Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Solution Specialist FCSS_SASE_AD-25 Questions and answers with ExamsMirror
Exam FCSS_SASE_AD-25 Premium Access
View all detail and faqs for the FCSS_SASE_AD-25 exam
750 Students Passed
95% Average Score
95% Same Questions
In a FortiSASE secure web gateway (SWG) deployment, which two features protect against web-based threats? (Choose two.)
Refer to the exhibit.
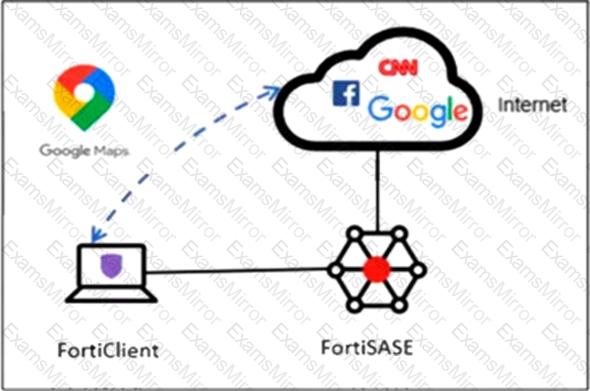
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
Refer to the exhibits.
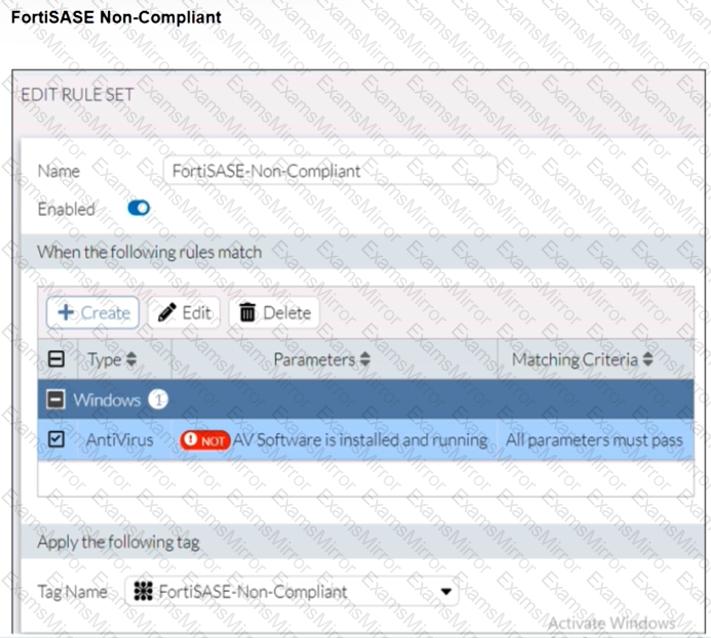
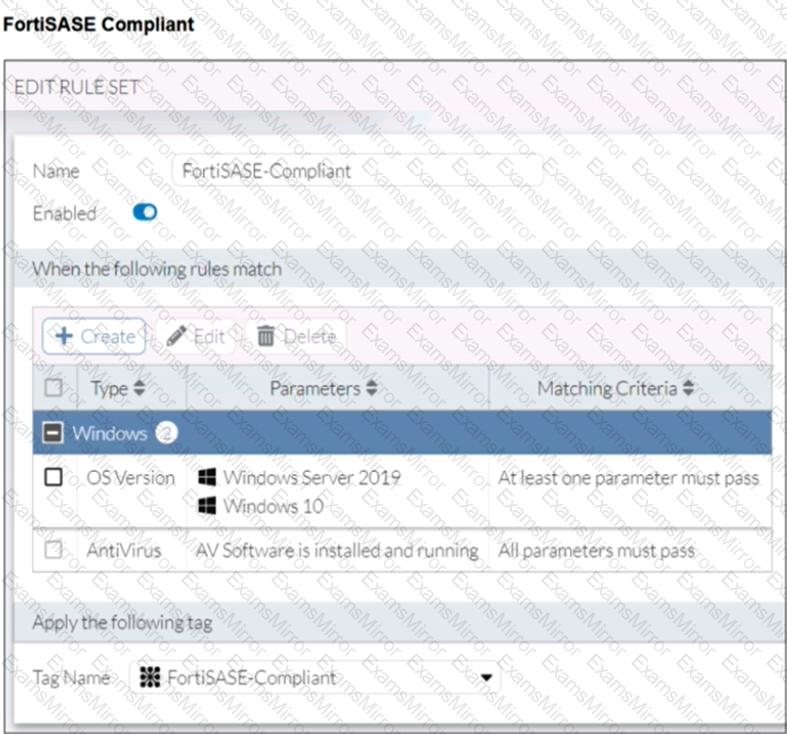
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two.)
Which two components are part of onboarding a secure web gateway (SWG) endpoint for secure internet access (SIA)? (Choose two.)
Which FortiSASE component protects users from online threats by hosting their browsing sessions on a remote container within a secure environment?
How do security profile group objects behave when central management is enabled on FortiSASE?
Refer to the exhibit.
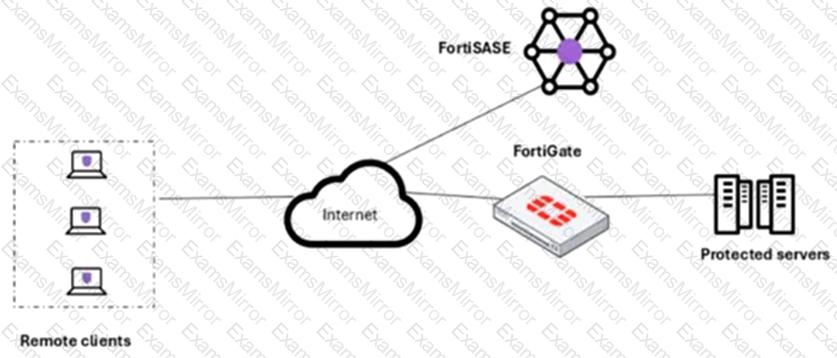
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which two setups will achieve these requirements? (Choose two.)
Refer to the exhibit.
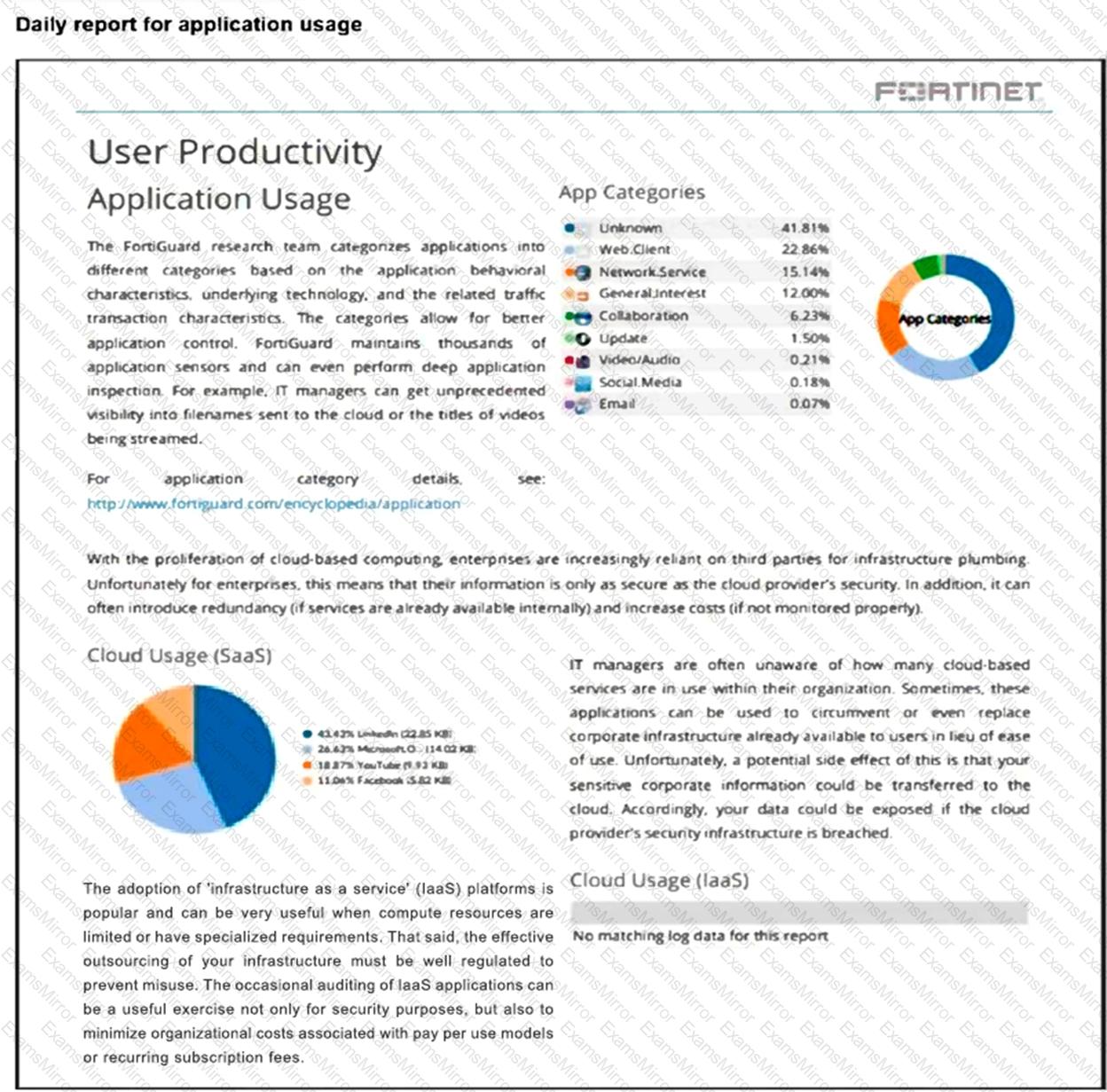
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
