Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Cyber Security GCCC Questions and answers with ExamsMirror
Exam GCCC Premium Access
View all detail and faqs for the GCCC exam
716 Students Passed
85% Average Score
93% Same Questions
Which of the following archiving methods would maximize log integrity?
An organization wants to test its procedure for data recovery. Which of the following will be most effective?
An organization has implemented a control for penetration testing and red team exercises conducted on their network. They have compiled metrics showing the success of the penetration testing (Penetration Tests), as well as the number of actual adversary attacks they have sustained (External Attacks). Assess the metrics below and determine the appropriate interpretation with respect to this control.
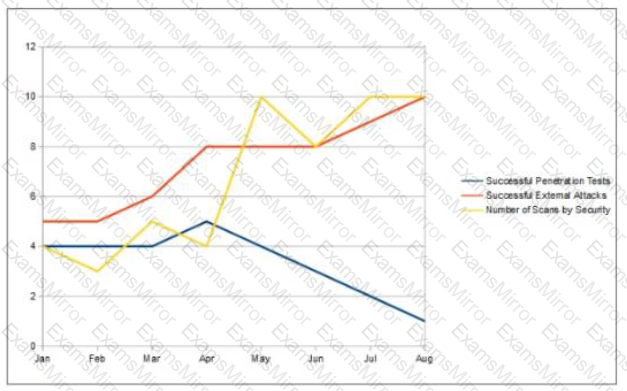
An organization has implemented a policy to continually detect and remove malware from its network. Which of the following is a detective control needed for this?
When evaluating the Wireless Access Control CIS Control, which of the following systems needs to be tested?
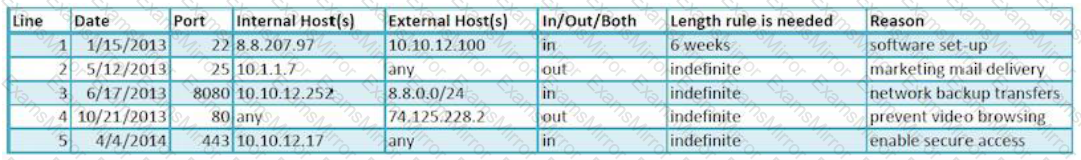
Dragonfly Industries requires firewall rules to go through a change management system before they are configured. Review the change management log. Which of the following lines in your firewall ruleset has expired and should be removed from the configuration?
An Internet retailer's database was recently exploited by a foreign criminal organization via a remote attack. The initial exploit resulted in immediate root-level access. What could have been done to prevent this level of access being given to the intruder upon successful exploitation?
What is the first step suggested before implementing any single CIS Control?
What is the business goal of the Inventory and Control of Software Assets Control?
Which of the following statements is appropriate in an incident response report?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
