Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Paloalto Networks Security Operations XSIAM-Engineer Questions and answers with ExamsMirror
Exam XSIAM-Engineer Premium Access
View all detail and faqs for the XSIAM-Engineer exam
731 Students Passed
86% Average Score
93% Same Questions
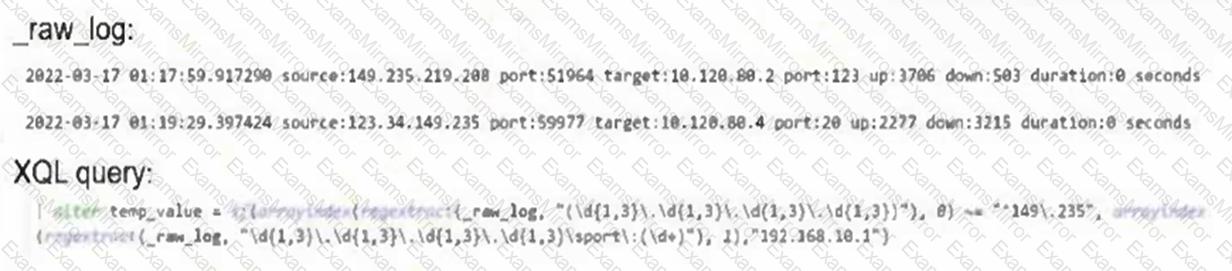
Based on the _raw_log and XQL query information below, what will be the result(s) of the temp_value?
Which common issue can result in sudden data ingestion loss for a data source that was previously successful?
Administrators from Building 3 have been added to Cortex XSIAM to perform limited functions on a subset of endpoints. Custom roles have been created and applied to the administrators to limit their permissions, but their access should also be constrained through the principle of least privilege according to the endpoints they are allowed to manage. All endpoints are part of an endpoint group named "Building3," and some endpoints may also be members of other endpoint groups.
Which technical control will restrict the ability of the administrators to manage endpoints outside of their area of responsibility, while maintaining visibility to Building 3's endpoints?
An application which ingests custom application logs is hosted in an on-premises virtual environment on an Ubuntu server, and it logs locally to a .csv file.
Which set of actions will allow the ingestion of the .csv logs into Cortex XSIAM directly from the server?
An application which ingests custom application logs is hosted in an on-premises virtual environment on an Ubuntu server, and it logs locally to a .csv file.
Which set of actions will allow the ingestion of the .csv logs into Cortex XSIAM directly from the server?
In the Incident War Room, which command is used to update incident fields identified in the incident layout?
Which cytool command will look up the policy being applied to a Cortex XDR agent?
Which action will prevent the automatic extraction of indicators such as IP addresses and URLs from a script's output?
A Cortex XSIAM engineer at a SOC downgrades a critical threat intelligence content pack from the Cortex Marketplace while performing routine maintenance. As a result, the SOC team loses access to the latest threat intelligence data.
Which action will restore the functionality of the content pack to its previously installed version?
What is the function of the "MODEL" section when creating a data model rule?
Which section of a parsing rule defines the newly created dataset?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
