Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Forensics GCFA Questions and answers with ExamsMirror
Exam GCFA Premium Access
View all detail and faqs for the GCFA exam
706 Students Passed
97% Average Score
90% Same Questions
Normally, RAM is used for temporary storage of data. But sometimes RAM data is stored in the hard disk, what is this method called?
Nathan works as a Computer Hacking Forensic Investigator for SecureEnet Inc. He uses Visual TimeAnalyzer software to track all computer usage by logging into individual users account or specific projects and compile detailed accounts of time spent within each program. Which of the following functions are NOT performed by Visual TimeAnalyzer?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned with the project of investigating an iPod, which is suspected to contain some explicit material. Adam wants to connect the compromised iPod to his system, which is running on Windows XP (SP2) operating system. He doubts that connecting the iPod with his computer may change some evidences and settings in the iPod. He wants to set the iPod to read-only mode. This can be done by changing the registry key within the Windows XP (SP2) operating system. Which of the following registry keys will Adam change to accomplish the task?
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below:
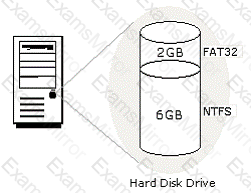
The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
Which of the following modules of OS X kernel (XNU) provides the primary system program interface?
Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP ports of his computer. Nathan uses the netstat command for this purpose but he is still unable to map open ports to the running process with PID, process name, and path. Which of the following commands will Nathan use to accomplish the task?
Which of the following parameters is NOT used for calculating the capacity of the hard disk?
Adam, a malicious hacker has successfully gained unauthorized access to the Linux system of
Umbrella Inc. Web server of the company runs on Apache. He has downloaded sensitive documents and database files from the computer. After performing these malicious tasks, Adam finally runs the following command on the Linux command box before disconnecting. for (( i = 0;i<11;i++ )); do
dd if=/dev/random of=/dev/hda && dd if=/dev/zero of=/dev/hda done
Which of the following actions does Adam want to perform by the above command?
You work as a Web developer for ABC Inc. You want to investigate the Cross-Site Scripting attack on your company's Web site. Which of the following methods of investigation can you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. He works with the local police. A project has been assigned to him to investigate an iPod, which was seized from a student of the high school. It is suspected that the explicit child pornography contents are stored in the iPod. Adam wants to investigate the iPod extensively. Which of the following operating systems will Adam use to carry out his investigations in more extensive and elaborate manner?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
