Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Paloalto Networks Certified Cybersecurity Associate PCCET Questions and answers with ExamsMirror
Exam PCCET Premium Access
View all detail and faqs for the PCCET exam
791 Students Passed
95% Average Score
90% Same Questions
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
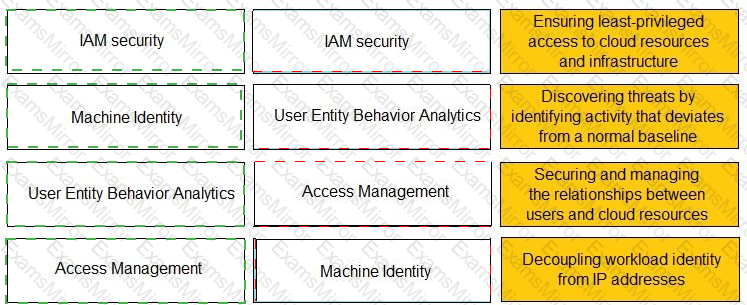
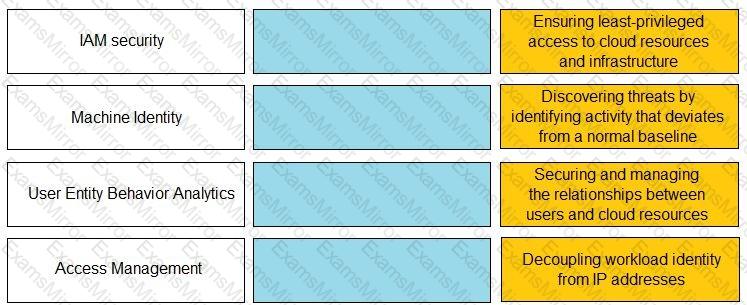
Match the Identity and Access Management (IAM) security control with the appropriate definition.
On an endpoint, which method should you use to secure applications against exploits?
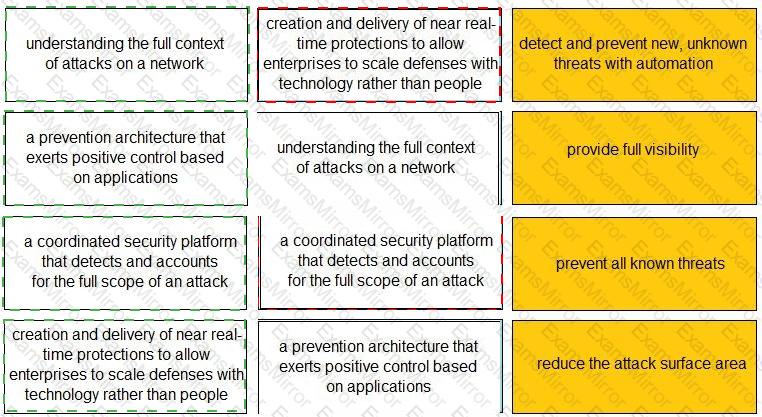
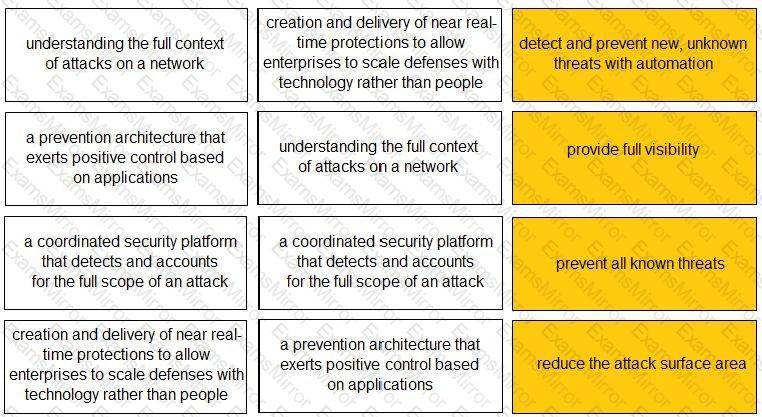
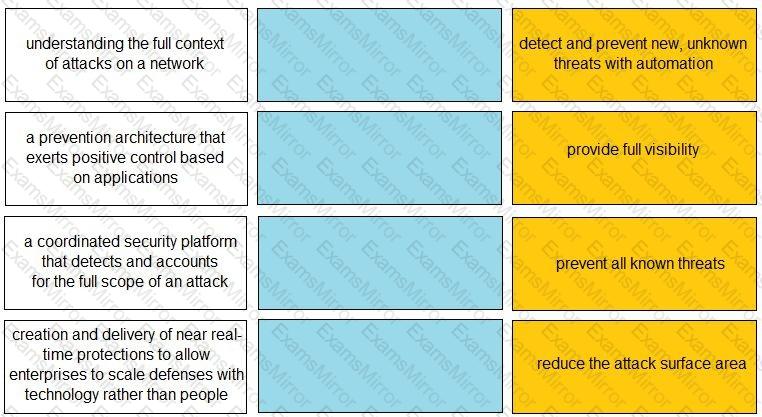
Match each description to a Security Operating Platform key capability.
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
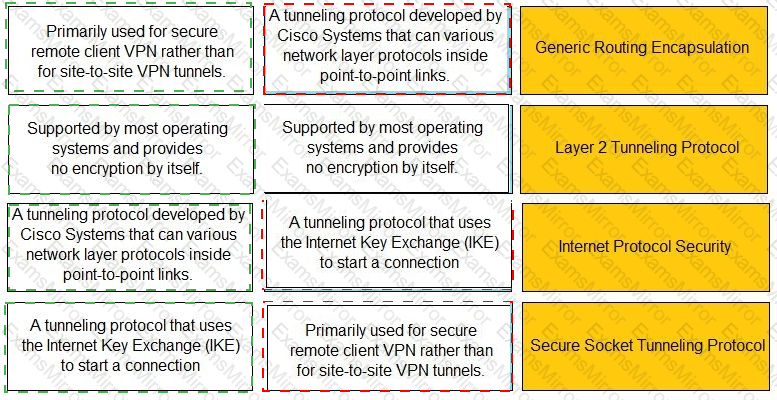
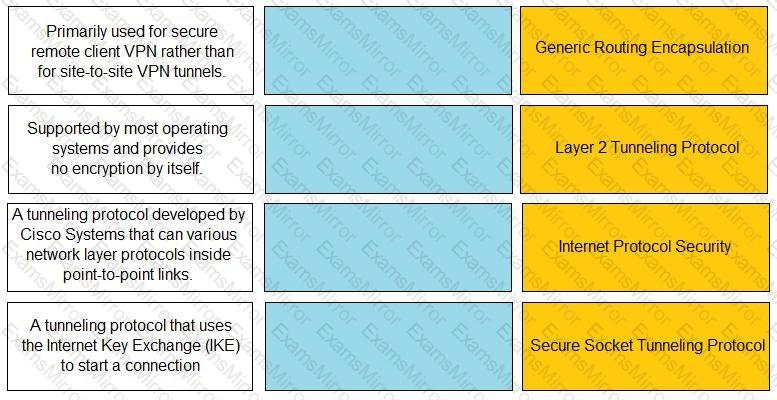
Match the description with the VPN technology.
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which endpoint tool or agent can enact behavior-based protection?
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads.
What deployment options do you have available? (Choose two.)
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.