Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Huawei HCIA-Security H12-711_V4.0 Questions and answers with ExamsMirror
Exam H12-711_V4.0 Premium Access
View all detail and faqs for the H12-711_V4.0 exam
716 Students Passed
85% Average Score
93% Same Questions
In the authentication policy of the firewall, _____ allows the user to not need to enter the user name and password, but can obtain the corresponding relationship between the user and the IP, so as to carry out policy management based on the user[fill in the blank]*
Which layer of the protocol stack does SSL provide end-to-end encrypted transmission services?
The following description of asymmetric encryption algorithms, which item is wrong?
For which of the following parameters can the packet filtering firewall filter?
In cases where some configurations alter existing session table entries and want them to take effect immediately, you can regenerate the session table by clearing the session table information. All session table information can be cleared by executing the _____firewall session table command.
During the process of establishing IPSec VPN between peers FW_A and FW_B, two types of security associations need to be established in two stages. In the first stage, _____ is established to verify the identity of the peers.[fill in the blank]*
Which of the following is the correct sequence for incident response management
1. Detection 2 Report 3 Mitigation 4 Lessons learned 5 Fix 6 Recovery 7 Response
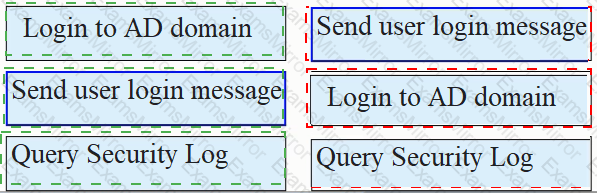
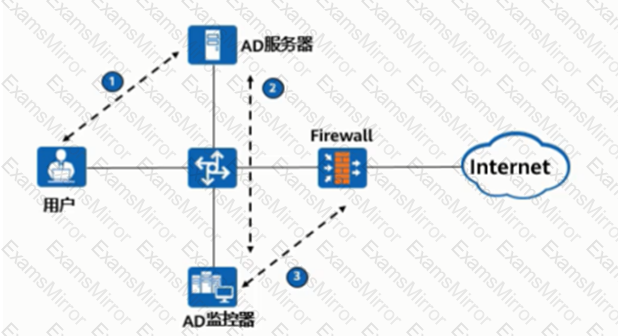
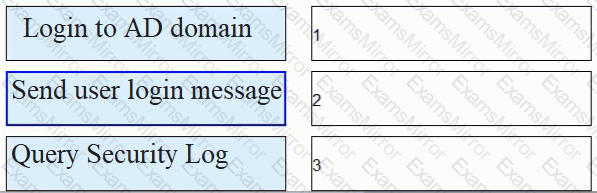
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.
Which of the following is not an advantage of symmetric encryption algorithms?
The keys used by the IPSec encryption and authentication algorithms can be configured manually or dynamically negotiated via the ____ protocol. (abbreviation, all uppercase).
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.