Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the HashiCorp Security Automation Certification HCVA0-003 Questions and answers with ExamsMirror
Exam HCVA0-003 Premium Access
View all detail and faqs for the HCVA0-003 exam
727 Students Passed
85% Average Score
90% Same Questions
Which of the following capabilities can be used when writing a Vault policy? (Select four)
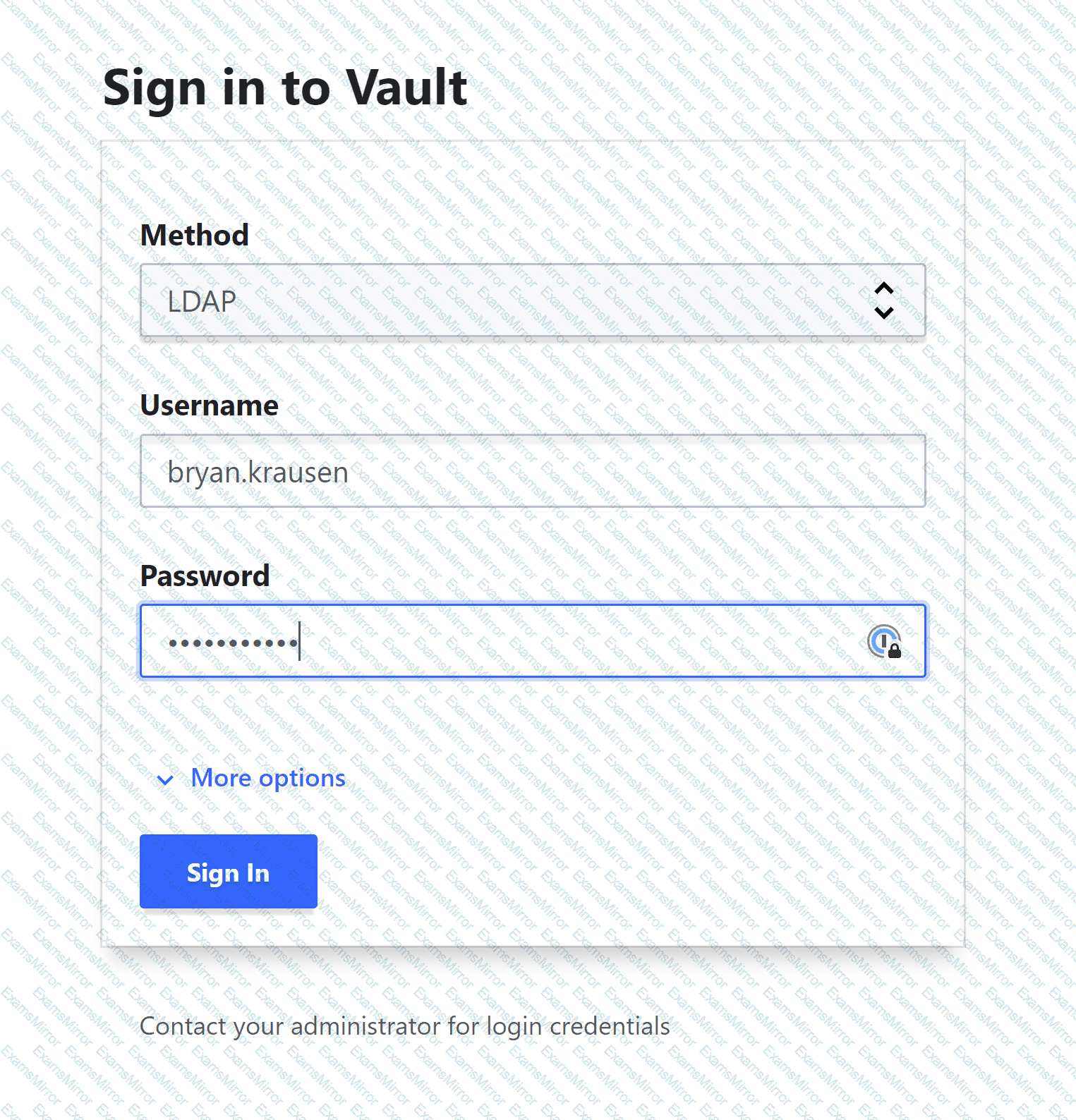
Your organization has enabled the LDAP auth method on the path of corp-auth/. When you access the Vault UI, you cannot log in despite providing the correct credentials. Based on the screenshot below, what action should you take to log in?
Your organization audited an essential application and found it isn’t securely storing data. For added security, auditors recommended encrypting all data before storing it in a backend database, and the application server should not store encryption keys locally. Which secrets engine meets these requirements?
A MySQL server has been deployed on Google Cloud Platform (GCP) to support a legacy application. You want to generate dynamic credentials against this MySQL server rather than use static credentials. What Vault secrets engine would you use to accomplish this?
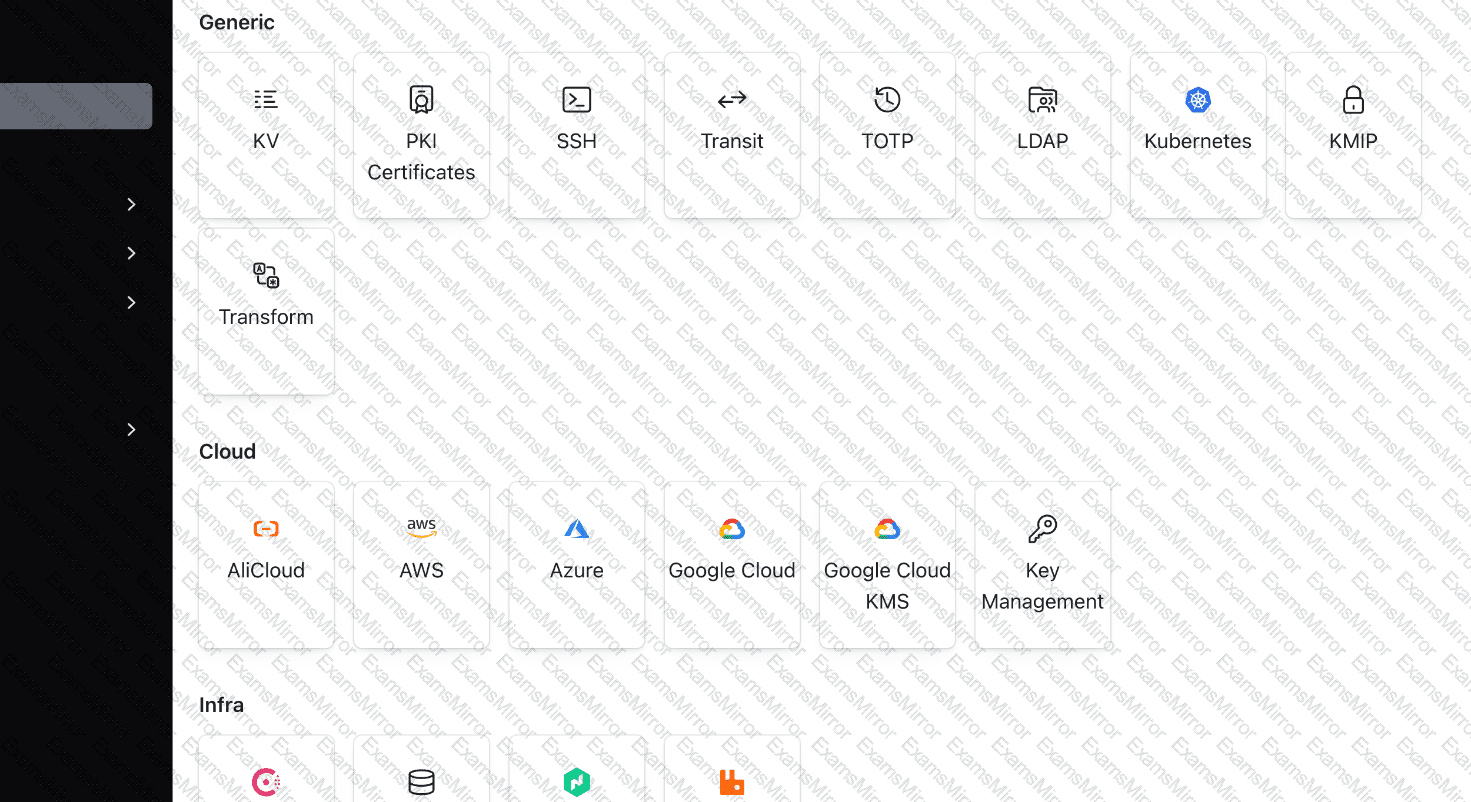
You have logged into the Vault UI and see this screen. What Vault component is being enabled in the screenshot below?
Which of the following are considered benefits of using policies in Vault? (Select three)
You are planning the deployment of your first Vault cluster and have decided to use Integrated Storage as the storage backend. Where do you configure the storage backend to be used by Vault?
There are a few ways in Vault that can be used to obtain a root token. Select the valid methods from the answers below. (Select three)
A security architect is designing a solution to address the "Secret Zero" problem for a Kubernetes-based application that needs to authenticate to HashiCorp Vault. Which approach correctly leverages Vault features to solve this challenge?
A developer has requested access to manage secrets at the path kv/apps/webapp01. You create the policy below which gives them the proper access:
path "kv/apps/webapp01" {
capabilities = ["read", "create", "update", "list"]
}
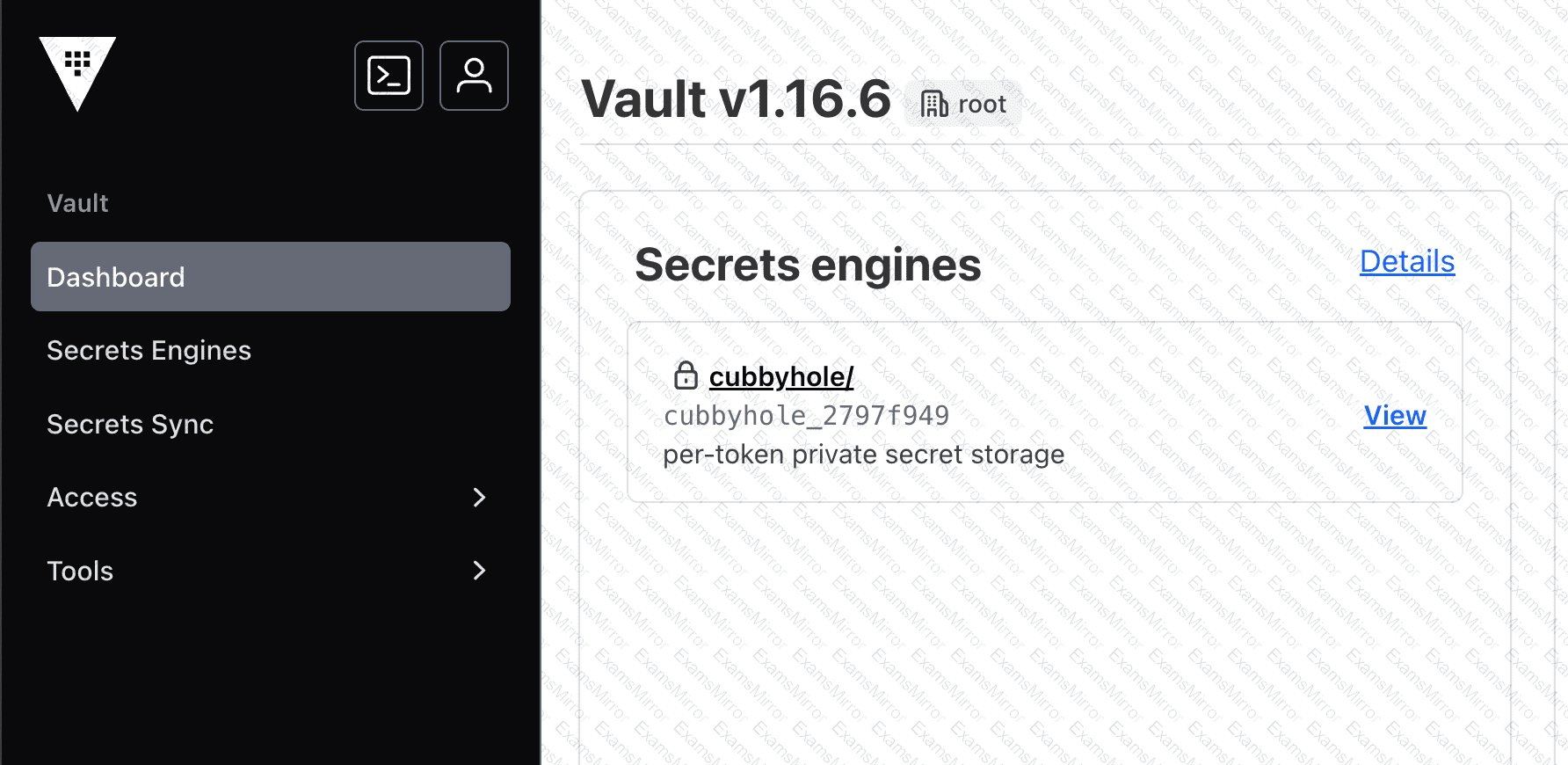
However, when the developer logs in to the Vault UI, they see the following screenshot and cannot access the desired secret. Why can’t the developer see the secrets they need?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
