Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Professional Network Security FCSS_EFW_AD-7.6 Questions and answers with ExamsMirror
Exam FCSS_EFW_AD-7.6 Premium Access
View all detail and faqs for the FCSS_EFW_AD-7.6 exam
629 Students Passed
90% Average Score
95% Same Questions
A vulnerability scan report has revealed that a user has generated traffic to the website example.com (10.10.10.10) using a weak SSL/TLS version supported by the HTTPS web server.
What can the firewall administrator do to block all outdated SSL/TLS versions on any HTTPS web server to prevent possible attacks on user traffic?
Refer to the exhibit, which shows the FortiGuard Distribution Network of a FortiGate device.
FortiGuard Distribution Network on FortiGate

An administrator is trying to find the web filter database signature on FortiGate to resolve issues with websites not being filtered correctly in a flow-mode web filter profile.
Why is the web filter database version not visible on the GUI, such as with IPS definitions?
Refer to the exhibit, which shows a hub and spokes deployment.
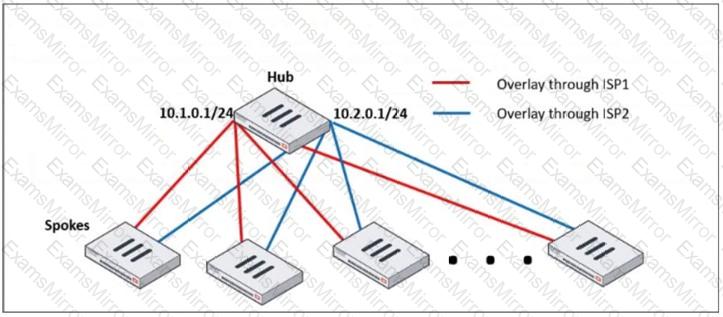
An administrator is deploying several spokes, including the BGP configuration for the spokes to connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
Refer to the exhibit, which shows a partial enterprise network.

An administrator would like the area 0.0.0.0 to detect the external network.
What must the administrator configure?
Refer to the exhibit.

The routing tables of FortiGate_A and FortiGate_B are shown. FortiGate_A and FortiGate_B are in the same autonomous system.
The administrator wants to dynamically add only route 172.16.1.248/30 on FortiGate_A.
What must the administrator configure?
Refer to the exhibit, which shows a LAN interface connected from FortiGate to two FortiSwitch devices.

What two conclusions can you draw from the corresponding LAN interface? (Choose two.)
An administrator received a FortiAnalyzer alert that a 1 ТВ disk filled up in a day. Upon investigation, they found thousands of unusual DNS log requests, such as JHCMQK.website.com, with no answers. They later discovered that DNS exfiltration was occurring through both UDP and TLS.
How can the administrator prevent this data theft technique?
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)
During the maintenance window, an administrator must sniff all the traffic going through a specific firewall policy, which is handled by NP6 interfaces. The output of the sniffer trace provides just a few packets.
Why is the output of sniffer trace limited?
Refer to the exhibit, which shows a network diagram.
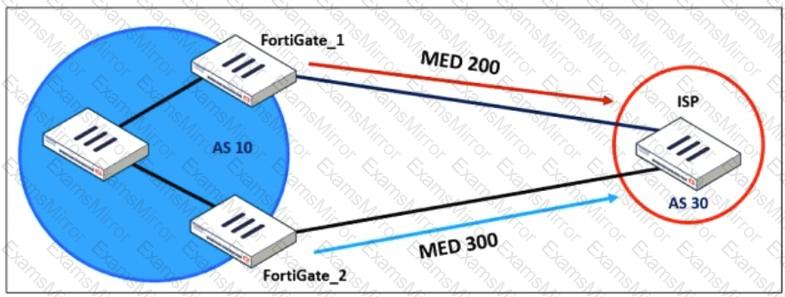
An administrator would like to modify the MED value advertised from FortiGate_1 to a BGP neighbor in the autonomous system 30.
What must the administrator configure on FortiGate_1 to implement this?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
