Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CCNP Security 300-740 Questions and answers with ExamsMirror
Exam 300-740 Premium Access
View all detail and faqs for the 300-740 exam
660 Students Passed
84% Average Score
93% Same Questions

Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to prevent restricted users from being able to browse any business or mobile phone shopping websites. The indicated policy was applied; however, the restricted users still can browse on the mobile phone shopping websites during business hours. What should be done to meet the requirement?
What does the MITRE ATT&CK framework catalog?
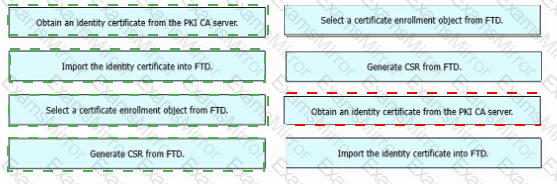
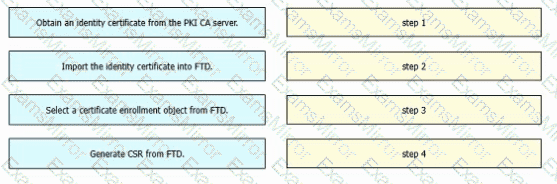
An engineer must configure certificate-based authentication in a cloud-delivered Cisco Secure Firewall Management Center. Drag and drop the steps from left to right to manually enroll certificates on a Cisco Secure Firewall Threat Defense Virtual device.

Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report. Which activity does the output verify?
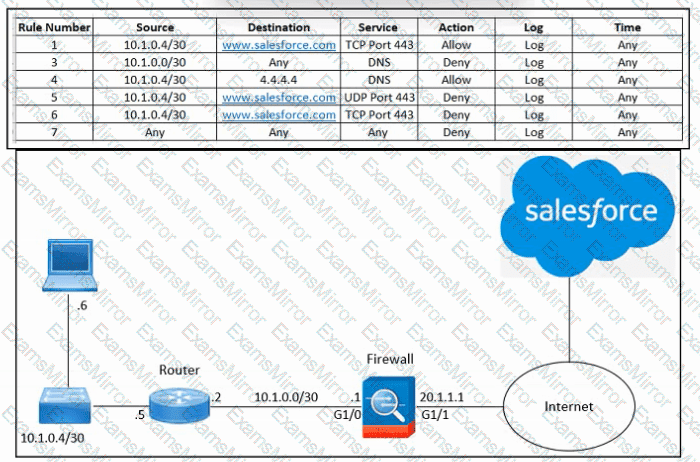
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution; however, the client still cannot access the URL. What should be done to meet the requirements?
What must be automated to enhance the efficiency of a security team response?
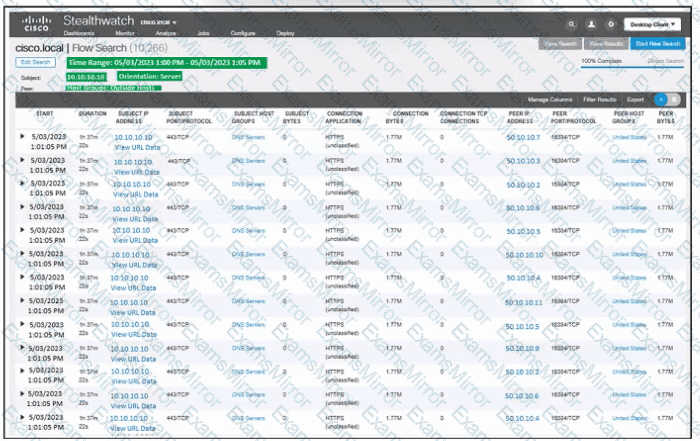
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?
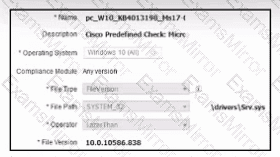
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network. Which posture condition must the engineer configure?
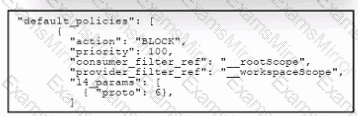
Refer to the exhibit. An engineer configured a default segmentation policy in Cisco Secure Workload to block SMTP traffic. During testing, it is observed that the SMTP traffic is still allowed. Which action must the engineer take to complete the configuration?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.