Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CyberOps Professional 300-215 Questions and answers with ExamsMirror
Exam 300-215 Premium Access
View all detail and faqs for the 300-215 exam
762 Students Passed
95% Average Score
91% Same Questions
Refer to the exhibit.
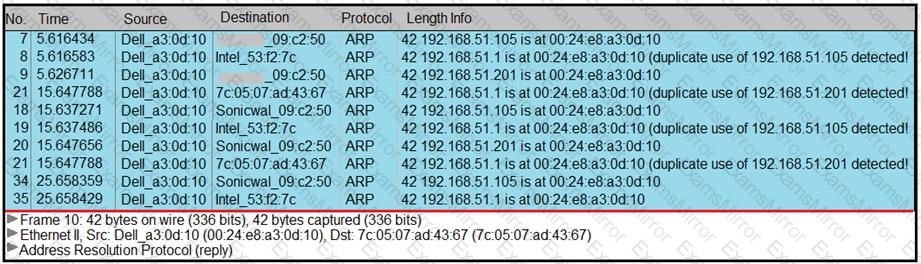
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
What are two features of Cisco Secure Endpoint? (Choose two.)

Refer to the exhibit.
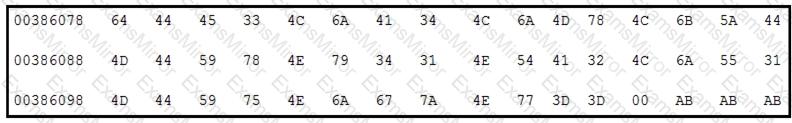
Which encoding technique is represented by this HEX string?
During a routine inspection of system logs, a security analyst notices an entry where Microsoft Word initiated a PowerShell command with encoded arguments. Given that the user's role does not involve scripting or advanced document processing, which action should the analyst take to analyze this output for potential indicators of compromise?
Refer to the exhibit.
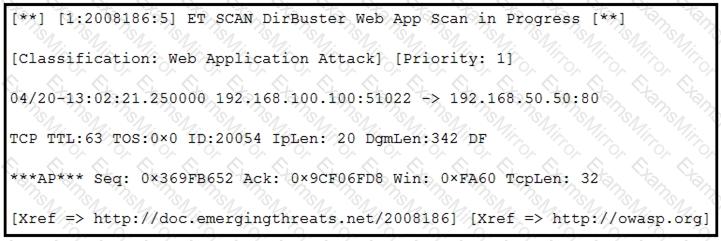
According to the SNORT alert, what is the attacker performing?
Refer to the exhibit.
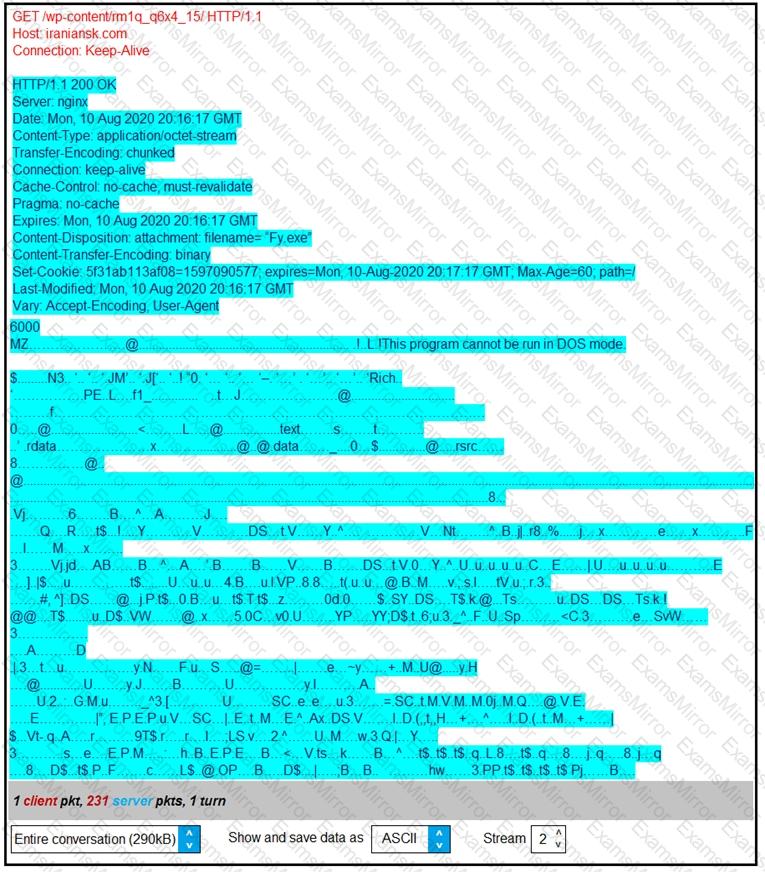
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
An insider scattered multiple USB flash drives with zero-day malware in a company HQ building. Many employees connected the USB flash drives to their workstations. An attacker was able to get access to endpoints from outside, steal user credentials, and exfiltrate confidential information from internal web resources. Which two steps prevent these types of security incidents in the future? (Choose two.)
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
