Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Salesforce MuleSoft MuleSoft-Platform-Architect-I Questions and answers with ExamsMirror
Exam MuleSoft-Platform-Architect-I Premium Access
View all detail and faqs for the MuleSoft-Platform-Architect-I exam
662 Students Passed
94% Average Score
90% Same Questions
Select the correct Owner-Layer combinations from below options
Which of the below, when used together, makes the IT Operational Model effective?
An API experiences a high rate of client requests (TPS) vwth small message paytoads. How can usage limits be imposed on the API based on the type of client application?
An online store's marketing team has noticed an increase in customers leaving online baskets without checking out. They suspect a technology issue is at the root cause of the baskets being left behind. They approach the Center for Enablement to ask for help identifying the issue. Multiple APIs from across all the layers of their application network are involved in the shopping application.
Which feature of the Anypoint Platform can be used to view metrics from all involved APIs at the same time?
A system API has a guaranteed SLA of 100 ms per request. The system API is deployed to a primary environment as well as to a disaster recovery (DR) environment, with different DNS names in each environment. An upstream process API invokes the system API and the main goal of this process API is to respond to client requests in the least possible time. In what order should the system APIs be invoked, and what changes should be made in order to speed up the response time for requests from the process API?
A company deployed an API to a single worker/replica in the shared cloud in the U.S. West Region.
What happens when the Availability Zone experiences an outage?
A Mule application exposes an HTTPS endpoint and is deployed to the CloudHub Shared Worker Cloud. All traffic to that Mule application must stay inside the AWS VPC.
To what TCP port do API invocations to that Mule application need to be sent?
An organization requires several APIs to be secured with OAuth 2.0, and PingFederate has been identified as the identity provider for API client authorization, The
PingFederate Client Provider is configured in access management, and the PingFederate OAuth 2.0 Token Enforcement policy is configured for the API instances required by the
organization. The API instances reside in two business groups (Group A and Group B) within the Master Organization (Master Org).
What should be done to allow API consumers to access the API instances?
An eCommerce company is adding a new Product Details feature to their website, A customer will launch the product catalog page, a new Product Details link will
appear by product where they can click to retrieve the product detail description. Product detail data is updated with product update releases, once or twice a year, Presently
the database response time has been very slow due to high volume.
What action retrieves the product details with the lowest response time, fault tolerant, and consistent data?
What API policy would be LEAST LIKELY used when designing an Experience API that is intended to work with a consumer mobile phone or tablet application?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.

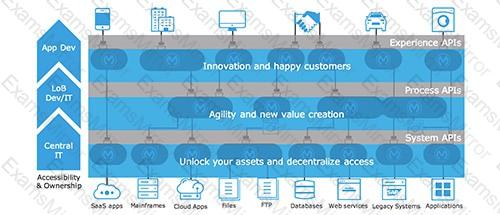
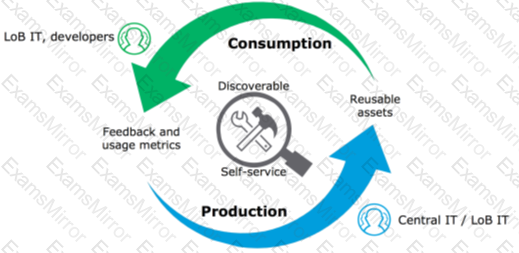 Diagram, arrow
Description automatically generated
Diagram, arrow
Description automatically generated