Cyber Monday Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Professional Network Security FCSS_EFW_AD-7.4 Questions and answers with ExamsMirror
Exam FCSS_EFW_AD-7.4 Premium Access
View all detail and faqs for the FCSS_EFW_AD-7.4 exam
667 Students Passed
97% Average Score
91% Same Questions
An administrator must enable direct communication between multiple spokes in a company's network. Each spoke has more than one internet connection.
The requirement is for the spokes to connect directly without passing through the hub, and for the links to automatically switch to the best available connection.
How can this automatic detection and optimal link utilization between spokes be achieved?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Refer to the exhibit, which shows the VDOM section of a FortiGate device.
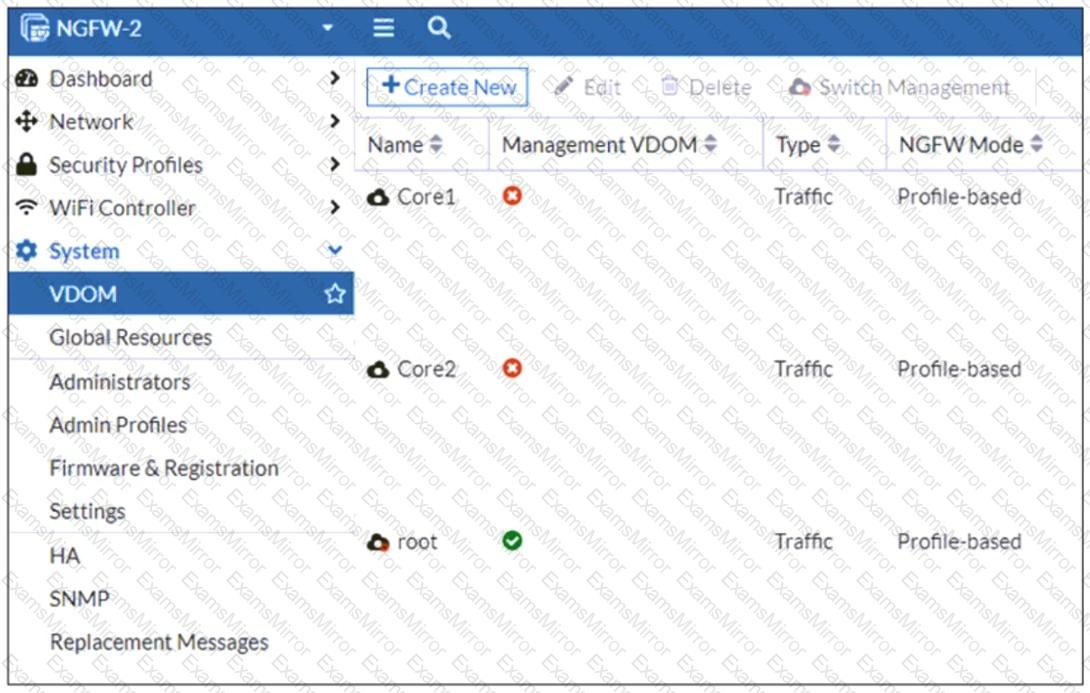
An administrator discovers that webfilter stopped working in Core1 and Core2 after a maintenance window.
Which two reasons could explain why webfilter stopped working? (Choose two.)
Refer to the exhibits. The exhibits show a network topology, a firewall policy, and an SSL/SSH inspection profile configuration.
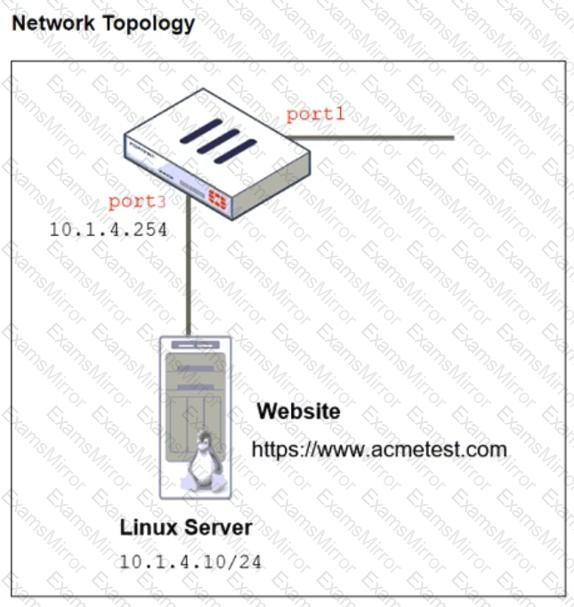
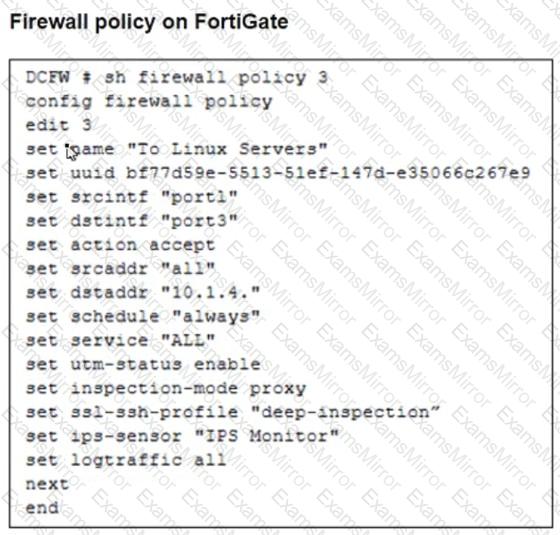
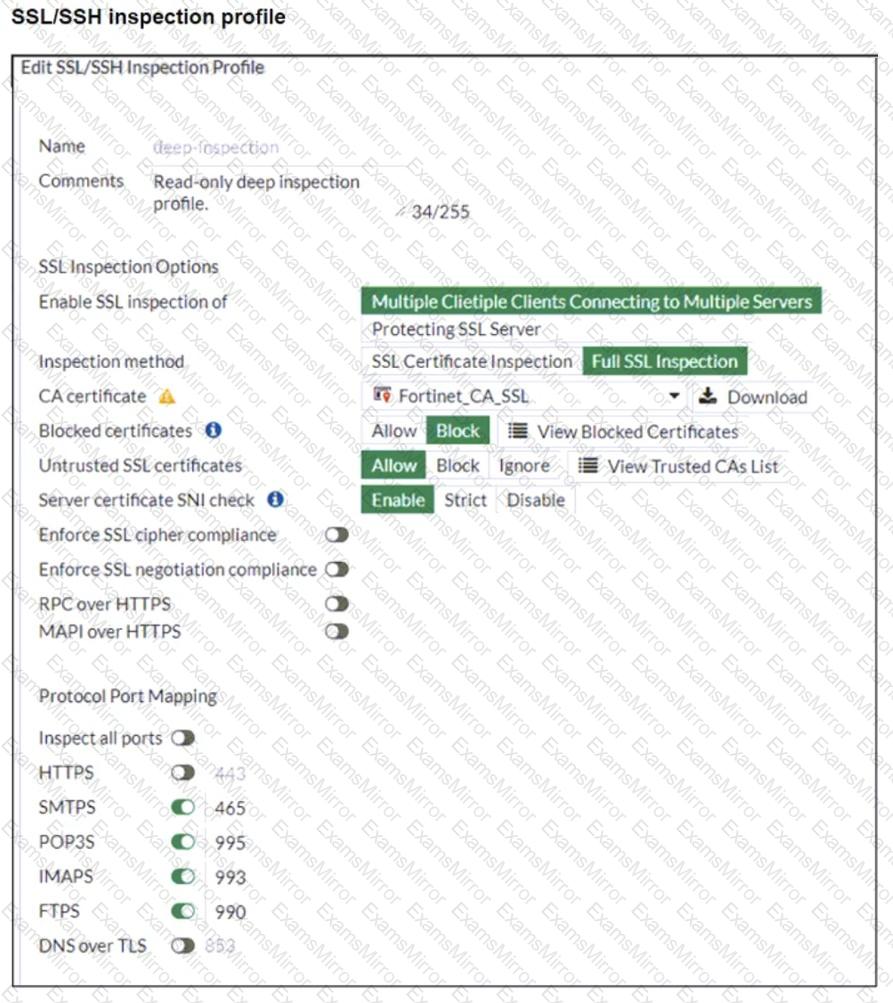
Why is FortiGate unable to detect HTTPS attacks on firewall policy ID 3 targeting the Linux server?
A company's users on an IPsec VPN between FortiGate A and B have experienced intermittent issues since implementing VXLAN. The administrator suspects that packets exceeding the 1500-byte default MTU are causing the problems.
In which situation would adjusting the interface’s maximum MTU value help resolve issues caused by protocols that add extra headers to IP packets?
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
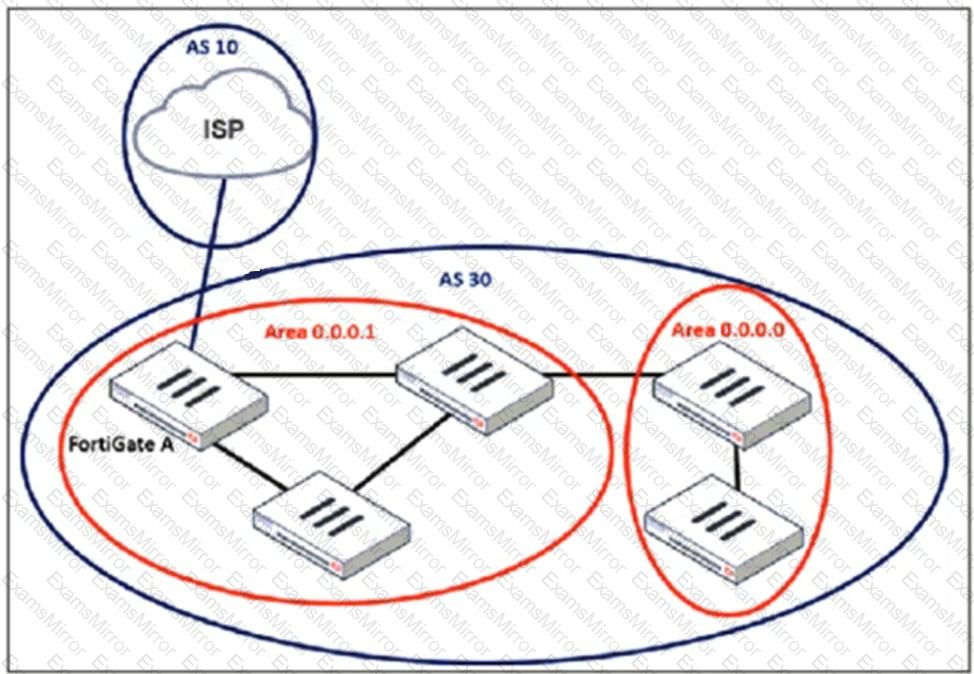
An administrator must configure a loopback as a BGP source to connect to the ISP.
Which two commands are required to establish the connection? (Choose two.)
An administrator wants to scale the IBGP sessions and optimize the routing table in an IBGP network.
Which parameter should the administrator configure?
An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic.
Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.

 BGP normally expects directly connected neighbors, but since the ISP and FortiGate A are usingloopback interfaces,packets will not be sent directly between their physical interfaces.
BGP normally expects directly connected neighbors, but since the ISP and FortiGate A are usingloopback interfaces,packets will not be sent directly between their physical interfaces. Theebgp-enforce-multihopcommandallows BGP to form an eBGP peering over multiple hops.
Theebgp-enforce-multihopcommandallows BGP to form an eBGP peering over multiple hops. Since FortiGate is using aloopback interface as the source, theupdate-sourcecommand ensures thatBGP updates originate from the loopback interfacerather than a physical interface.
Since FortiGate is using aloopback interface as the source, theupdate-sourcecommand ensures thatBGP updates originate from the loopback interfacerather than a physical interface. This is essential becauseBGP peers must match the source IP with the configured neighbor address.
This is essential becauseBGP peers must match the source IP with the configured neighbor address.