Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Professional Security Operations FCSS_ADA_AR-6.7 Questions and answers with ExamsMirror
Exam FCSS_ADA_AR-6.7 Premium Access
View all detail and faqs for the FCSS_ADA_AR-6.7 exam
789 Students Passed
85% Average Score
90% Same Questions
Which lookup table function can be either true or false?
Refer to the exhibit.
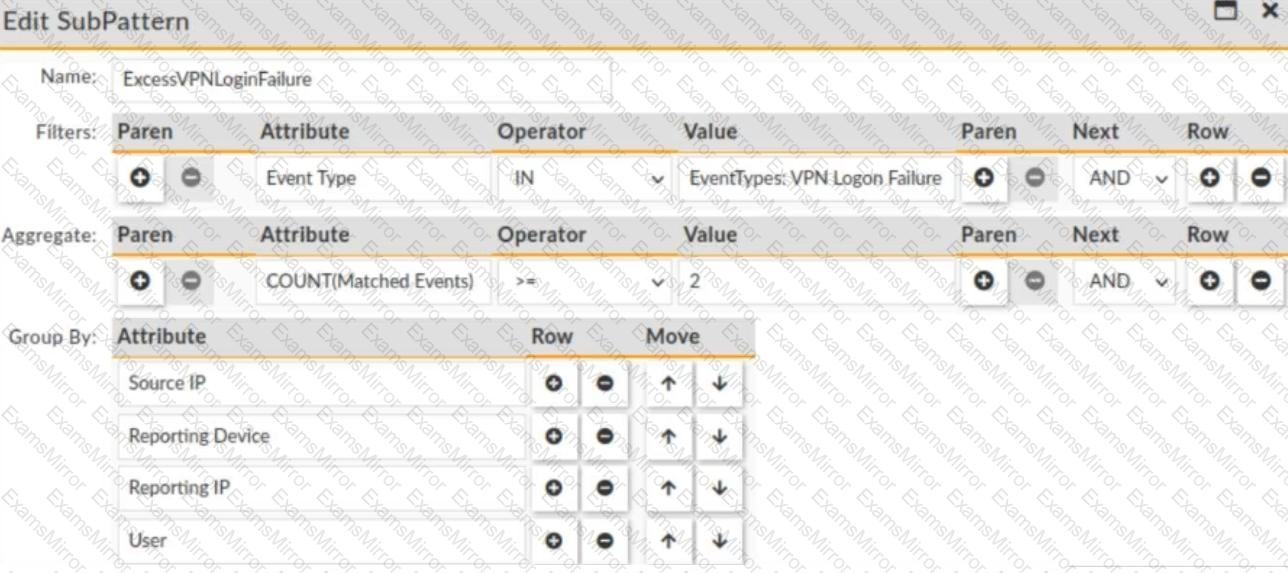
The rule evaluates multiple VPN logon failures within a ten-minute window. Consider the following VPN failure events received within a ten-minute window:
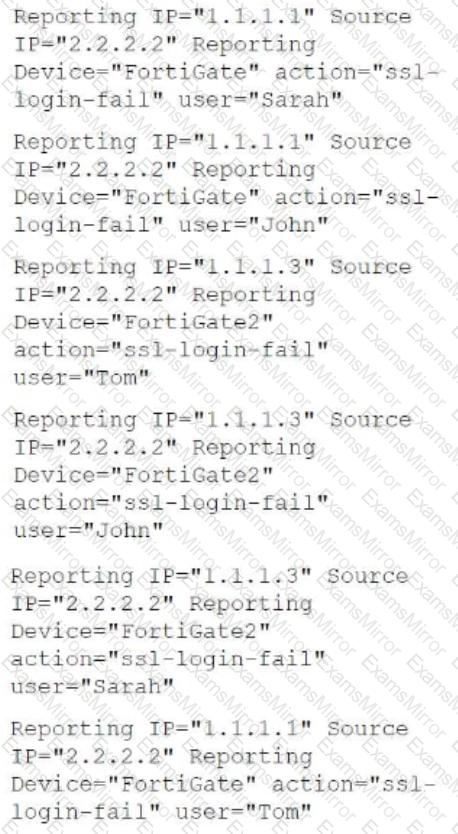
How many incidents are generated?
Refer to the exhibit.
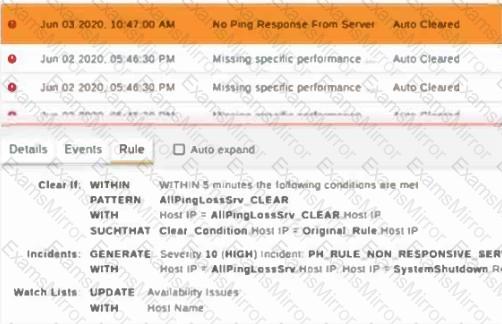
Why was this incident auto cleared?
What happens to events that the collector receives when there is a WAN link failure between the collector and the supervisor?
What is the hourly bucket used in baselining?
Which statement accurately contrasts lookup tables with watchlists?
Which two statements about the maximum device limit on FortiSIEM are true? (Choose two.)
Refer to the exhibit.
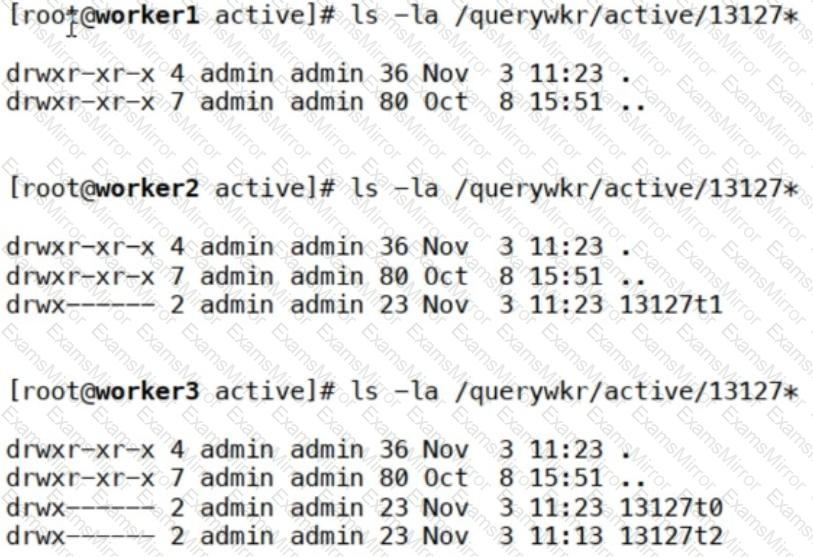
Which workers are assigned tasks for the query ID 13127? (Choose two.)
How can you invoke an integration policy on FortiSIEM rules?
What is the disadvantage of automatic remediation?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.

 The output does not show any subdirectories or task files (13127t0, 13127t1, etc.), meaning Worker1 is not assigned any tasks.
The output does not show any subdirectories or task files (13127t0, 13127t1, etc.), meaning Worker1 is not assigned any tasks. The output shows one task (13127t1) under /querywkr/active/13127*.
The output shows one task (13127t1) under /querywkr/active/13127*. The worker has only one assigned task, not two, so options C and D are incorrect.
The worker has only one assigned task, not two, so options C and D are incorrect. The output shows two tasks (13127t0 and 13127t1), indicating that Worker3 is processing two tasks for query ID 13127.
The output shows two tasks (13127t0 and 13127t1), indicating that Worker3 is processing two tasks for query ID 13127.