Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the HP Aruba Certified Switching Professional (ACSP) V1 HPE6-A73 Questions and answers with ExamsMirror
Exam HPE6-A73 Premium Access
View all detail and faqs for the HPE6-A73 exam
722 Students Passed
93% Average Score
93% Same Questions
A company has recently upgraded their campus switching infrastructure with AOS-CX switches. They have
implemented 802.1X authentication on access ports where laptop and IOT devices typically connect. An
administrator has noticed that for POE devices, the AOS-CX switch ports are delivering the maximum wattage
to the port instead of what the device actually needs.
Concerned about this waste of electricity, what should the administrator implement to solve this problem?
A network engineer is having a problem adding a custom-written script to an AOS-CX switch’s NAE GUI. The script was written in Python and was successfully added on other AOS-CX switches. The engineer examines the following items from the CLI of the switch:
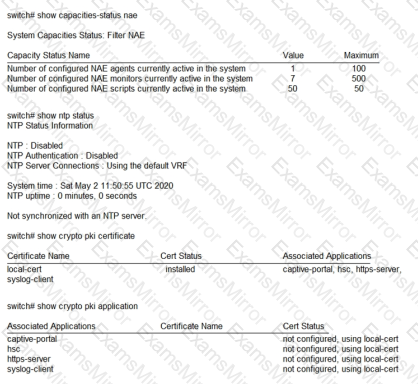
What should the engineer perform to fix this issue?
Examine the attached diagram
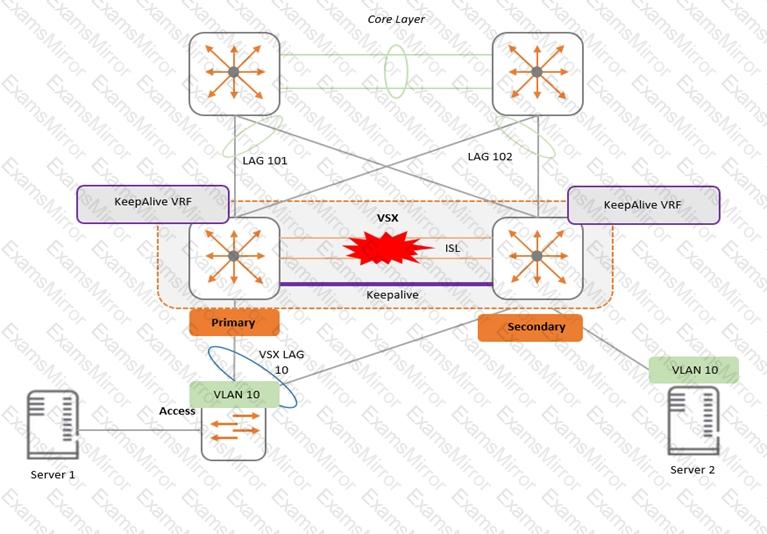
Two AOS-CX switches are configured for VSX at the access layer, where servers attached to them. An SVI interface is configured for VLAN 10 and serves as the default gateway for VLAN 10. The ISL link between the switches fails, but the keepalive interface functions. Active gateway has been configured on the switches.
What is correct about access from the servers to the Core?
Which protocol does NetEdit use to discover devices in a subnet during the discovery process?
A company has recently purchased a ClearPass AAA solution. Their network consists of AOS-CX switches at the access layer. The company is implementing a rollout of IoT devices for smart building management to control the lighting and HVAC systems. The network administrator is concerned about allowing secure access to these devices since they only support MAC-Auth.
Which ClearPass feature should the administrator leverage to help determine that MAC address spoofing is not occurring for this group of devices?
The network is configured for OSPF with the following attributes:
Core1 and Core2 and ABRs
Area 1 has 20 networks in the 10.1.0.0/16 range
Area 0 has 10 networks in the 10.0.0.0/16 range
Area 2 has 50 networks in the 10.2.0.0/16 range
The ASBR is importing a static route into Area 1
Core2 has a summary for Area 2: area 0.0.0.2 range 10.2.0.0/16 type inter-area
Here is the OSPF configuration performed on Core1:
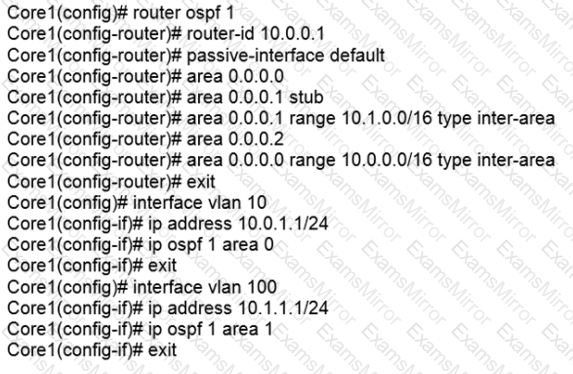
Based on the above information, what is correct?
An administrator is implementing a downloadable user role solution involving AOS-CX switches. The AAA
solution and the AOS-CX switches can successfully authenticate users; however, the role information fails to
download to the switches. What policy should be added to an intermediate firewall to allow the downloadable
role function to succeed?
A network administrator is implementing OSPF, where there are two exit points. Each exit point has a stateful, application inspection firewall to implement company policies.
What would the best practice be to ensure that one firewall will see both directions of the traffic, preventing asynchronous connections in the network?
Which protocol should be configured to allow NetEdit to discover third-party devices?
What is a concept associated with PIM sparse mode (SM)?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
