Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the CompTIA CASP CAS-005 Questions and answers with ExamsMirror
Exam CAS-005 Premium Access
View all detail and faqs for the CAS-005 exam
656 Students Passed
84% Average Score
98% Same Questions
An organization determines existing business continuity practices areinadequateto support critical internal process dependencies during a contingency event. Acompliance analystwants the Chief Information Officer (CIO) to identify the level ofresidual riskthat is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
During a periodic internal audit, a company identifies a few new, critical security controls that are missing. The company has a mature risk management program in place, and the following requirements must be met:
The stakeholders should be able to see all the risks.
The risks need to have someone accountable for them.
Which of the following actions should the GRC analyst take next?
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?
A news organization wants to implement workflows that allow users to request that untruthful data be retraced and scrubbed from online publications to comply with the right to be forgotten Which of the following regulations is the organization most likely trying to address'
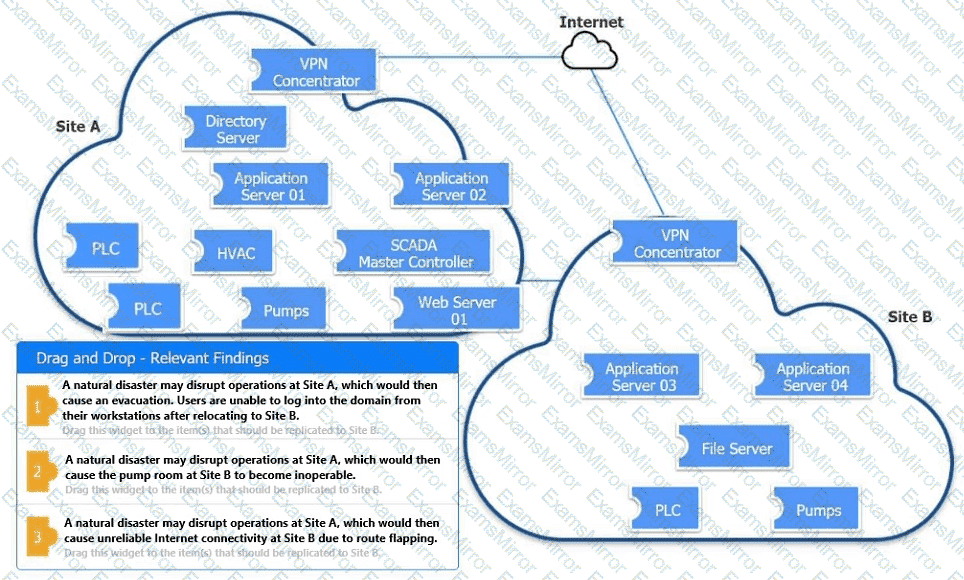
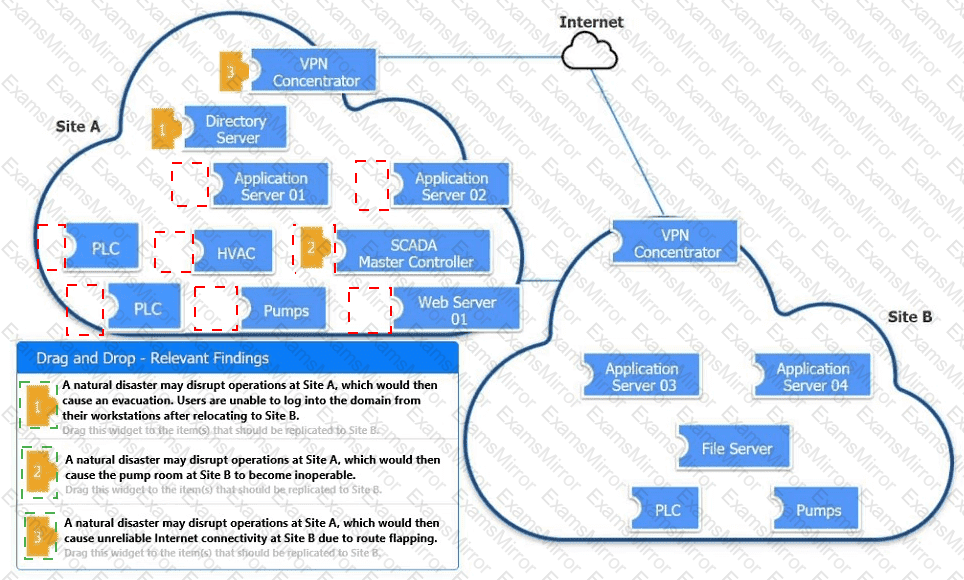
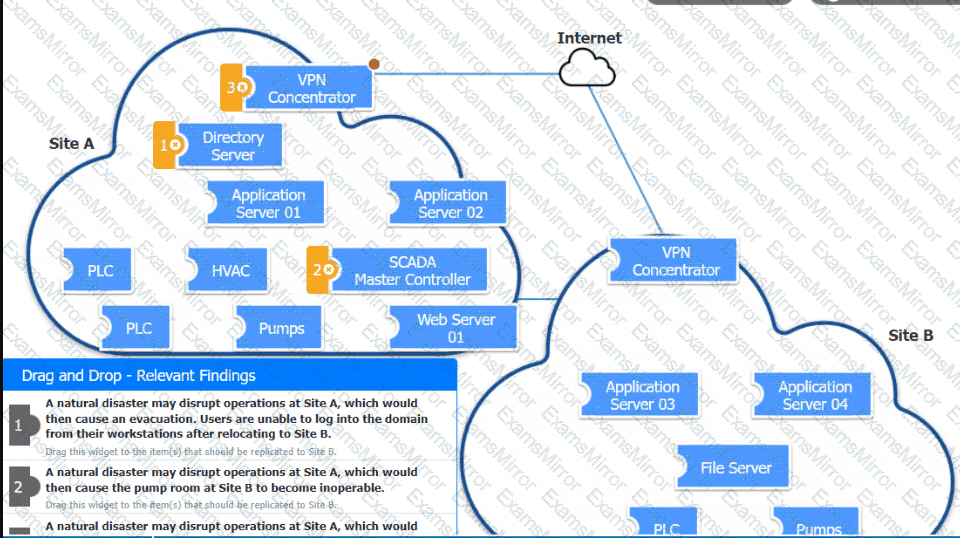
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
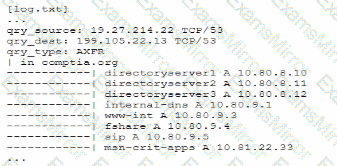
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
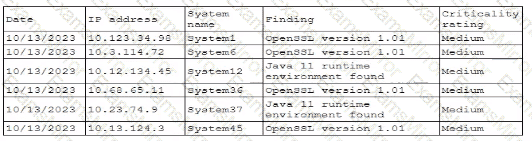
Which of the following actions would address the root cause of this issue?
A company implemented a NIDS and a NIPS on the most critical environments. Since this implementation, the company has been experiencing network connectivity issues. Which of the following should the security architect recommend for a new NIDS/NIPS implementation?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
An external threat actor attacks public infrastructure providers. In response to the attack and during follow-up activities, various providers share information obtained during response efforts. After the attack, energy sector companies share their status and response data:
Company
SIEM
UEBA
DLP
ISAC Member
TIP Integration
Time to Detect
Time to Respond
1
Yes
No
Yes
Yes
Yes
10 minutes
20 minutes
2
Yes
Yes
Yes
Yes
No
20 minutes
40 minutes
3
Yes
Yes
No
No
Yes
12 minutes
24 minutes
Which of thefollowing is the most important issue to address to defend against future attacks?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.

 A computer screen shot of a diagram Description automatically generated
A computer screen shot of a diagram Description automatically generated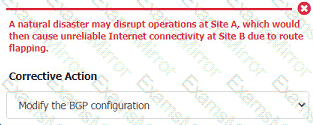 A screenshot of a computer error Description automatically generated
A screenshot of a computer error Description automatically generated