Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Juniper JNCIS-SEC JN0-335 Questions and answers with ExamsMirror
Exam JN0-335 Premium Access
View all detail and faqs for the JN0-335 exam
659 Students Passed
89% Average Score
92% Same Questions
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
Which two statements are correct about a reth LAG? (Choose two.)
You want to deploy a virtualized SRX in your environment.
In this scenario, why would you use a vSRX instead of a cSRX? (Choose two.)
Which statement defines the function of an Application Layer Gateway (ALG)?
Exhibit
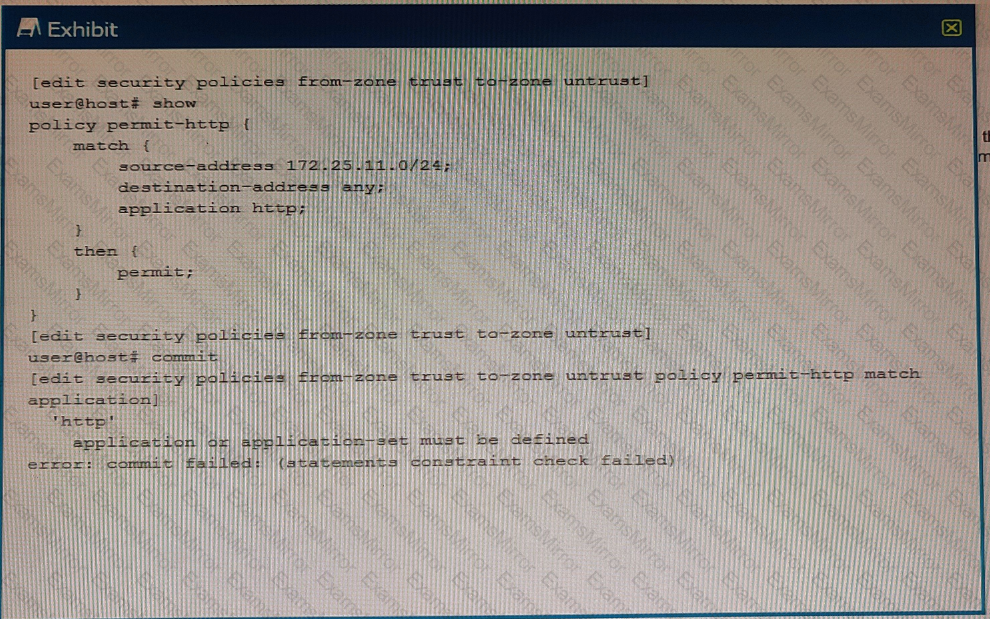
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
Which method does the loT Security feature use to identify traffic sourced from IoT devices?
You have implemented a vSRX in your VMware environment. You want to implement a second vSRX Series device and enable chassis clustering.
Which two statements are correct in this scenario about the control-link settings? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
