Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Professional Security Operations FCP_FSM_AN-7.2 Questions and answers with ExamsMirror
Exam FCP_FSM_AN-7.2 Premium Access
View all detail and faqs for the FCP_FSM_AN-7.2 exam
693 Students Passed
89% Average Score
97% Same Questions
What can you use to send data to FortiSIEM for user and entity behavior analytics (UEBA)?
Refer to the exhibit.
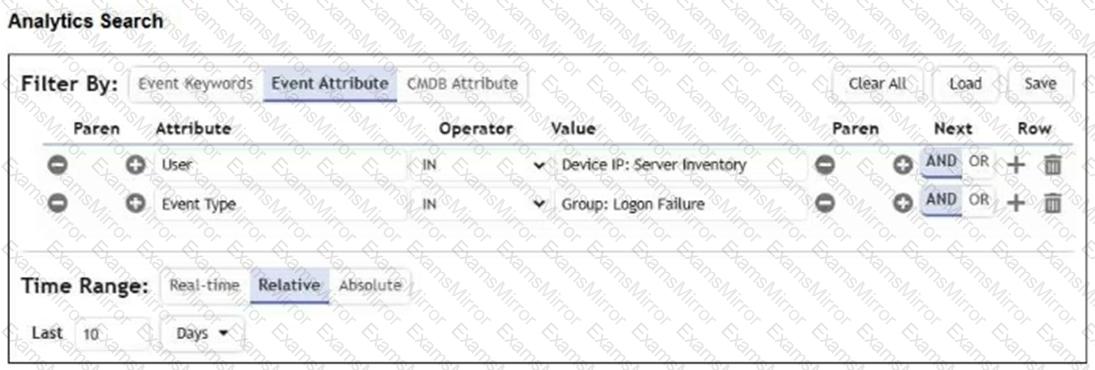
The analyst is troubleshooting the analytics query shown in the exhibit.
Why is this search not producing any results?
How can you query the configuration management database (CMDB) in an analytics search?
Refer to the exhibit.
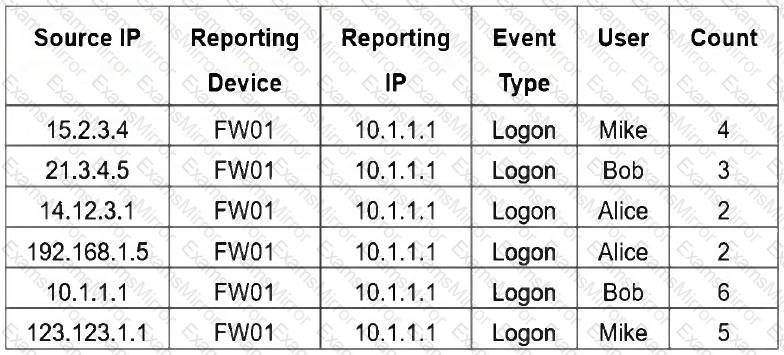
If you group the events by User, Source IP, and Count attributes, how many results will FortiSIEM display?
Refer to the exhibit.
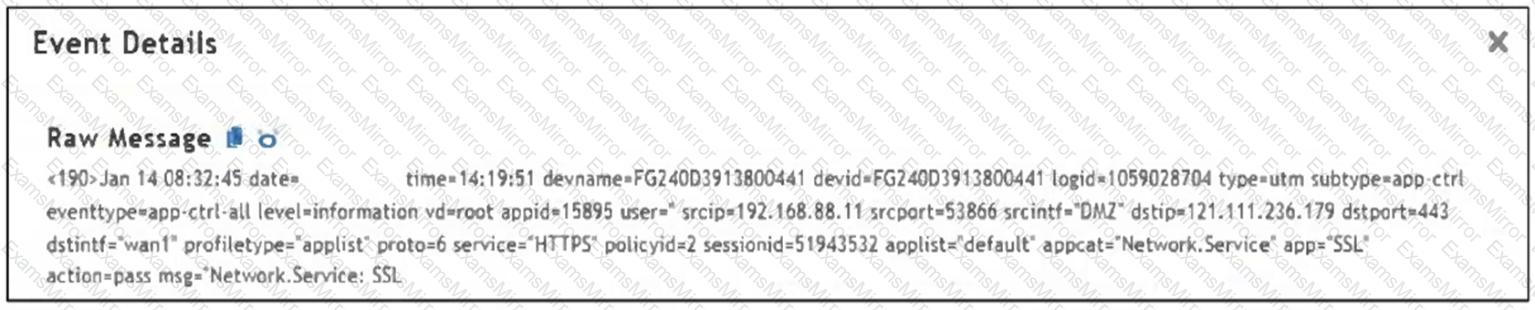
Which value would you expect the FortiSIEM parser to use to populate the Application Name field?
Refer to the exhibit.
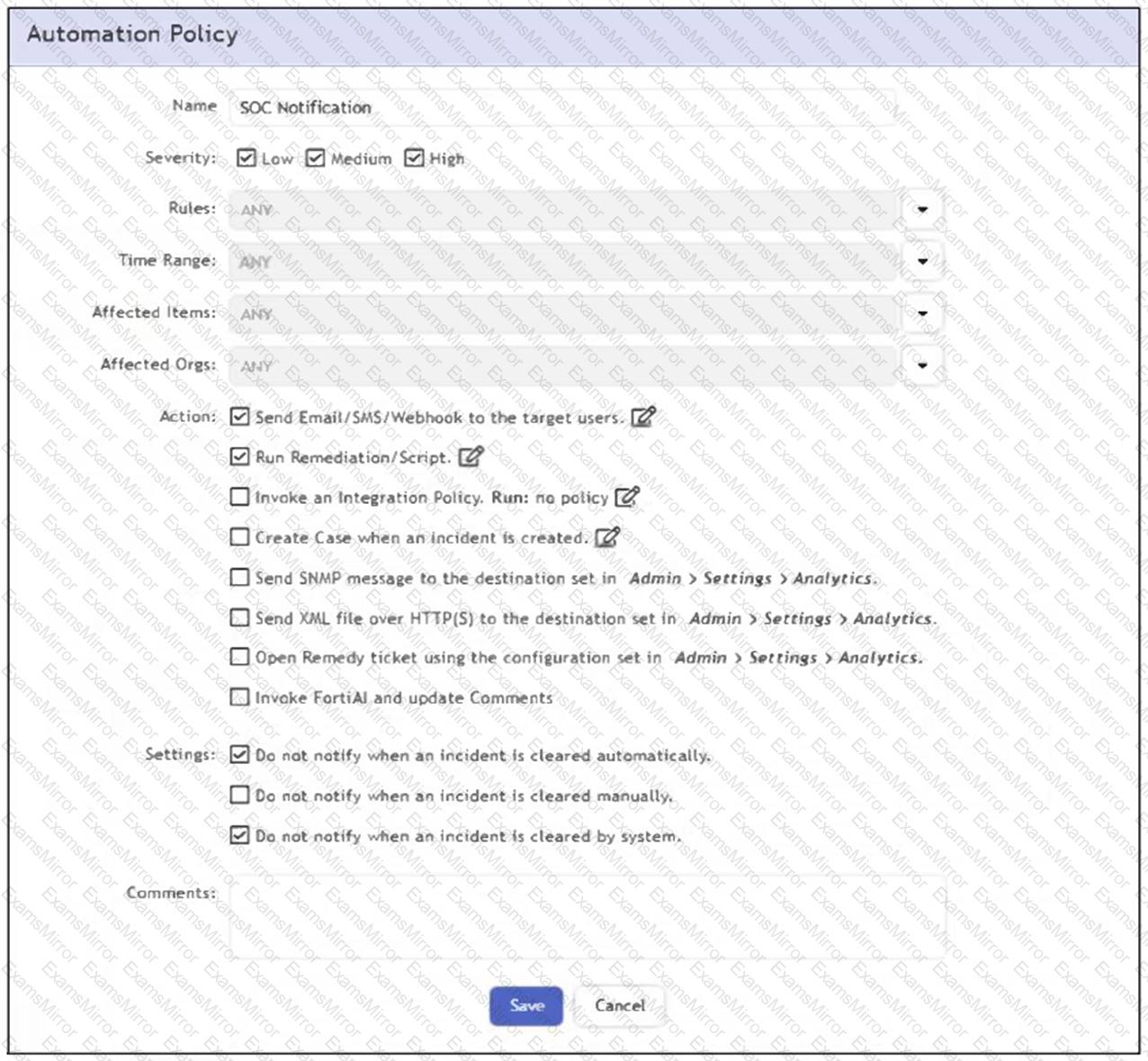
What happens when an analyst clears an incident generated by a rule containing the automation policy shown in the exhibit?
What are two required components of a rule? (Choose two.)
Refer to the exhibit.
Which two lookup types can you reference as the subquery in a nested analytics query? (Choose two.)
Refer to the exhibit.
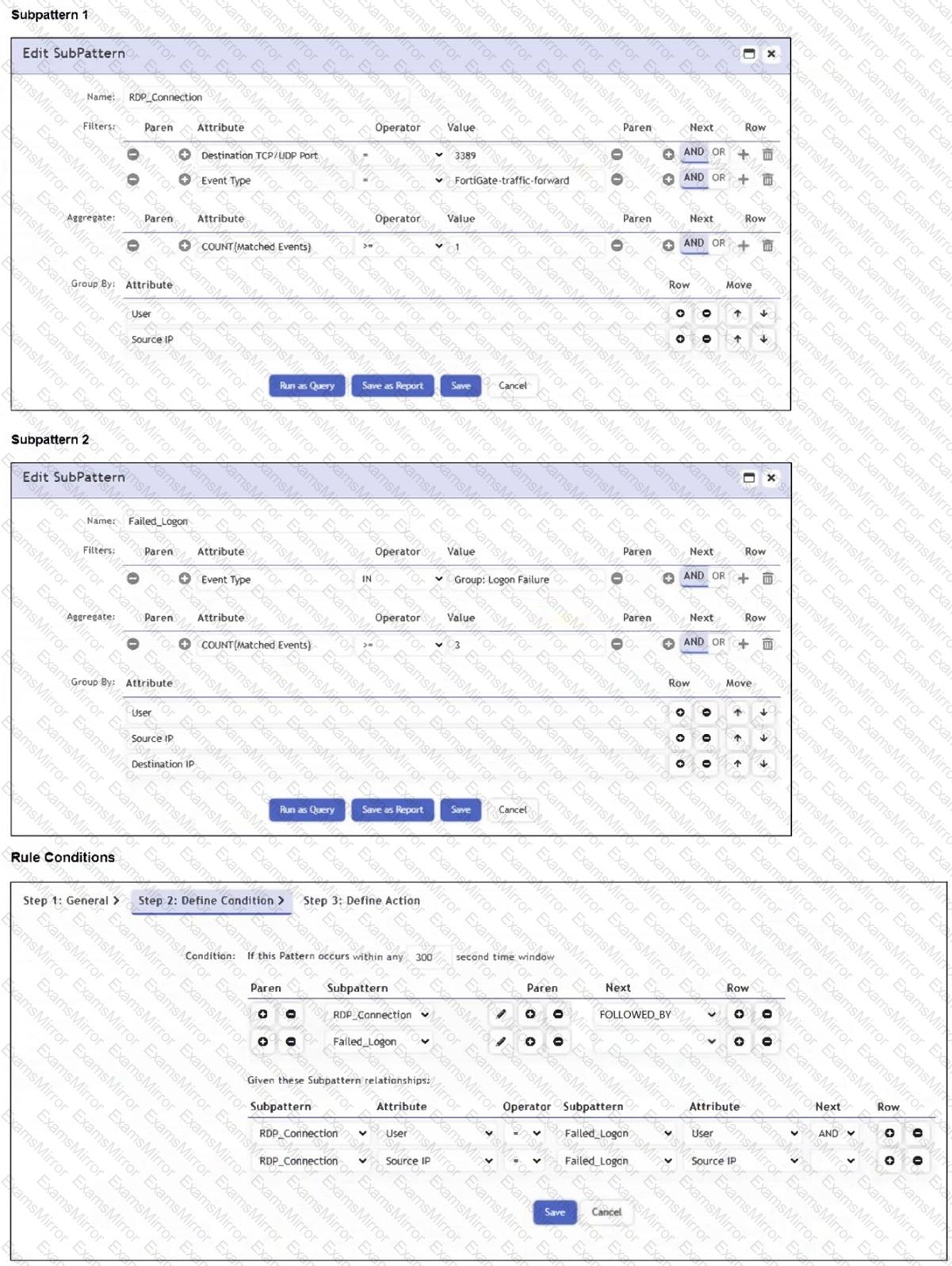
Which two conditions will match this rule and subpatterns? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
