Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Fortinet NSE 7 Network Security Architect NSE7_EFW-7.2 Questions and answers with ExamsMirror
Exam NSE7_EFW-7.2 Premium Access
View all detail and faqs for the NSE7_EFW-7.2 exam
785 Students Passed
90% Average Score
90% Same Questions
Which two statements about the Security fabric are true? (Choose two.)
How are bulk configuration changes made using FortiManager CLI scripts? (Choose two.)
Refer to the exhibit, which shows an SSL certification inspection configuration.
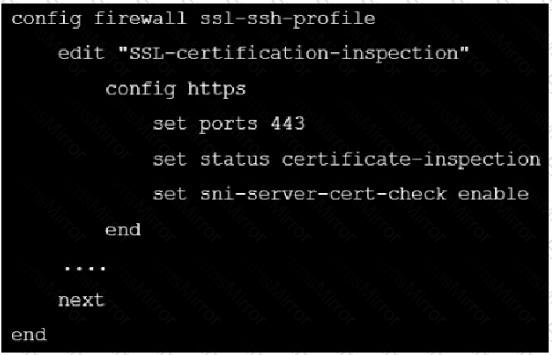
Which action does FortiGate take if the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate?
Which ADVPN configuration must be configured using a script on fortiManager, when using VPN Manager to manage fortiGate VPN tunnels?
Exhibit.
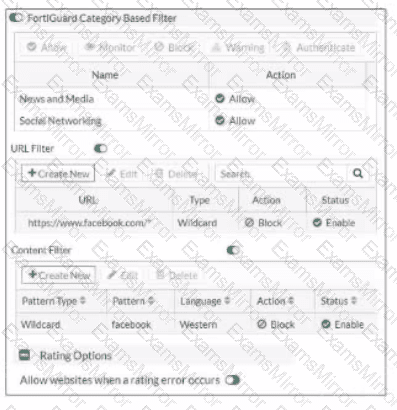
Refer to the exhibit, which shows a partial web filter profile conjuration
What can you cone udo from this configuration about access to www.facebook , com, which is categorized as Social Networking?
Exhibit.
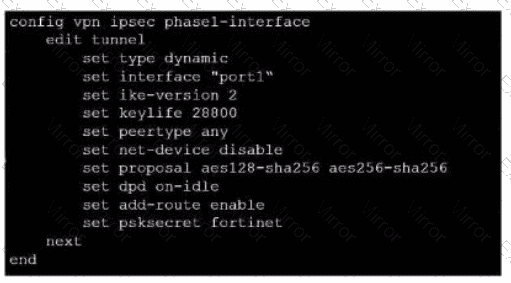
Refer to the exhibit, which contains a partial VPN configuration.
What can you conclude from this configuration1?
Which FortiGate in a Security I auric sends togs to FortiAnalyzer?
Which two statements about the BFD parameter in BGP are true? (Choose two.)
Which, three conditions are required for two FortiGate devices to form an OSPF adjacency? (Choose three.)
Which two statements about the Security Fabric are true? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
