Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Google Cloud Certified Security-Operations-Engineer Questions and answers with ExamsMirror
Exam Security-Operations-Engineer Premium Access
View all detail and faqs for the Security-Operations-Engineer exam
661 Students Passed
91% Average Score
91% Same Questions
You are implementing Google Security Operations (SecOps) with multiple log sources. You want to closely monitor the health of the ingestion pipeline's forwarders and collection agents, and detect silent sources within five minutes. What should you do?
You are a SOC manager at an organization that recently implemented Google Security Operations (SecOps). You need to monitor your organization's data ingestion health in Google SecOps. Data is ingested with Bindplane collection agents. You want to configure the following:
• Receive a notification when data sources go silent within 15 minutes.
• Visualize ingestion throughput and parsing errors.
What should you do?
You are implementing Google Security Operations (SecOps) for your organization. Your organization has their own threat intelligence feed that has been ingested to Google SecOps by using a native integration with a Malware Information Sharing Platform (MISP). You are working on the following detection rule to leverage the command and control (C2) indicators that were ingested into the entity graph.
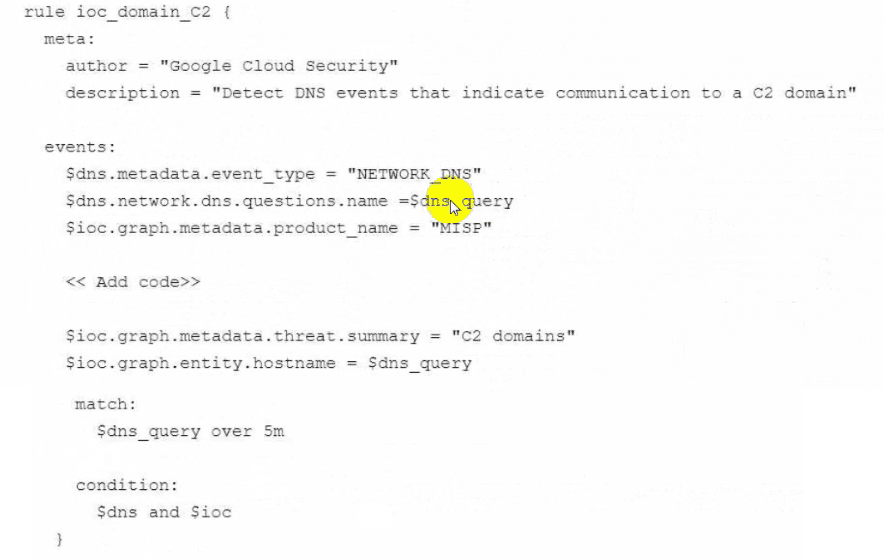
What code should you add in the detection rule to filter for the domain IOCS?
Your organization uses Google Security Operations (SecOps) for security analysis and investigation. Your organization has decided that all security cases related to Data Loss Prevention (DLP) events must be categorized with a defined root cause specific to one of five DLP event types when the case is closed in Google SecOps. How should you achieve this?
Your organization uses the curated detection rule set in Google Security Operations (SecOps) for high priority network indicators. You are finding a vast number of false positives coming from your on-premises proxy servers. You need to reduce the number of alerts. What should you do?
You work for an organization that operates an ecommerce platform. You have identified a remote shell on your company's web host. The existing incident response playbook is outdated and lacks specific procedures for handling this attack. You want to create a new, functional playbook that can be deployed as soon as possible by junior analysts. You plan to use available tools in Google Security Operations (SecOps) to streamline the playbook creation process. What should you do?
You have identified a common malware variant on a potentially infected computer. You need to find reliable IoCs and malware behaviors as quickly as possible to confirm whether the computer is infected and search for signs of infection on other computers. What should you do?
You scheduled a Google Security Operations (SecOps) report to export results to a BigQuery dataset in your Google Cloud project. The report executes successfully in Google SecOps, but no data appears in the dataset. You confirmed that the dataset exists. How should you address this export failure?
You were recently hired as a SOC manager at an organization with an existing Google Security Operations (SecOps) implementation. You need to understand the current performance by calculating the mean time to respond or remediate (MTTR) for your cases. What should you do?
You are conducting proactive threat hunting in your company's Google Cloud environment. You suspect that an attacker compromised a developer's credentials and is attempting to move laterally from a development Google Kubernetes Engine (GKE) cluster to critical production systems. You need to identify IoCs and prioritize investigative actions by using Google Cloud's security tools before analyzing raw logs in detail. What should you do next?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
