Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet NSE 6 Network Security Specialist NSE6_FNC-9.1 Questions and answers with ExamsMirror
Exam NSE6_FNC-9.1 Premium Access
View all detail and faqs for the NSE6_FNC-9.1 exam
682 Students Passed
91% Average Score
98% Same Questions
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
Which command line shell and scripting language does FortiNAC use for WinRM?
Which two of the following are required for endpoint compliance monitors? (Choose two.)
Where are logical network values defined?
View the command and output shown in the exhibit.
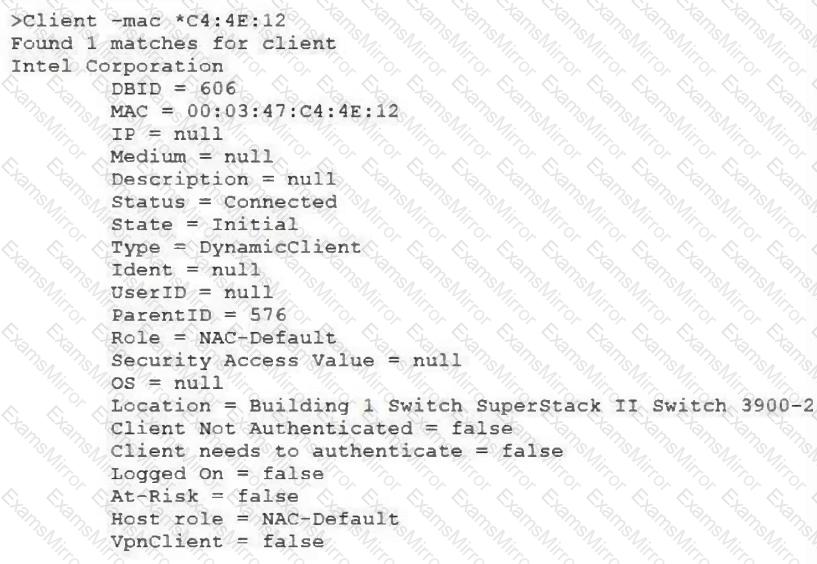
What is the current state of this host?
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Which two things must be done to allow FortiNAC to process incoming syslog messages from an unknown vendor? (Choose two.)
An administrator wants the Host At Risk event to generate an alarm. What is used to achieve this result?
Which agent is used only as part of a login script?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
