Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Huawei HCIP-Security H12-725_V4.0 Questions and answers with ExamsMirror
Exam H12-725_V4.0 Premium Access
View all detail and faqs for the H12-725_V4.0 exam
761 Students Passed
88% Average Score
96% Same Questions
Which of the following statements is false about HTTP behavior?
Which of the following statements is true about the outgoing traffic in the firewall virtual system?
Network Access Control (NAC) is an end-to-end security control technology that works in combination with AAA to implement access authentication. Which of the following statements about NAC and AAA are true?(Select All that Apply)
Which of the following statements are true about SYN scanning attacks?(Select All that Apply)
Which of the following statements is false about hot standby networking?(Select All that Apply)
Which of the following statements is false about Eth-Trunk?(Select All that Apply)
Which of the following statements is false about virtual system resource allocation?
Which of the following statements is false about the restrictions on configuring bandwidth profiles in parent and child policies on a firewall?
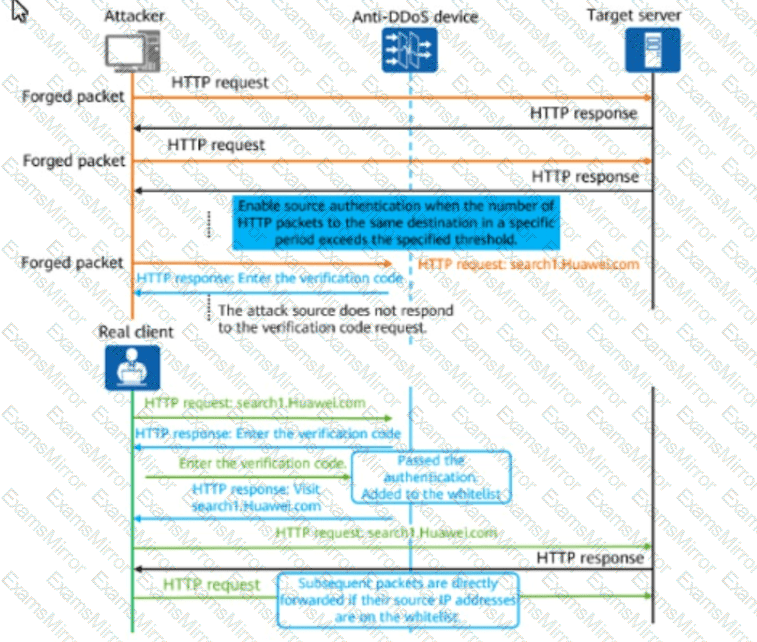
The figure shows the defense mechanism of an HTTP flood attack. Which source IP detection technology is displayed in the figure?
Which of the following actions can be performed when the firewall identifies file anomalies?(Select All that Apply)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
