Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Huawei HCIP-Security H12-724 Questions and answers with ExamsMirror
Exam H12-724 Premium Access
View all detail and faqs for the H12-724 exam
691 Students Passed
92% Average Score
90% Same Questions
Which of the following options belong to the network layer attack of the TCP/IP protocol stack? (multiple choice)
Portal authentication on the Agile Controller-Campus has been configured and is correct.
Configure the following commands on the access control switch:
[S5720] authentication free-rule 1 destination ip 10.1.31.78 mask 255.255. 255.255
Which of the following options are correct? (multiple choice)
Jailbroken mobile terminal\Mobile terminals with non-compliant applications installed or terminals with non-compliant lock screen passwords connecting to the corporate network for office operations are not safe for companies. Any 0fice How to solve the problem of mobile office system?
In some scenarios, an anonymous account can be used for authentication. What are the correct descriptions of the following options for the anonymous account?? (Multiple choice)
Anti-DDoS defense system includes: management center, detection center and cleaning center.
Fage attack means that the original address and target address of TOP are both set to the IP address of a certain victim. This behavior will cause the victim to report to it.
SYN-ACK message is sent from the address, and this address sends back an ACK message and creates an empty connection, which causes the system resource board to occupy or target
The host crashed.
According to the user’s access5W1H Conditions determine access rights andQoS Strategy for5W1Ho[Which of the following descriptions are correct? (Multiple choice)
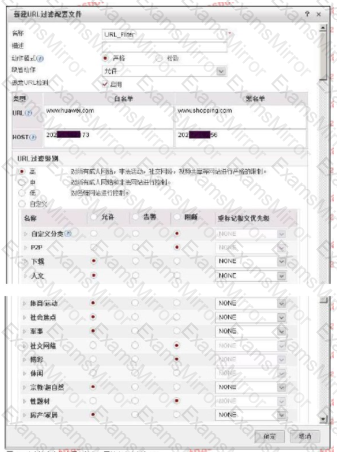
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
If a company wants to detect image files, Shellcode code files and PDF files, which of the following types of sandboxes can be used? (More
155955cc-666171a2-20fac832-0c042c0420
select)
Regarding the way SACG devices connect to the network, which of the following descriptions are correct? (multiple choice)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
