Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the CompTIA PenTest+ PT0-003 Questions and answers with ExamsMirror
Exam PT0-003 Premium Access
View all detail and faqs for the PT0-003 exam
728 Students Passed
89% Average Score
94% Same Questions
During a pre-engagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
Which of the following OT protocols sends information in cleartext?
A penetration tester is performing an assessment focused on attacking the authentication identity provider hosted within a cloud provider. During the reconnaissance phase, the tester finds that the system is using OpenID Connect with OAuth and has dynamic registration enabled. Which of the following attacks should the tester try first?
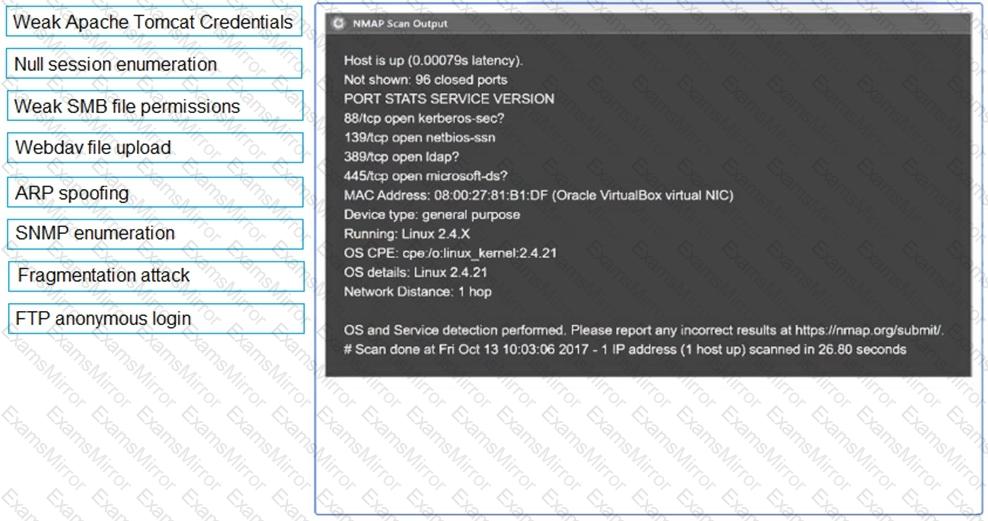
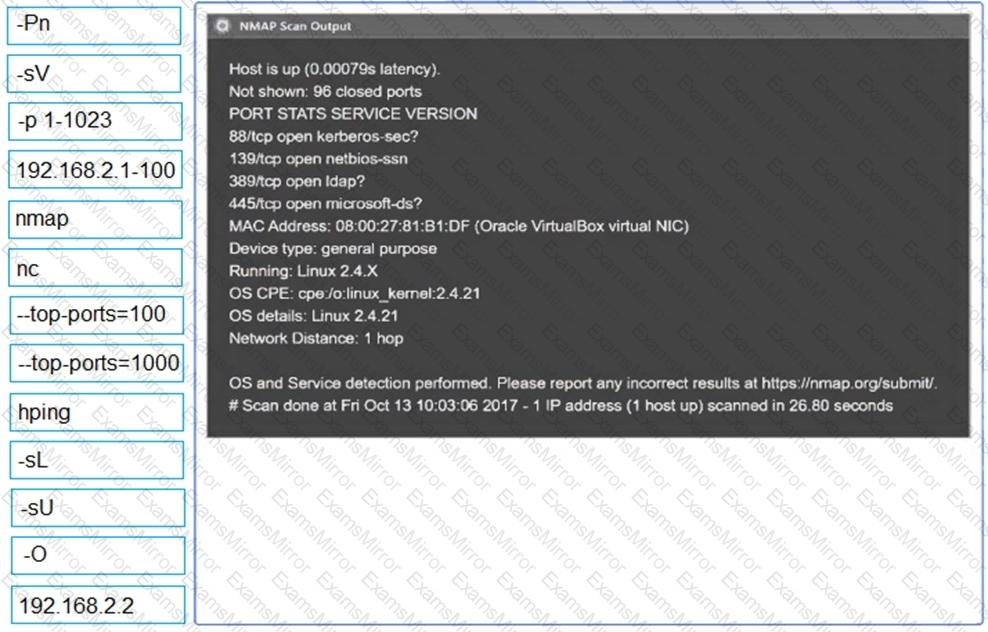
A penetration tester identifies the following open ports during a network enumeration scan:
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
27017/tcp open mongodb
50123/tcp open ms-rpc
Which of the following commands did the tester use to get this output?
A penetration testing team wants to conduct DNS lookups for a set of targets provided by the client. The team crafts a Bash script for this task. However, they find a minor error in one line of the script:
1 #!/bin/bash
2 for i in $(cat example.txt); do
3 curl $i
4 done
Which of the following changes should the team make to line 3 of the script?
A penetration tester downloads a JAR file that is used in an organization's production environment. The tester evaluates the contents of the JAR file to identify potentially vulnerable components that can be targeted for exploit. Which of the following describes the tester's activities?
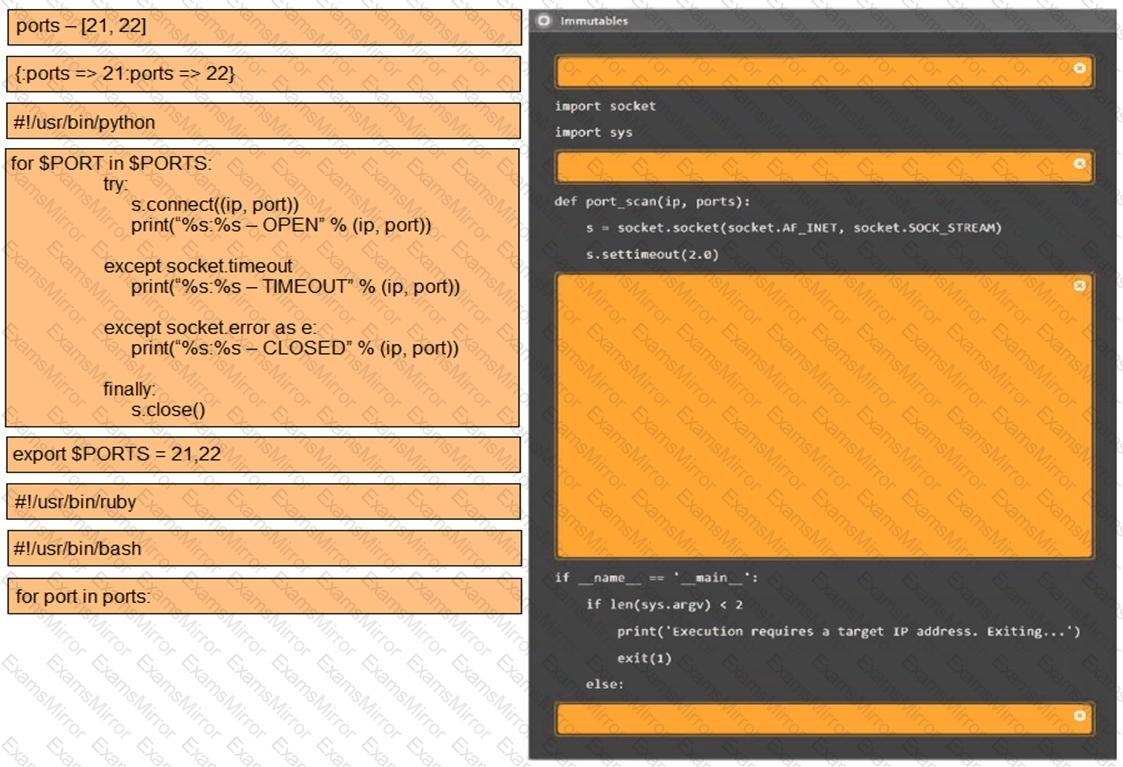
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
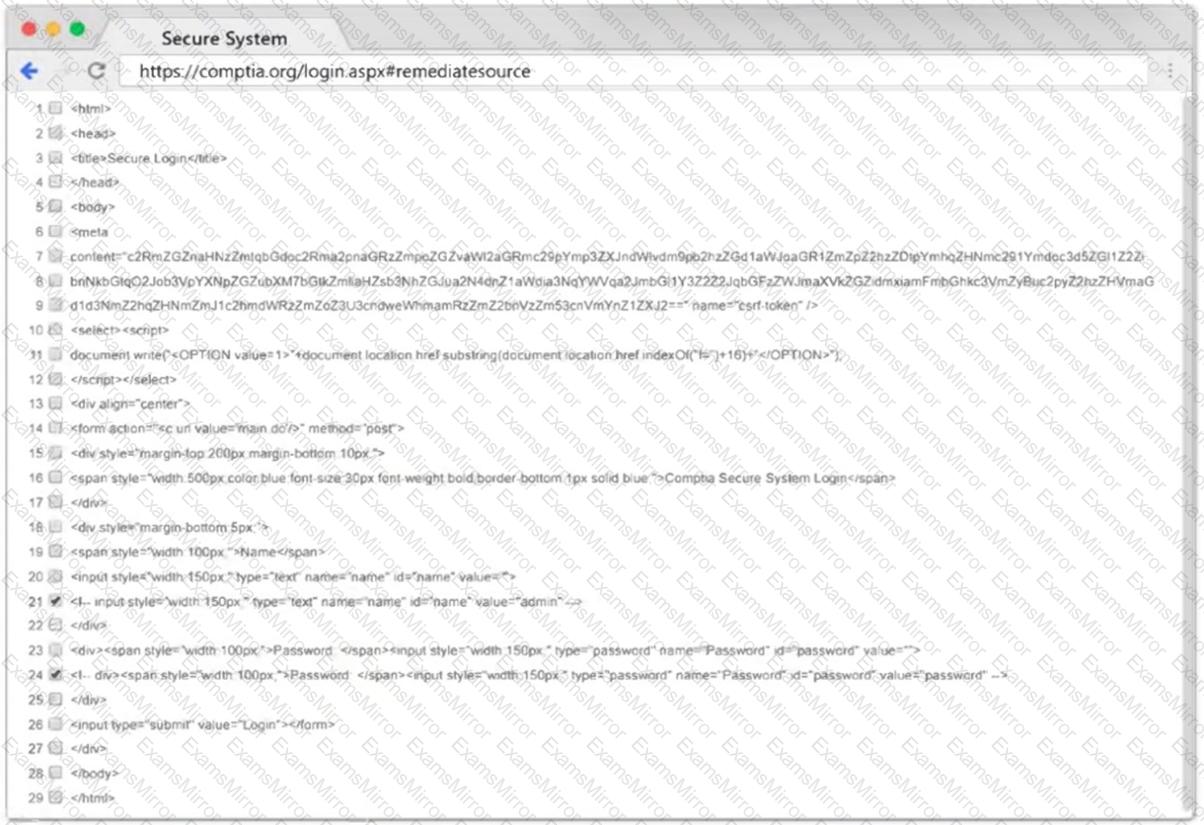
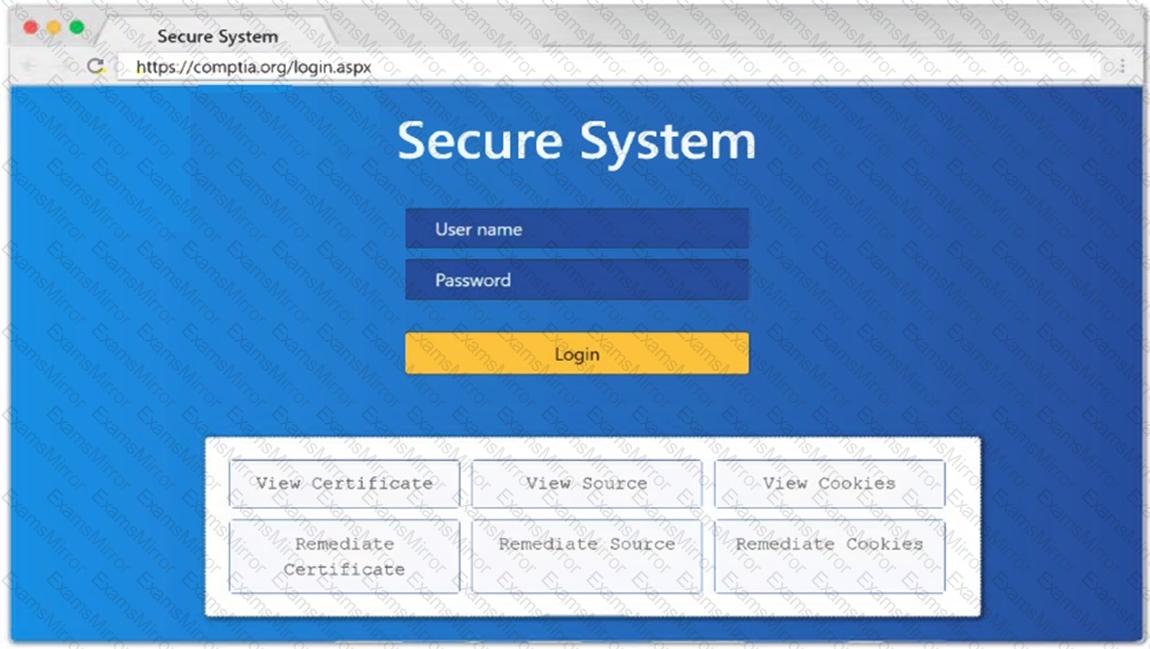
A penetration tester sets up a C2 (Command and Control) server to manage and control payloads deployed in the target network. Which of the following tools is the most suitable for establishing a robust and stealthy connection?
During a penetration test, a junior tester uses Hunter.io for an assessment and plans to review the information that will be collected. Which of the following describes the information the junior tester will receive from the Hunter.io tool?
Which of the following elements of a penetration test report can be used to most effectively prioritize the remediation efforts for all the findings?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
