Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Microsoft Azure Security Engineer Associate AZ-500 Questions and answers with ExamsMirror
Exam AZ-500 Premium Access
View all detail and faqs for the AZ-500 exam
764 Students Passed
84% Average Score
98% Same Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center for the centralized policy management of three Azure subscriptions.
You use several policy definitions to manage the security of the subscriptions.
You need to deploy the policy definitions as a group to all three subscriptions.
Solution: You create an initiative and an assignment that is scoped to the Tenant Root Group management group.
Does this meet the goal?
You are configuring an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the auto-generated service principal to authenticate to the Azure Container Registry.
What should you create?
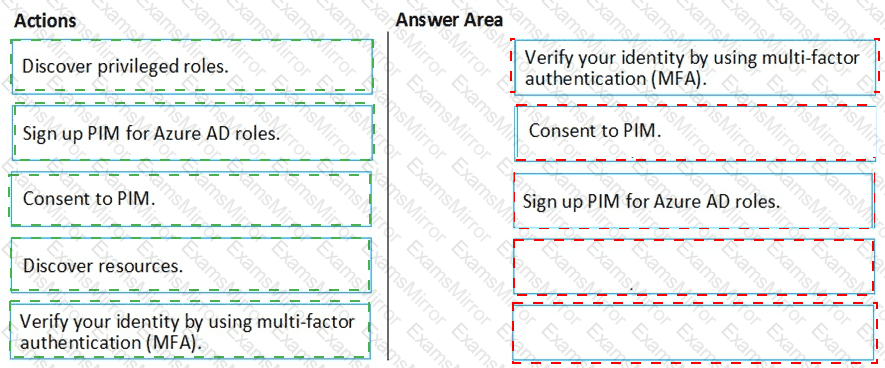
You create an Azure subscription with Azure AD Premium P2.
You need to ensure that you can use Azure Active Directory (Azure AD) Privileged Identity Management (PIM) to secure Azure roles.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

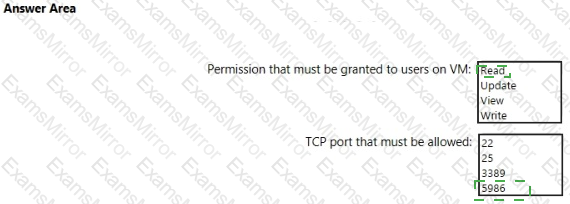
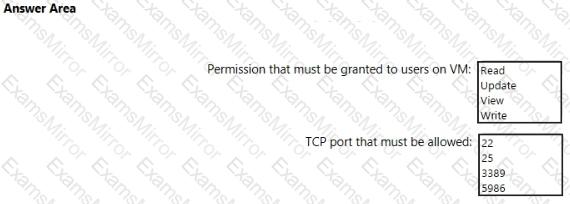
You are configuring just in time (JIT) VM access to a set of Azure virtual machines.
You need to grant users PowerShell access to the virtual machine by using JIT VM access.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
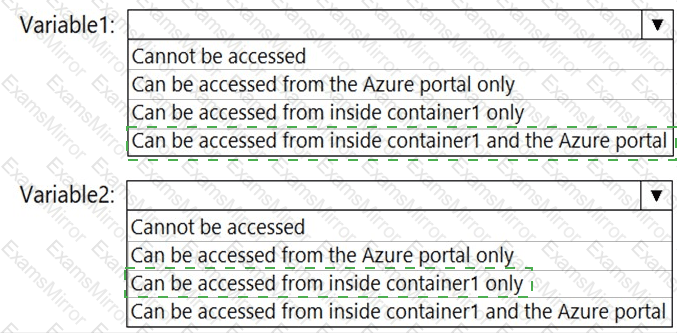
You have a file named File1.yaml that contains the following contents.
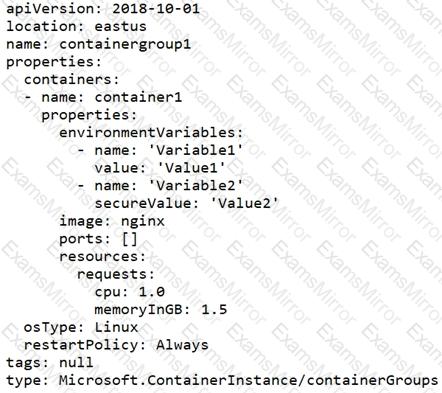
You create an Azure container instance named container1 by using File1.yaml.
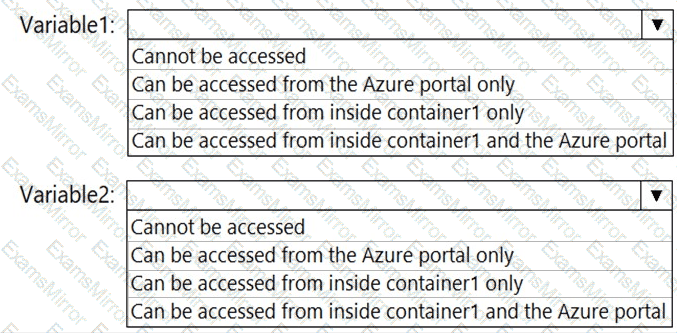
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
From Azure Security Center, you enable Azure Container Registry vulnerability scanning of the images in
Registry1.
You perform the following actions:
Push a Windows image named Image1 to Registry1.
Push a Linux image named Image2 to Registry1.
Push a Windows image named Image3 to Registry1.
Modify Image1 and push the new image as Image4 to Registry1.
Modify Image2 and push the new image as Image5 to Registry1.
Which two images will be scanned for vulnerabilities? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1.
You have 100 on-premises servers that run Windows Server 2012 R2 and Windows Server 2016. The servers connect to LAW1. LAW1 is configured to collect security-related performance counters from the connected servers.
You need to configure alerts based on the data collected by LAW1. The solution must meet the following requirements:
Alert rules must support dimensions.
The time it takes to generate an alert must be minimized.
Alert notifications must be generated only once when the alert is generated and once when the alert is
resolved.
Which signal type should you use when you create the alert rules?
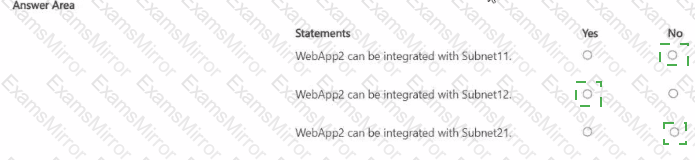
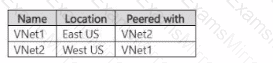
You have an Azure subscription that contains the virtual networks shown in the following table.
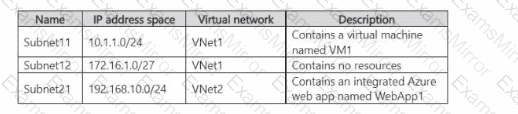
The subscription contains the subnets shown in the following table.
You plan to create an Azure web app named WebApp2 that will have the following configurations:
• Region: East US
• VNet integration: Enabled
• Scale out; Autoscale to up to 10 instances
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

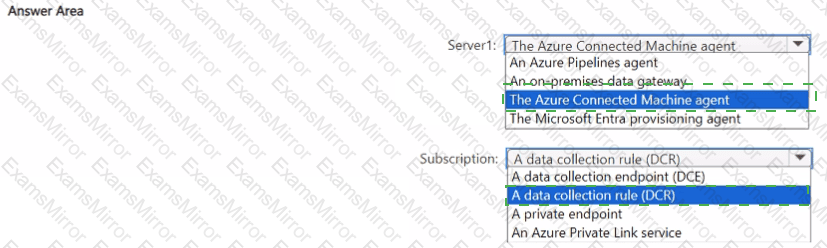
You have an on-premises server named Server1.
You have an Azure subscription that contains a Microsoft Sentinel workspace named Sentinel 1.
You install the Windows Firewall solution in Sentinel1.
You need to use Microsoft Sentinel to monitor Windows Defender Firewall on Server1.
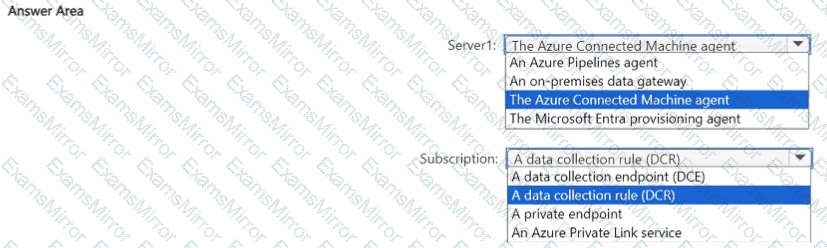
What should you install on Server1, and what should you create in the Azure subscription? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
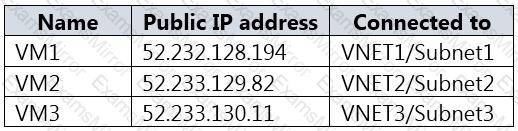
You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table.
The virtual network subnets have service endpoints defined as shown in the following table.
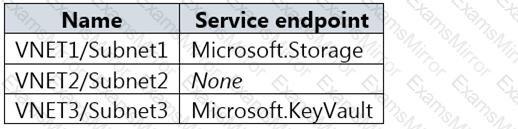
You configure the following Firewall and virtual networks settings for storage1:
Allow access from: Selected networks
Virtual networks: VNET3\Subnet3
Firewall – Address range: 52.233.129.0/24
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.