Cyber Monday Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the VMware NSX-T Data Center Security Skills 2023 5V0-41.21 Questions and answers with ExamsMirror
Exam 5V0-41.21 Premium Access
View all detail and faqs for the 5V0-41.21 exam
598 Students Passed
92% Average Score
92% Same Questions
An NSX administrator has been tasked with deploying a NSX Edge Virtual machine through an ISO image.
Which virtual network interface card (vNIC) type must be selected while creating the NSX Edge VM allow participation in overlay and VLAN transport zones?
An administrator needs to configure their NSX-T logging to audit changes on firewall security policy. The administrator Is using the following command from NSX-T3.1 documentation :

Which Message ID from the following list will allow the administrator to track changes on firewall security rules?
Which of the following are the local user accounts used to administer NSX-T Data Center?
A security administrator recently enabled Guest Introspection on NSX-T Data Center.
Which would be a reason none of the Microsoft Windows based VMs are reporting any information?
An organization wants to add security controls for contractor virtual desktops. Which statement Is true when configuring an NSX Identity firewall rule?
An NSX administrator has turned on logging for the distributed firewall rule. On an ESXi host, where will the logs be stored?
At which OSI Layer do Next Generation Firewalls capable of analyzing application traffic operate?
An administrator wants to use Distributed Intrusion Detection. How is this implemented in an NSX-T Data Center?
Reference the CLI output.
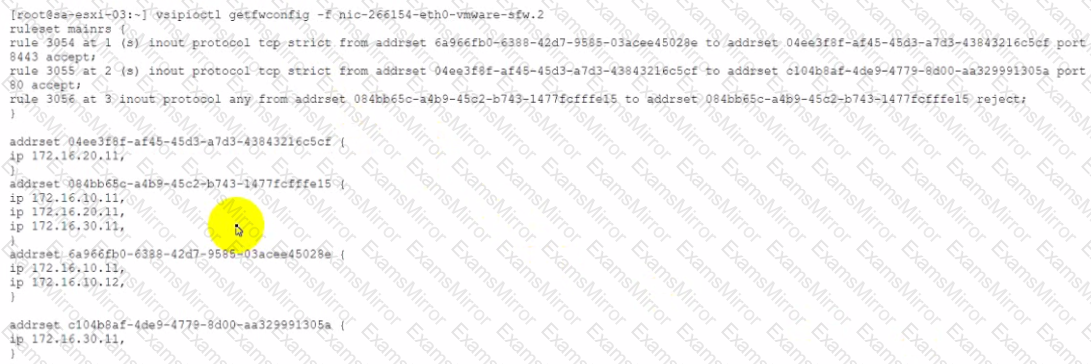
What is the source IP address in the distributed firewall rule to accept HTTP traffic?
A company's CTO has requested that all logging should be enabled for all NSX-T Data Center Distributed Firewall rules. What should be considered prior to executing this request?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
