Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Security Certification: GASF GCED Questions and answers with ExamsMirror
Exam GCED Premium Access
View all detail and faqs for the GCED exam
665 Students Passed
93% Average Score
96% Same Questions
What is needed to be able to use taskkill to end a process on remote system?
Why would a Cisco network device with the latest updates and patches have the service config setting enabled, making the device vulnerable to the TFTP Server Attack?
A legacy server on the network was breached through an OS vulnerability with no patch available. The server is used only rarely by employees across several business units. The theft of information from the server goes unnoticed until the company is notified by a third party that sensitive information has been posted on the Internet. Which control was the first to fail?
What does the following WMIC command accomplish?
process where name=’malicious.exe’ delete
A security device processes the first packet from 10.62.34.12 destined to 10.23.10.7 and recognizes a malicious anomaly. The first packet makes it to 10.23.10.7 before the security devices sends a TCP RST to 10.62.34.12. What type of security device is this?
What attack was indicated when the IDS system picked up the following text coming from the Internet to the web server?
select user, password from user where user= “jdoe” and password= ‘myp@55!’ union select “text”,2 into outfile “/tmp/file1.txt” - - ’
Which tasks would a First Responder perform during the Identification phase of Incident Response?
Before re-assigning a computer to a new employee, what data security technique does the IT department use to make sure no data is left behind by the previous user?
Which command is the Best choice for creating a forensic backup of a Linux system?
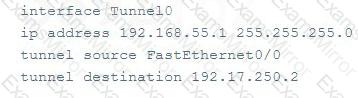
How would an attacker use the following configuration settings?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
