Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Huawei Certified Network Professional HCNP H12-721 Questions and answers with ExamsMirror
Exam H12-721 Premium Access
View all detail and faqs for the H12-721 exam
712 Students Passed
92% Average Score
95% Same Questions
What are the following attacks that are malformed?
The load balancing function is configured on the USG firewall for three FTP servers. The IP addresses and weights of the three physical servers are 10.1.13/24 (weight 16); 10.1.1.4/24 (weight 32); 10.1.1.5 /24 (weight 16), and the virtual server address is 202.152.26.123/24. A PC with the host address of 202.152.26.3/24 initiates access to the FTP server. Run the display firewall session table command on the firewall to check the configuration. Which of the following conditions indicates that the load balancing function is successfully implemented?
What are the correct statements about the IP address scanning attack and prevention principles?
Which of the following protocols does the USG firewall hot standby not include?
Load balancing implements the function of distributing user traffic accessing the same IP address to different servers. What are the main technologies used?
What type of message is the VRRP hello message?
Two USG firewalls establish an IPSec VPN through the Site to Site mode. When viewing the status of a USG A, the following is displayed: display ipsec statistics the security packet statistics: input/output security paskets: 40 input/output security bytes: 400/0 input /output dropped security packets: 0/0 By status information, what information can be obtained correctly?
Which of the following attacks is a SYN Flood attack?
The constraints of the policy in the traffic limiting policy include quintuple, time period, user identity, and application protocol.
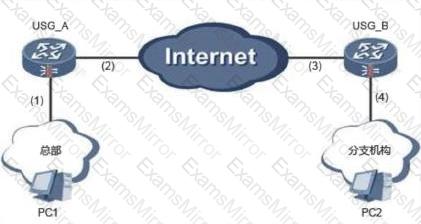
The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
