Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Trend Micro Deep Security Deep-Security-Professional Questions and answers with ExamsMirror
Exam Deep-Security-Professional Premium Access
View all detail and faqs for the Deep-Security-Professional exam
709 Students Passed
89% Average Score
97% Same Questions
Which Protection Modules can make use of a locally installed Smart Protection Server?
Which of the following statements is true regarding Event Tagging?
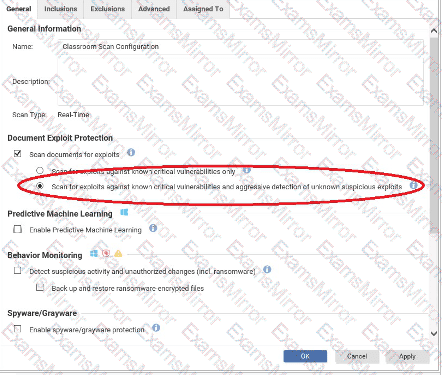
Based on the configuration setting highlighted in the exhibit, what behavior can be expected during a malware scan?
What is the purpose of the Deep Security Relay?
Where does Deep Security Manager store the credentials it uses to access the database?
What is the result of performing a Reset operation on a Deep Security Agent?
Which of the following VMware components is not required to enable agentless protection using Deep Security.
Which of the following statements is false regarding the Log Inspection Protection Module?
Which of the following are valid methods for forwarding Event information from Deep Secu-rity? Select all that apply.
Which of the following are valid methods for pre-approving software updates to prevent Ap-plication Control Events from being triggered by the execution of the modified software? Select all that apply.
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
