Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CCNP Security 350-701 Questions and answers with ExamsMirror
Exam 350-701 Premium Access
View all detail and faqs for the 350-701 exam
737 Students Passed
91% Average Score
91% Same Questions
What is the process In DevSecOps where all changes In the central code repository are merged and synchronized?
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?
Which two preventive measures are used to control cross-site scripting? (Choose two)
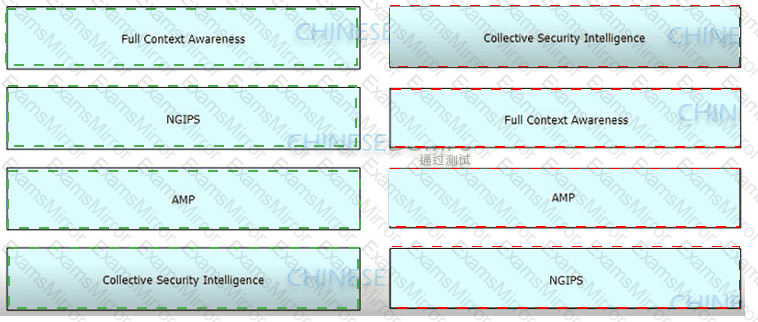
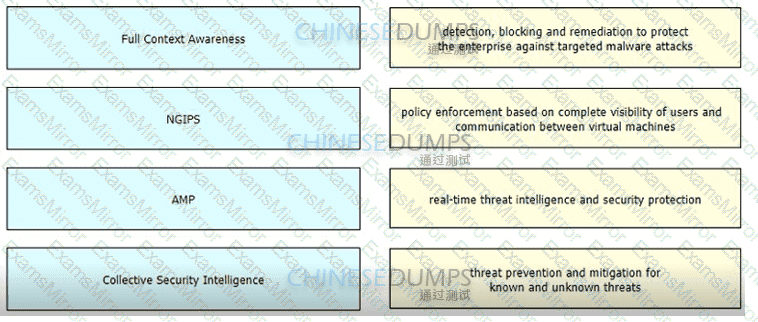
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.
Refer to the exhibit.
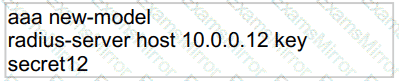
Which statement about the authentication protocol used in the configuration is true?
What provides visibility and awareness into what is currently occurring on the network?
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two)
For Cisco IOS PKI, which two types of Servers are used as a distribution point for CRLs? (Choose two)
What is a difference between GETVPN and IPsec?
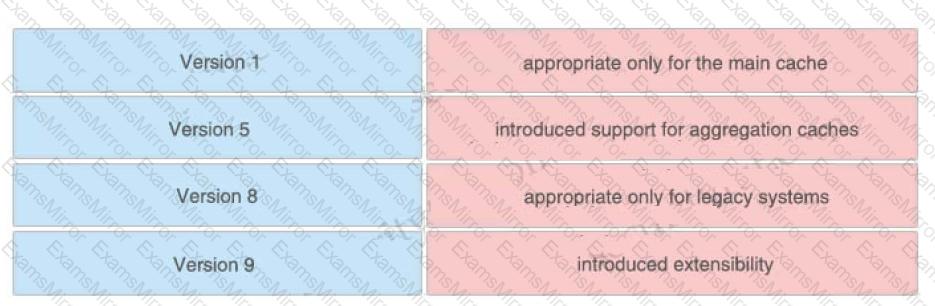
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements?
Which policy does a Cisco Secure Web Appliance use to block or monitor URL requests based on the reputation score?
What is a characteristic of Dynamic ARP Inspection?
What is a difference between an XSS attack and an SQL injection attack?
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.