Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Netskope NCCSA NSK300 Questions and answers with ExamsMirror
Exam NSK300 Premium Access
View all detail and faqs for the NSK300 exam
684 Students Passed
88% Average Score
94% Same Questions
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee. Which two statements are correct in this scenario? (Choose two.)
You recently began deploying Netskope at your company. You are steering all traffic, but you discover that the Real-time Protection policies you created to protect Microsoft OneDrive are not being enforced.
Which default setting in the Ul would you change to solve this problem?
You are asked to ensure that a Web application your company uses is both reachable and decrypted by Netskope. This application is served using HTTPS on port 6443. Netskope is configured with a default Cloud Firewall configuration and the steering configuration is set for All Traffic.
Which statement is correct in this scenario?
Review the exhibit.
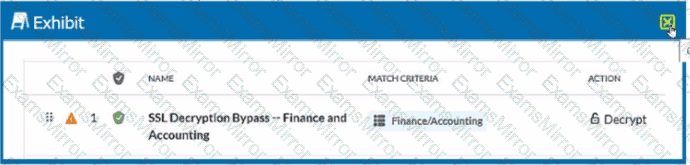
You created an SSL decryption policy to bypass the inspection of financial and accounting Web categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
Given the following:
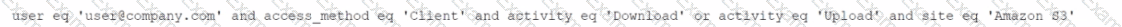
Which result does this Skope IT query provide?
You are consuming Audit Reports as part of a Salesforce API integration. Someone has made a change to a Salesforce account record field that should not have been made and you are asked to venfy the previous value of the structured data field. You have the approximate date and time of the change, user information, and the new field value.
How would you accomplish this task?
You successfully configured Advanced Analytics to identify policy violation trends Upon further investigation, you notice that the activity is NULL. Why is this happening in this scenario?
Your client is an NG-SWG customer. They are going to use the Explicit Proxy over Tunnel (EPoT) steering method. They have a specific list of domains that they do not want to steer to the Netskope Cloud.
What would accomplish this task''
You built a number of DLP profiles for different sensitive data types. If a file contains any of this sensitive data, you want to take the most restrictive policy action but also create incident details for all matching profiles.
Which statement is correct in this scenario?
A company needs to block access to their instance of Microsoft 365 from unmanaged devices. They have configured Reverse Proxy and have also created a policy that blocks login activity for the AD group "marketing-users" for the Reverse Proxy access method. During UAT testing, they notice that access from unmanaged devices to Microsoft 365 is not blocked for marketing users.
What is causing this issue?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
