Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Paloalto Networks Network Security Administrator NetSec-Generalist Questions and answers with ExamsMirror
Exam NetSec-Generalist Premium Access
View all detail and faqs for the NetSec-Generalist exam
841 Students Passed
90% Average Score
90% Same Questions
What is the most efficient way in Strata Cloud Manager (SCM) to apply a Security policy to all ten firewalls in one data center?
Which action must a firewall administrator take to incorporate custom vulnerability signatures into current Security policies?
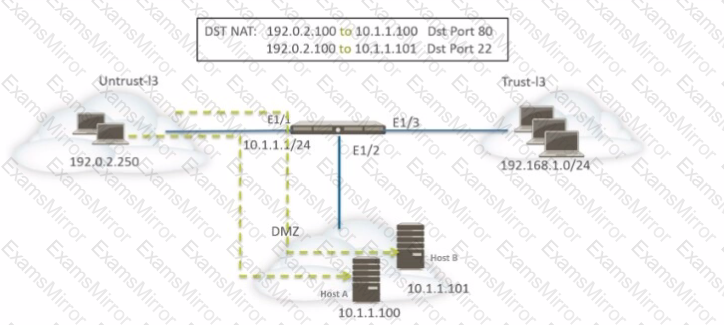
A network administrator is using DNAT to map two servers to one public IP address. Traffic will be directed to a specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.
Which two sets of Security policy rules will accomplish this configuration? (Choose two.)
Which functionality does an NGFW use to determine whether new session setups are legitimate or illegitimate?
What is the primary role of Advanced DNS Security in protecting against DNS-based threats?
What is the main security benefit of adding a CN-Series firewall to an existing VM-Series firewall deployment when the customer is using containers?
A company uses Prisma Access to provide secure connectivity for mobile users to access its corporate-sanctioned Google Workspace and wants to block access to all unsanctioned Google Workspace environments.
What would an administrator configure in the snippet to achieve this goal?
Which feature is available in both Panorama and Strata Cloud Manager (SCM)?
A company currently uses Prisma Access for its mobile users. A use case is discovered in which mobile users will need to access an internal site, but there is no existing network communication between the mobile users and the internal site.
Which Prisma Access functionality needs to be deployed to enable routing between the mobile users and the internal site?
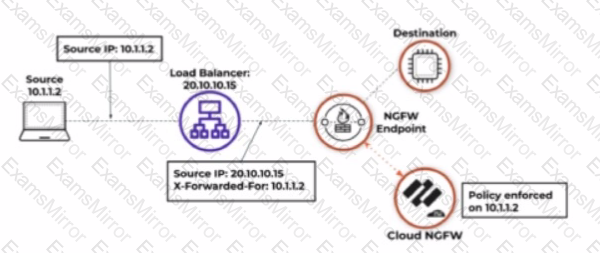
Based on the image below, which source IP address will be seen in the data filtering logs of the Cloud NGFW for AWS with the default rulestack settings?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
