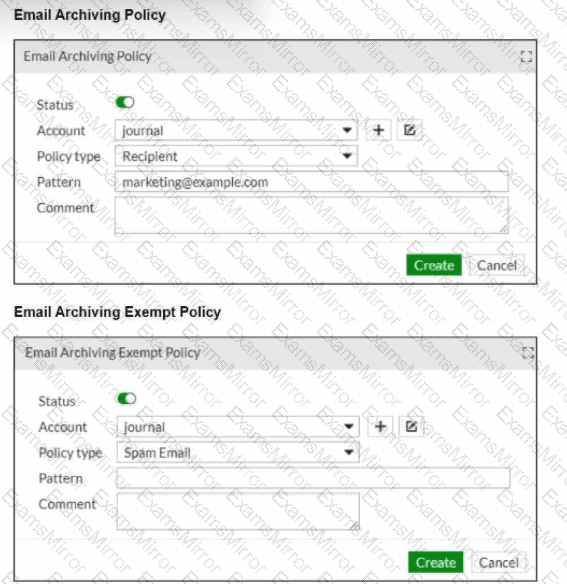
Refer to the exhibits, which show an email archiving configuration (Email Archiving 1 and Email Archiving 2) from a FortiMail device.
What two archiving actions will FortiMail take when email messages match these archive policies? (Choose two.)
Refer to the exhibit, which displays a history log entry.
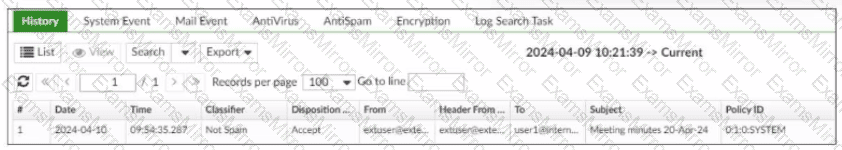
In the Policy ID column, why isthe last policy ID value SYSTEM?
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs werenotgenerated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
