Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the MuleSoft Certified Developer MCD-Level-2 Questions and answers with ExamsMirror
Exam MCD-Level-2 Premium Access
View all detail and faqs for the MCD-Level-2 exam
644 Students Passed
84% Average Score
97% Same Questions
Which pattern should be used to invoke multiple HTTP APIs in parallel and roll back failed requests in sequence?
A developer deploys an API to CloudHub and applies an OAuth policy on API Manager. During testing, the API response is slow, so the developer reconfigures the API so that the out-of-the-box HTTP Caching policy is applied first, and the OAuth API policy is applied second.
What will happen when an HTTP request is received?
Refer to the exhibit.
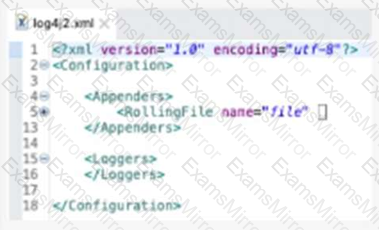
What action must be performed to log all the errors raised by the VM Connector?
A Mule API receives a JSON payload and updates the target system with the payload. The developer uses JSON schemas to ensure the data is valid.
How can the data be validation before posting to the target system?
When implementing a synchronous API where the event source is an HTTP Listener, a developer needs to return the same correlation ID back to the caller in the HTTP response header.
How can this be achieved?
Refer to the exhibits.
Bioinfo System API is implemented and published to Anypoint Exchange. A developer wants to invoke this API using its REST Connector.
What should be added to the POM?
A)
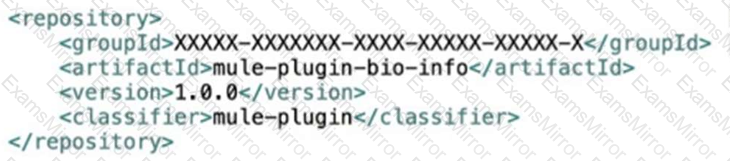
B)
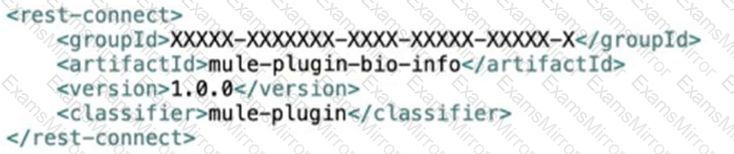
C)
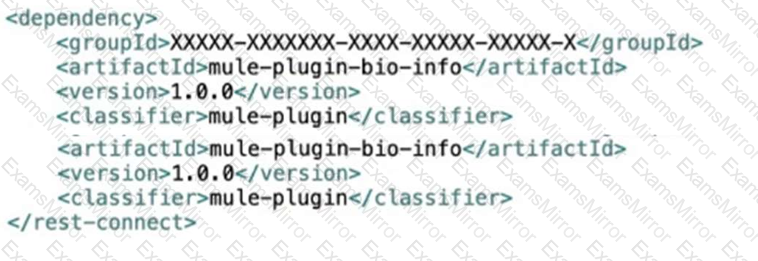
D)
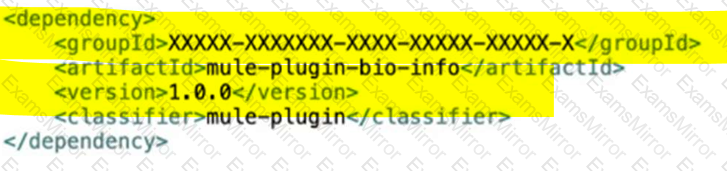
E)
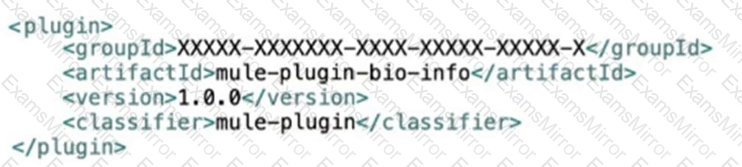
A mule application exposes and API for creating payments. An Operations team wants to ensure that the Payment API is up and running at all times in production.
Which approach should be used to test that the payment API is working in production?
A Mule implementation uses a HTTP Request within an Unit Successful scope to connect to an API.
How should a permanent error response like HTTP:UNAUTHORIZED be handle inside Until Successful to reduce latency?
Two APIs are deployed to a two-node on-prem cluster. Due to a requirements change, the two APIs must communicate to exchange data asynchronously.
Which statement is true about using mutual TLS to secure an application?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
