Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Audit GSNA GSNA Questions and answers with ExamsMirror
Exam GSNA Premium Access
View all detail and faqs for the GSNA exam
659 Students Passed
86% Average Score
96% Same Questions
You work as a Network Administrator for Infosec Inc. Nowadays, you are facing an unauthorized access in your Wi-Fi network. Therefore, you analyze a log that has been recorded by your favorite sniffer, Ethereal. You are able to discover the cause of the unauthorized access after noticing the following string in the log file: (Wlan.fc.type_subtype eq 32 and llc.oui eq 0x00601d and llc.pid eq 0x0001) When you find All your 802.11b are belong to us as the payload string, you are convinced about which tool is being used for the unauthorized access. Which of the following tools have you ascertained?
Which of the following is the most secure place to host a server that will be accessed publicly through the Internet?
In which of the following techniques does an attacker take network traffic coming towards a host at one port and forward it from that host to another host?
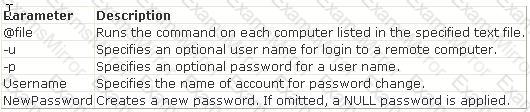
You work as a Network Analyst for XYZ CORP. The company has a Unix-based network. You want to view the directories in alphabetical order. Which of the following Unix commands will you use to accomplish the task?
Which of the following tools monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools?
You want to append a tar file if the on-disk version of the tar file has a modification date more recent than its copy in the tar archive. Which of the following commands will you use to accomplish the task?
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement? (Choose two)
You work as a Network Architect for Tech Perfect Inc. The company has a TCP/IP based Enterprise network. The company uses Cisco IOS technologies in the Enterprise network. You have enabled system message logging (syslog) service on all the routers that are currently working in the network. The syslog service provides all the reports, and important error and notification messages. You want to store all the reports and messages. Choose the locations where you can store all of these.
Sam works as a Network Administrator for XYZ CORP. The computers in the company run Windows Vista operating system, and they are continuously connected to the Internet. This makes the network of the company susceptible to attacks from unauthorized users. Which of the following will Sam choose to protect the network of the company from such attacks?
Which of the following evidences are the collection of facts that, when considered together, can be used to infer a conclusion about the malicious activity/person?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
