Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Cyber Security GICSP Questions and answers with ExamsMirror
Exam GICSP Premium Access
View all detail and faqs for the GICSP exam
683 Students Passed
85% Average Score
98% Same Questions
What is an output of a Business Impact Analysis?
Which resource includes a standardized categorization of common software vulnerabilities?
How arc general purpose Programmable Logic Controllers (PLC) different than smart field devices?
What is a use of Network Address Translation?
Which of the following types of network devices sends traffic only to the intended recipient node?
Which of the following would use round-robin process scheduling?
For application-aware firewalls filtering traffic between trust zones, which of the following policies should be applied to a packet that doesn't match an existing rule?
Based on the following diagram, how many Active Directory domains should be created for this network?
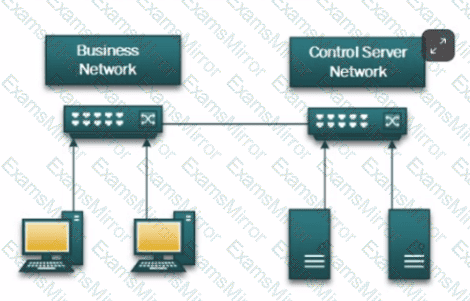
During a plant upgrade an architect needs to connect legacy lEDs to a new TCP/IP instrumentation LAN. The lEDs only have RS-232 communication interfaces available. What would best be used to connect the lEDs?
Which command can be used on a Linux system to search a file for a string of data and return the results to the screen?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
