Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CCST 100-160 Questions and answers with ExamsMirror
Exam 100-160 Premium Access
View all detail and faqs for the 100-160 exam
650 Students Passed
87% Average Score
96% Same Questions
Which two basic metrics should be taken into consideration when assigning a severity to a vulnerability during an assessment?(Choose 2.)
Which two passwords follow strong password policy guidelines?(Choose 2.)
Which wireless security protocol provides the strongest protection for a home or small business network?
You need to transfer configuration files to a router across an unsecured network.
Which protocol should you use to encrypt the files in transit?
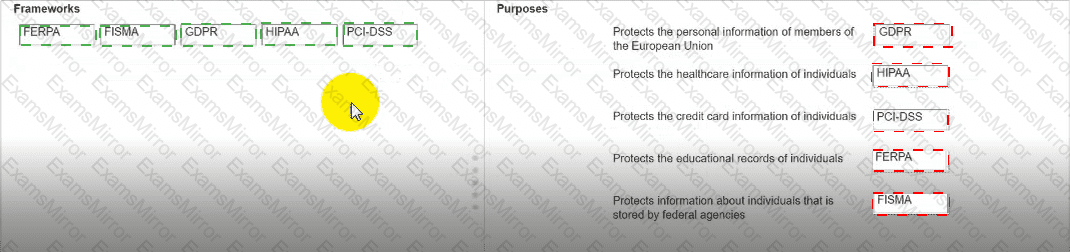
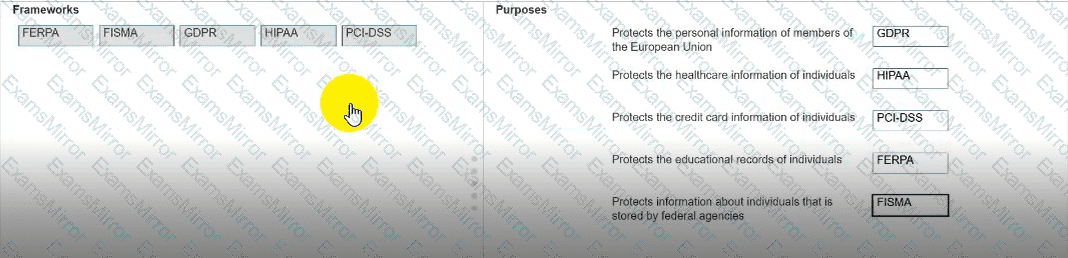
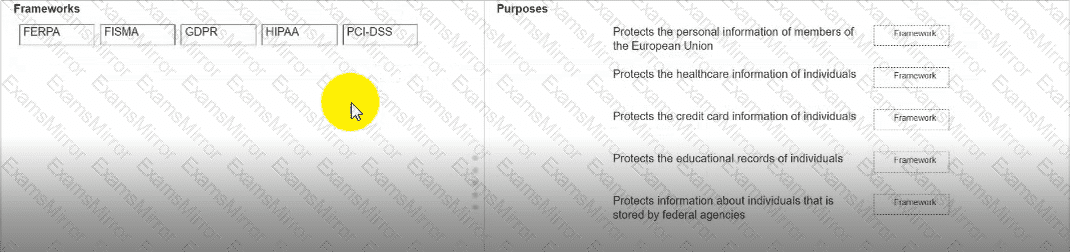
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a successful login to a privileged account. What is the most appropriate next step?
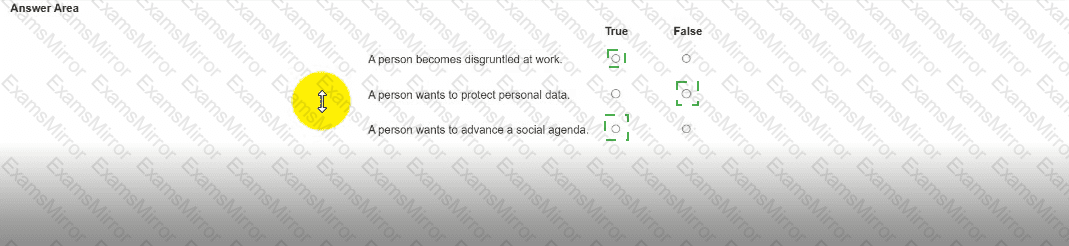
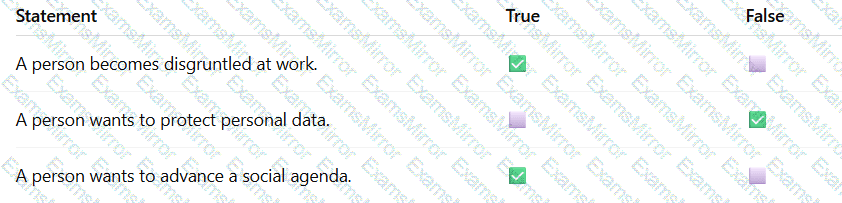
For each statement, selectTrueif it is a common motivation to commit cyber attacks orFalseif it is not.
Note: You will receive partial credit for each correct selection.

Which security measure can prevent unauthorized devices from automatically connecting to a corporate network through unused switch ports?
Your company is creating a BYOD policy to allow employees to join their personal smartphones to the company network.
Which three requirements are commonly included in a BYOD policy?(Choose 3.)
How does sandboxing help with the analysis of malware?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.