Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet Certified Solution Specialist FCSS_SOC_AN-7.4 Questions and answers with ExamsMirror
Exam FCSS_SOC_AN-7.4 Premium Access
View all detail and faqs for the FCSS_SOC_AN-7.4 exam
648 Students Passed
94% Average Score
91% Same Questions
When configuring a FortiAnalyzer to act as a collector device, which two steps must you perform?(Choose two.)
Refer to the exhibit.
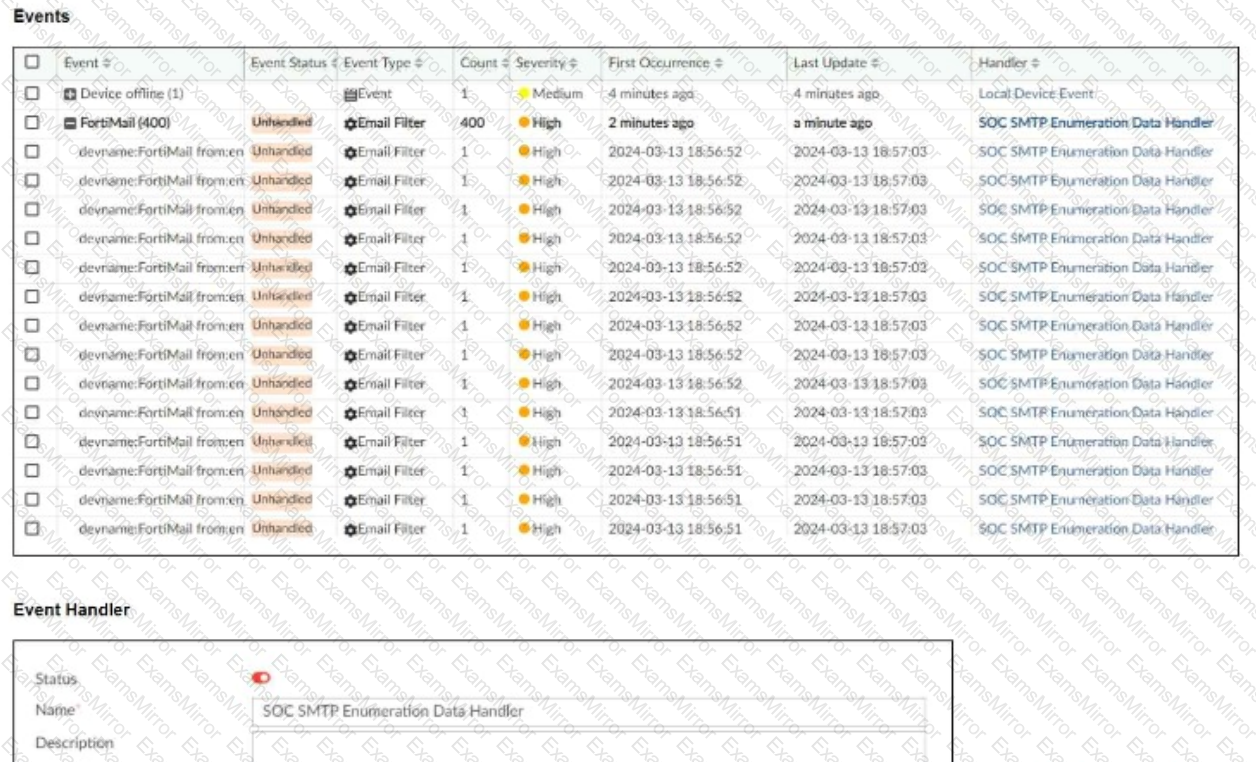
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is creating a large number of events. This is overwhelming your notification system.
How can you fix this?
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
Refer to the exhibits.
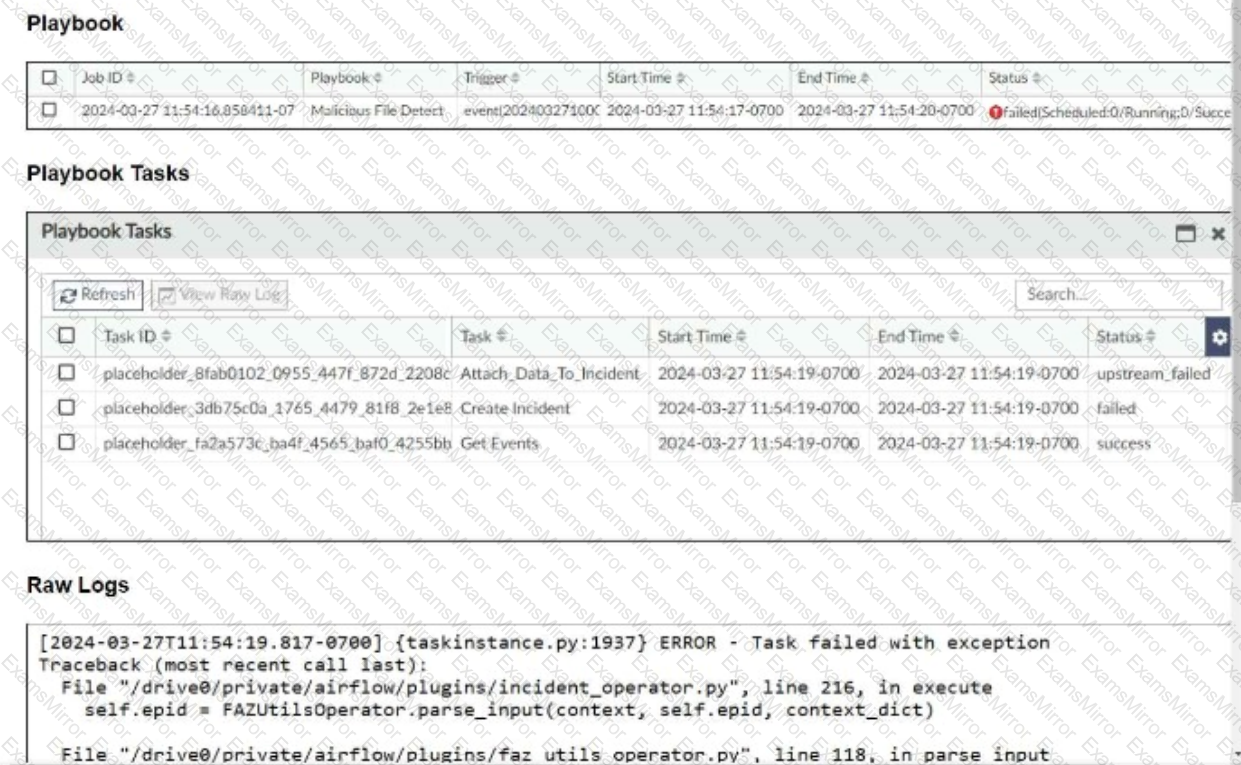
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Refer to the exhibit,
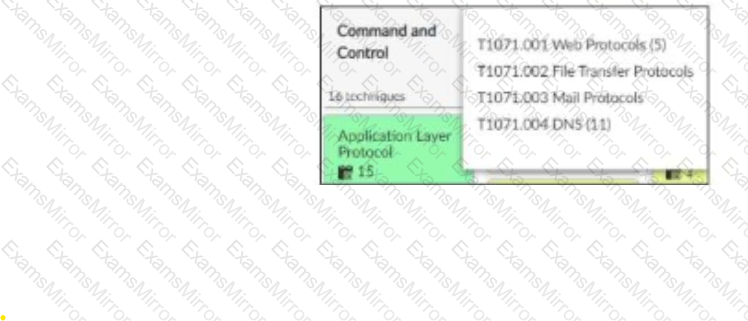
which shows the partial output of the MITRE ATT&CK Enterprise matrix on FortiAnalyzer.
Which two statements are true? (Choose two.)
Review the following incident report:
Attackers leveraged a phishing email campaign targeting your employees.
The email likely impersonated a trusted source, such as the IT department, and requested login credentials.
An unsuspecting employee clicked a malicious link in the email, leading to the download and execution of a Remote Access Trojan (RAT).
The RAT provided the attackers with remote access and a foothold in the compromised system.
Which two MITRE ATT&CK tactics does this incident report capture? (Choose two.)
Refer to Exhibit:
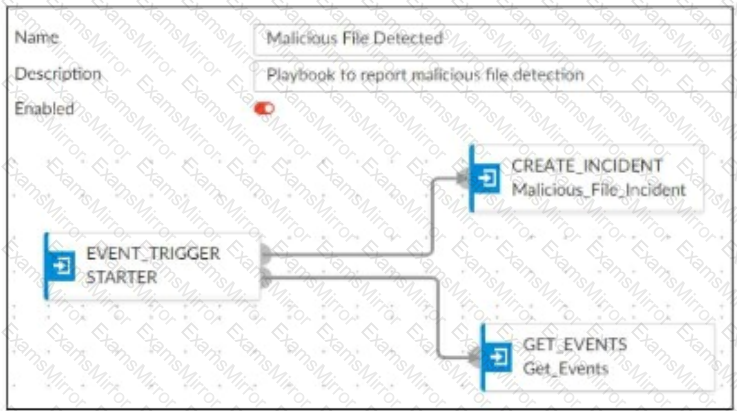
A SOC analyst is creating the Malicious File Detected playbook to run when FortiAnalyzer generates a malicious file event. The playbook must also update the incident with the malicious file event data.
What must the next task in this playbook be?
Refer to the exhibits.
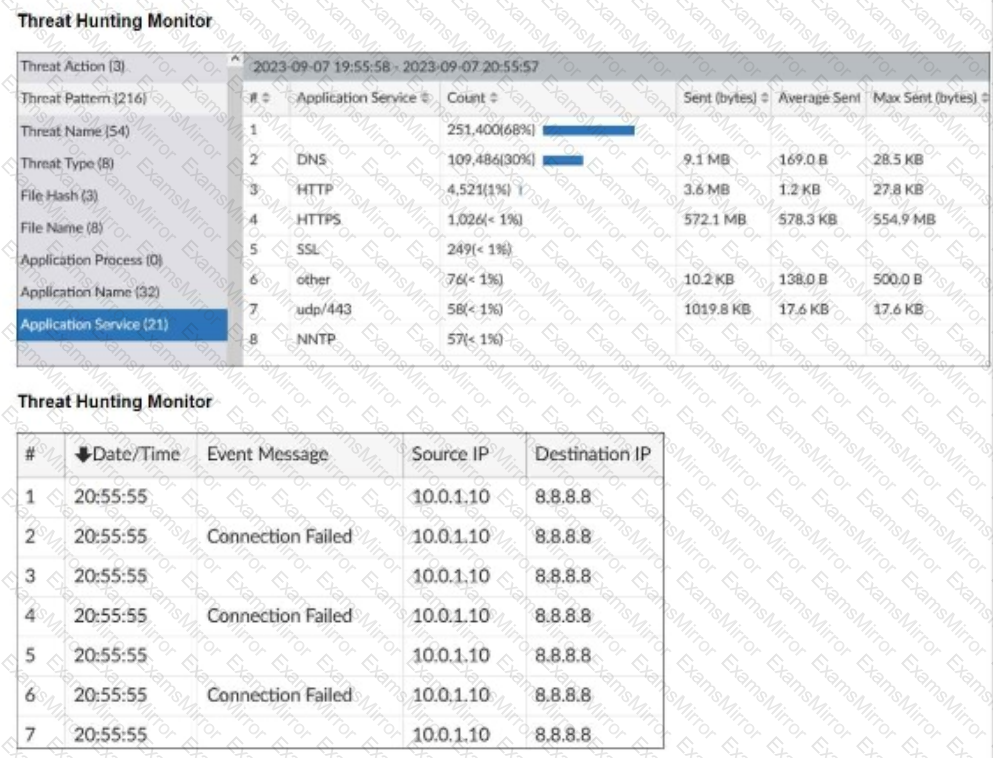
What can you conclude from analyzing the data using the threat hunting module?
Which two types of variables can you use in playbook tasks? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
