Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Citrix CCE-N 1Y0-440 Questions and answers with ExamsMirror
Exam 1Y0-440 Premium Access
View all detail and faqs for the 1Y0-440 exam
753 Students Passed
94% Average Score
97% Same Questions
Which four settings can a Citrix Architect use to create a configuration job using Citrix Application Delivery Management? (Choose four.)
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for the Citrix ADC design project:
• The Citrix Gateway virtual server is integrated with the Citrix Virtual Apps and Desktops environment.
• The authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
• The workspacelab users connecting from the internal (workspacelab) network should be authenticated using LDAP.
• The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS
• The vendorlab users should be authenticated using Active Directory Federation Service.
• The user credentials must NOT be shared between workspacelab and vendor) ab.
• Single Sign-on must be performed between F and Citrix Gateway.
• A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server externally.
• The domain of the user connecting externally must be identified using the domain selected from the domain drop down.
At which bind point should the architect bind the domain drop-down schema policy?
Scenario: A Citrix Architect needs to design a new Citrix Gateway deployment for a customer. During the design discussions, the architect documents the key
requirements for the Citrix Gateway.
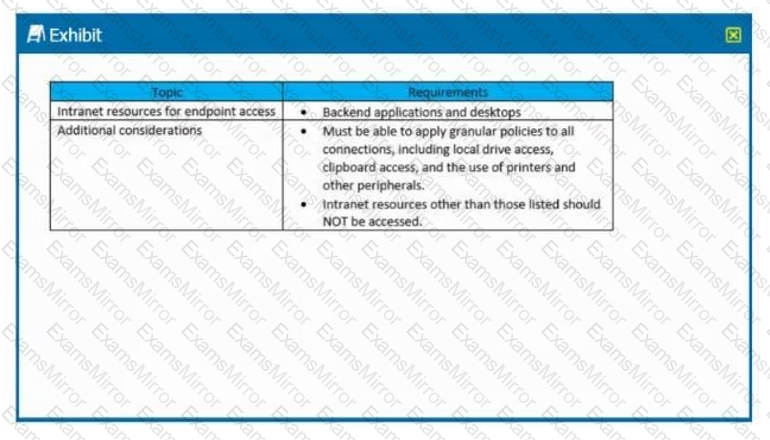
Click the Exhibit button to view the key requirements.
The architect should configure Citrix Gateway for __________________in order to meet the stated requirements. (Choose the correct option to complete the
sentence.)
Scenario: A Citrix Architect has deployed load balancing for SharePoint 2010 on a Citrix ADC instance. While editing the document, the architect observed the error displayed below:
Sorry, we couldn't open 'https://sharepointcs.emea.in/Shared Documents/Citrix Enhancement Request Form.doc'
After troubleshooting, the architect discovers the issue. When a user opens a document, it opens in the browser, but while editing the document, thd session is transferred from the browser to the Word application During this time, the cookies should be transferred from the browser to the Word application.
Which two configurations should the architect modify to ensure that the cookies are shared between the browser and non-browser applications? (Choose two.)
Which three session settings are valid once a Citrix Architect has configured session settings to customize user sessions? (Choose three.)
Scenario: A Citrix Architect needs to plan for a customer environment in which more than 10,000 users will need access. The networking infrastructure needs to be able to handle the expected usage.
Which business driver should be prioritized based on the customer’s requirement?
Scenario: A Citrix Architect needs to configure a full VPN session profile to meet the following requirements:
Users should be able to send the traffic only for the allowed networks through the VPN tunnel.
Only the DNS requests ending with the configured DNS suffix workspacelab.com must be sent to NetScaler Gateway.
If the DNS query does NOT contain a domain name, then DNS requests must be sent to NetScaler gateway.
Which settings will meet these requirements?
Which four parameters can a Citrix Architect change after the initial creation of a session profile? (Choose four.)
Scenario: A Citrix Architect has deployed two MPX devices, 12.0.53.13 nc and MPX 11500 models, in high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the NetScaler devices. Content Switching, SSL Offloading, Load Balancing, NetScaler Gateway, Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to NMAS 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration
All traffic should be secured and any traffic coming into HTTP should be redirected to HTTPS.
Single Sign-on should be created for Microsoft Outlook web access (OWA).
NetScaler should recognize Uniform Resource Identifier (URl) and close the session to NetScaler when users hit the Logoff button in Microsoft Outlook web access.
Users should be able to authenticate using either user principal name (UPN) or sAMAccountName.
The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL
Which monitor will meet these requirements?
Scenario: A Citrix Architect and a team of Workspacelab members met to discuss a NetScaler design project. They captured the following requirements from this design discussion:
A pair of NetScaler MPX appliances will be deployed in the DMZ network.
High Availability will be accessible in the NetScaler MPX in the DMZ Network.
Load balancing should be performed for the internal network services like Microsoft Exchange Client Access Services and Microsoft App-V.
The load balancing should be performed for StoreFront.
The NetScaler Gateway virtual server will be utilizing the StoreFront load-balancing virtual server.
The NetScaler Gateway virtual server and StoreFront.
The NetScaler Gateway virtual service and StoreFront and load-balancing services are publicly accessible.
The traffic for internal and external services must be isolated.
Click the Exhibit button to review the logical network diagram.
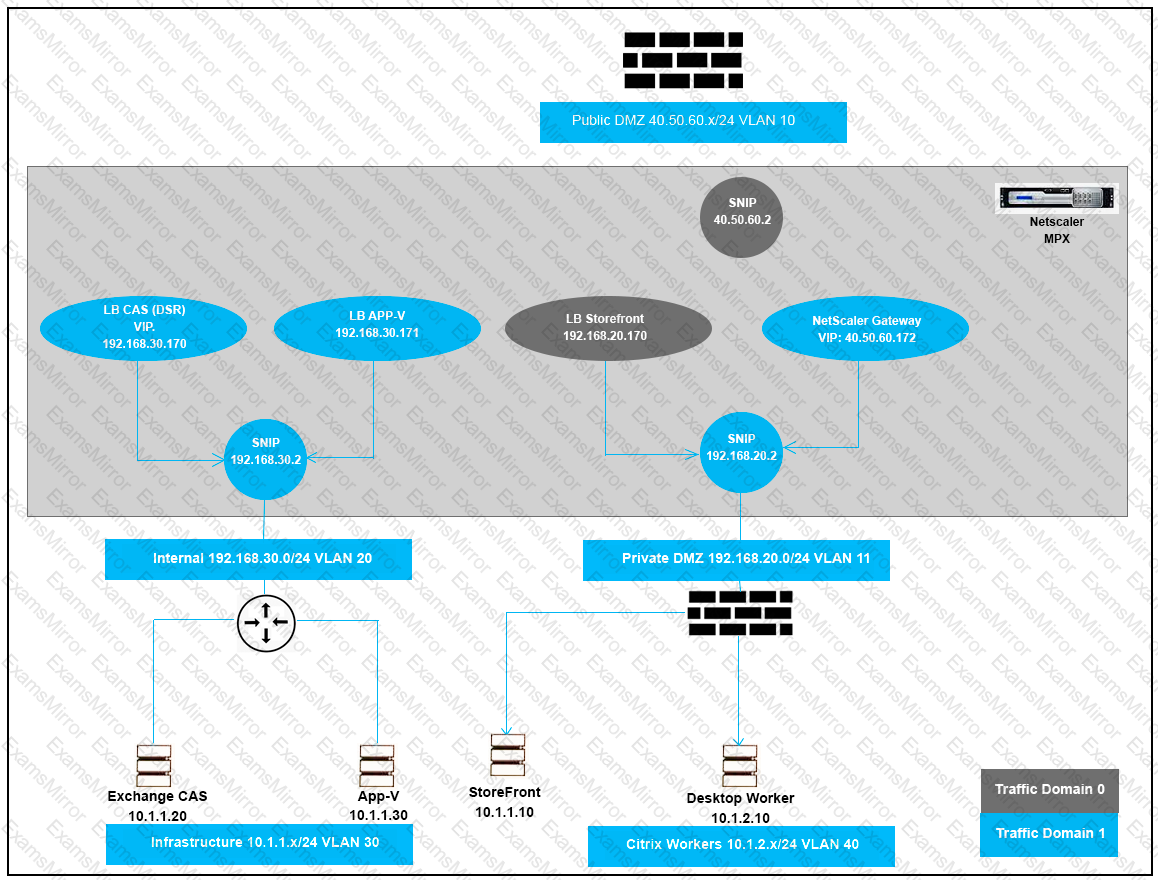
Which two design decisions are incorrect based on these requirements? (Choose two.)
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
