Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet NSE 6 Network Security Specialist NSE6_FNC-7.2 Questions and answers with ExamsMirror
Exam NSE6_FNC-7.2 Premium Access
View all detail and faqs for the NSE6_FNC-7.2 exam
664 Students Passed
86% Average Score
92% Same Questions
When FortiNAC is managing VPN clients connecting through FortiGate. why must the clients run a FortiNAC agent?
When FortiNAC passes a firewall tag to FortiGate, what determines the value that is passed?
Where are logical network values defined?
How does FortiGate update FortiNAC about VPN session information?
Which two of the following are required for endpoint compliance monitors? (Choose two.)
In which view would you find who made modifications to a Group?
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
Refer to the exhibit.
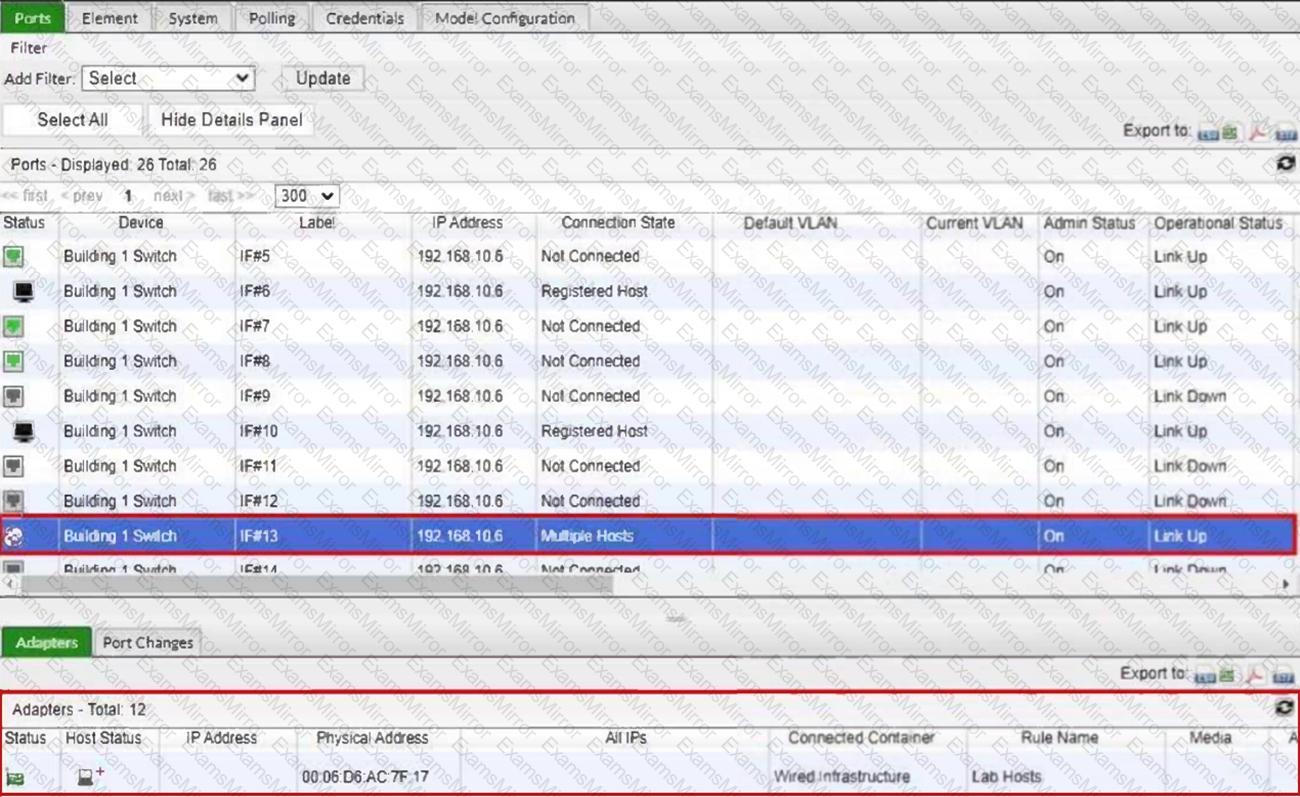
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
What capability do logical networks provide?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
