Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Oracle Linux Administration 1z0-106 Questions and answers with ExamsMirror
Exam 1z0-106 Premium Access
View all detail and faqs for the 1z0-106 exam
716 Students Passed
87% Average Score
93% Same Questions
Examine this segment of /etc/rsyslog.conf:
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don’t log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
Now examine this log output:
less
Nov 9 20:32:16 server02 sudo[4570]: pam_unix(sudo:session): session opened for user opc (uid=0)
Nov 9 20:32:17 server02 sudo[4570]: pam_unix(sudo:session): session closed
Nov 9 20:32:24 server02 unix_chkpwd[4661]: password check failed for user
Nov 9 20:32:24 server02 su[4581]: pam_unix(su:auth): authentication failed; logname= uid=1000 euid=0 tty=pts/0 ruser=opc rhost= user=root
Which setting enabled the reporting of this log file output?
Which two are true about using Ksplice?
Examine this content from /etc/chrony.conf:
...
pool pool.ntp.org offline
driftfile /var/lib/chrony/drift
keyfile /etc/chrony.keys
...
Which statement is true about pool.ntp.org?
Which two default user account settings are contained in /etc/login.defs?
Examine these commands and output:
# cat /etc/auto.master
/net -hosts
/- auto.direct ro
# cat /etc/auto.direct
/nfs1 host01:/export/share1
/nfs2 -sync host01:/export/share2
/nfs3 host02:/export/share3
Automounter must be used to mount these filesystems. Which mount options will it use?
Examine these Kubernetes components:
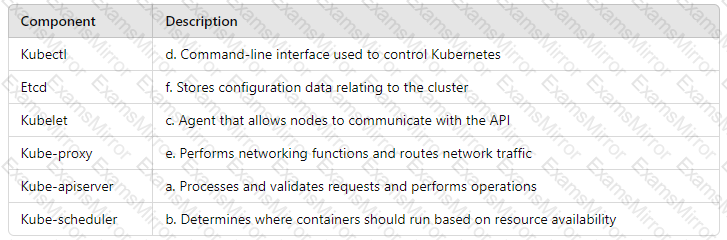
Which option correctly matches the components with their description?
Examine this command and output:
# cat deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
selector:
matchLabels:
app: nginx
replicas: 2
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
Now examine this command which executes successfully:
$ kubectl create -f deployment.yaml
Which two statements are true?
Which three statements are true about the journalctl command?
Examine this command:
# ssh -L 5011:127.0.0.1:80 bob@10.10.2.20 -f sleep 30
Which two are true upon execution?
Which two statements are true about container technology?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
